Juniper JN0-636 Security,Professional (JNCIP-SEC) Online Training
Juniper JN0-636 Online Training
The questions for JN0-636 were last updated at Feb 26,2026.
- Exam Code: JN0-636
- Exam Name: Security,Professional (JNCIP-SEC)
- Certification Provider: Juniper
- Latest update: Feb 26,2026
Exhibit
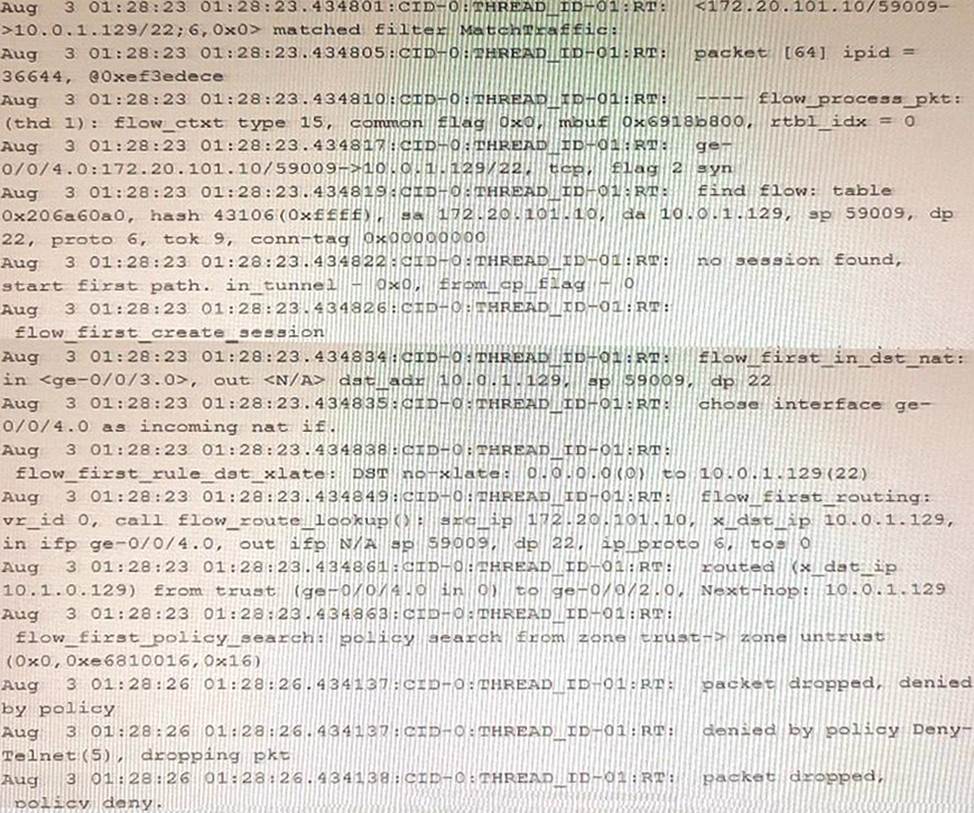
Referring to the exhibit, which statement is true?
- A . This custom block list feed will be used before the Juniper Seclntel
- B . This custom block list feed cannot be saved if the Juniper Seclntel block list feed is configured.
- C . This custom block list feed will be used instead of the Juniper Seclntel block list feed
- D . This custom block list feed will be used after the Juniper Seclntel block list feed.
Exhibit
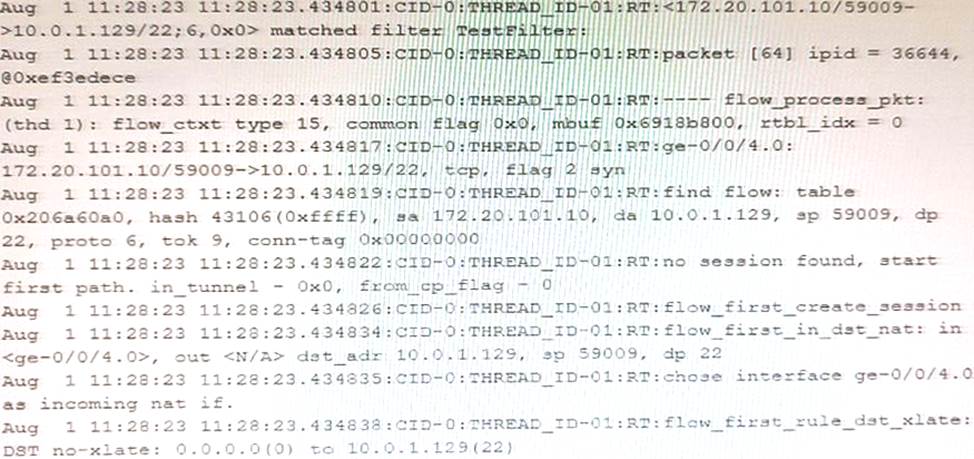
The exhibit shows a snippet of a security flow trace.
In this scenario, which two statements are correct? (Choose two.)
- A . This packet arrived on interface ge-0/0/4.0.
- B . Destination NAT occurs.
- C . The capture is a packet from the source address 172.20.101.10 destined to 10.0.1.129.
- D . An existing session is found in the table.
Regarding IPsec CoS-based VPNs, what is the number of IPsec SAs associated with a peer based upon?
- A . The number of traffic selectors configured for the VPN.
- B . The number of CoS queues configured for the VPN.
- C . The number of classifiers configured for the VPN.
- D . The number of forwarding classes configured for the VPN.
Exhibit
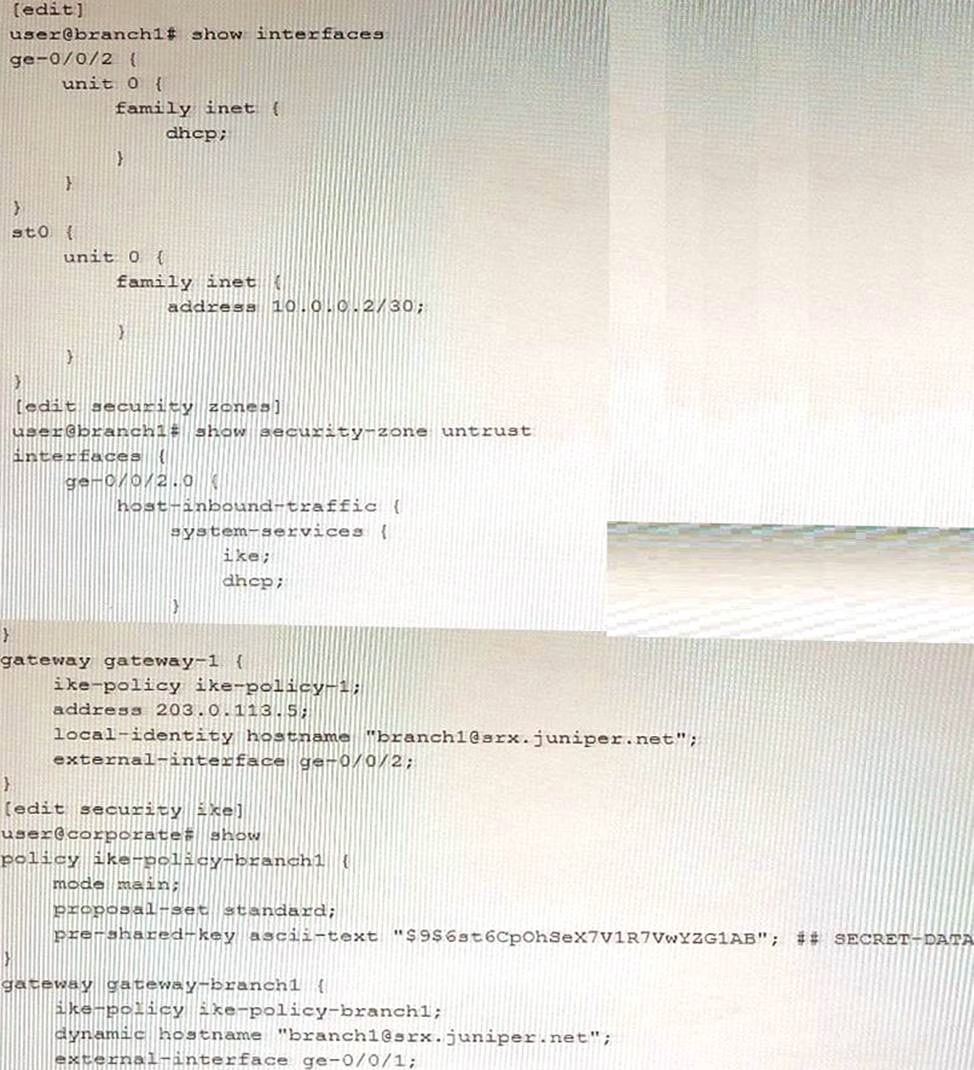
You are trying to configure an IPsec tunnel between SRX Series devices in the corporate office and branch1. You have committed the configuration shown in the exhibit, but the IPsec tunnel is not establishing.
In this scenario, what would solve this problem.
- A . Add multipoint to the st0.0 interface configuration on the branch1 device.
- B . Change the IKE proposal-set to compatible on the branch1 and corporate devices.
- C . Change the local identity to inet advpn on the branch1 device.
- D . Change the IKE mode to aggressive on the branch1 and corporate devices.
You want to configure a threat prevention policy.
Which three profiles are configurable in this scenario? (Choose three.)
- A . device profile
- B . SSL proxy profile
- C . infected host profile
- D . C&C profile
- E . malware profile
You are asked to detect domain generation algorithms
Which two steps will accomplish this goal on an SRX Series firewall? (Choose two.)
- A . Define an advanced-anti-malware policy under [edit services].
- B . Attach the security-metadata-streaming policy to a security
- C . Define a security-metadata-streaming policy under [edit
- D . Attach the advanced-anti-malware policy to a security policy.
You are deploying a virtualization solution with the security devices in your network Each SRX Series device must support at least 100 virtualized instances and each virtualized instance must have its own discrete administrative domain.
In this scenario, which solution would you choose?
- A . VRF instances
- B . virtual router instances
- C . logical systems
- D . tenant systems
Exhibit

You configure Source NAT using a pool of addresses that are in the same subnet range as the external ge-0/0/0 interface on your vSRX device. Traffic that is exiting the internal network can reach external destinations, but the return traffic is being dropped by the service provider router.
Referring to the exhibit, what must be enabled on the vSRX device to solve this problem?
- A . STUN
- B . Proxy ARP
- C . Persistent NAT
- D . DNS Doctoring
Exhibit
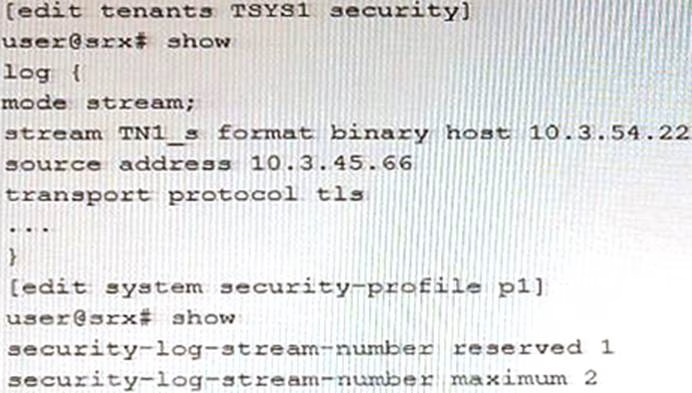
An administrator wants to configure an SRX Series device to log binary security events for tenant systems.
Referring to the exhibit, which statement would complete the configuration?
- A . Configure the tenant as TSYS1 for the pi security profile.
- B . Configure the tenant as root for the pi security profile.
- C . Configure the tenant as master for the pi security profile.
- D . Configure the tenant as local for the pi security profile
Your company wants to use the Juniper Seclntel feeds to block access to known command and control servers, but they do not want to use Security Director to manage the feeds.
Which two Juniper devices work in this situation? (Choose two)
- A . EX Series devices
- B . MX Series devices
- C . SRX Series devices
- D . QFX Series devices
Latest JN0-636 Dumps Valid Version with 65 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund

