Juniper JN0-635 Security, Professional Online Training
Juniper JN0-635 Online Training
The questions for JN0-635 were last updated at Feb 21,2026.
- Exam Code: JN0-635
- Exam Name: Security, Professional
- Certification Provider: Juniper
- Latest update: Feb 21,2026
You have noticed a high number of TCP-based attacks directed toward your primary edge device. You are asked to configure the IDP feature on your SRX Series device to block this attack.
Which two IDP attack objects would you configure to solve this problem? (Choose two.)
- A . Network
- B . Signature
- C . Protocol anomaly
- D . host
Click the Exhibit button.
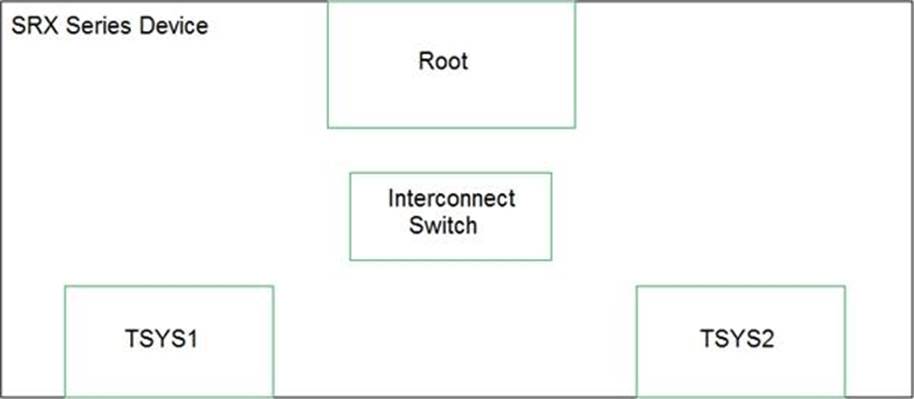
You have configured tenant systems on your SRX Series device.
Referring to the exhibit, which two actions should you take to facilitate inter-TSYS communication? (Choose two.)
- A . Place the logical tunnel interfaces in a virtual router routing instance in the interconnect switch
- B . Place the logical tunnel interfaces in a VPLS routing instance in the interconnect switch
- C . Connect each TSYS with the interconnect switch by configuring INET configured logical tunnel interfaces in the interconnect switch
- D . Connect each TSYS with the interconnect switch by configuring Ethernet VPLS configured logical tunnel interfaces in the interconnect switch
Click the Exhibit button.
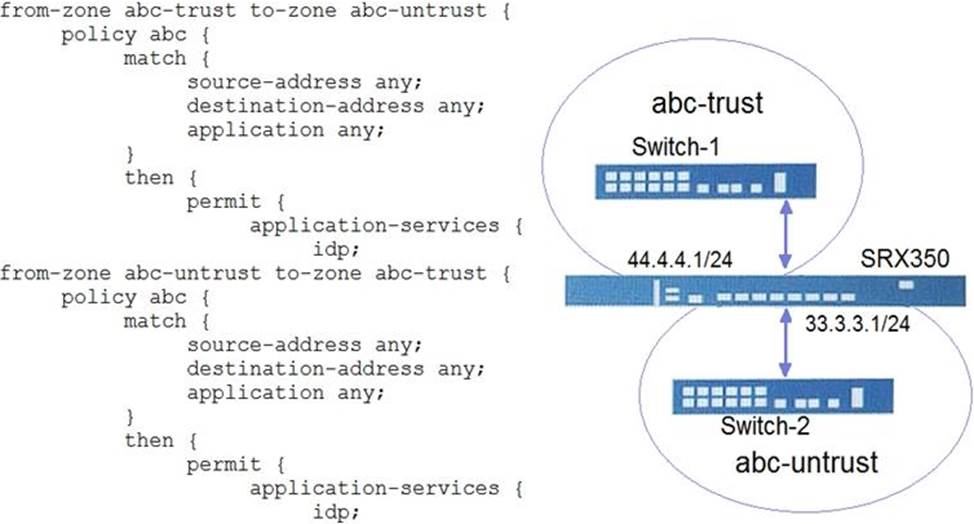
Referring to the exhibit, which three types of traffic would be examined by the IPS policy between Switch-1 and Switch-2? (Choose three.)
- A . TCP
- B . LLDP
- C . ARP
- D . ICMP
- E . UDP
Click the Exhibit button.
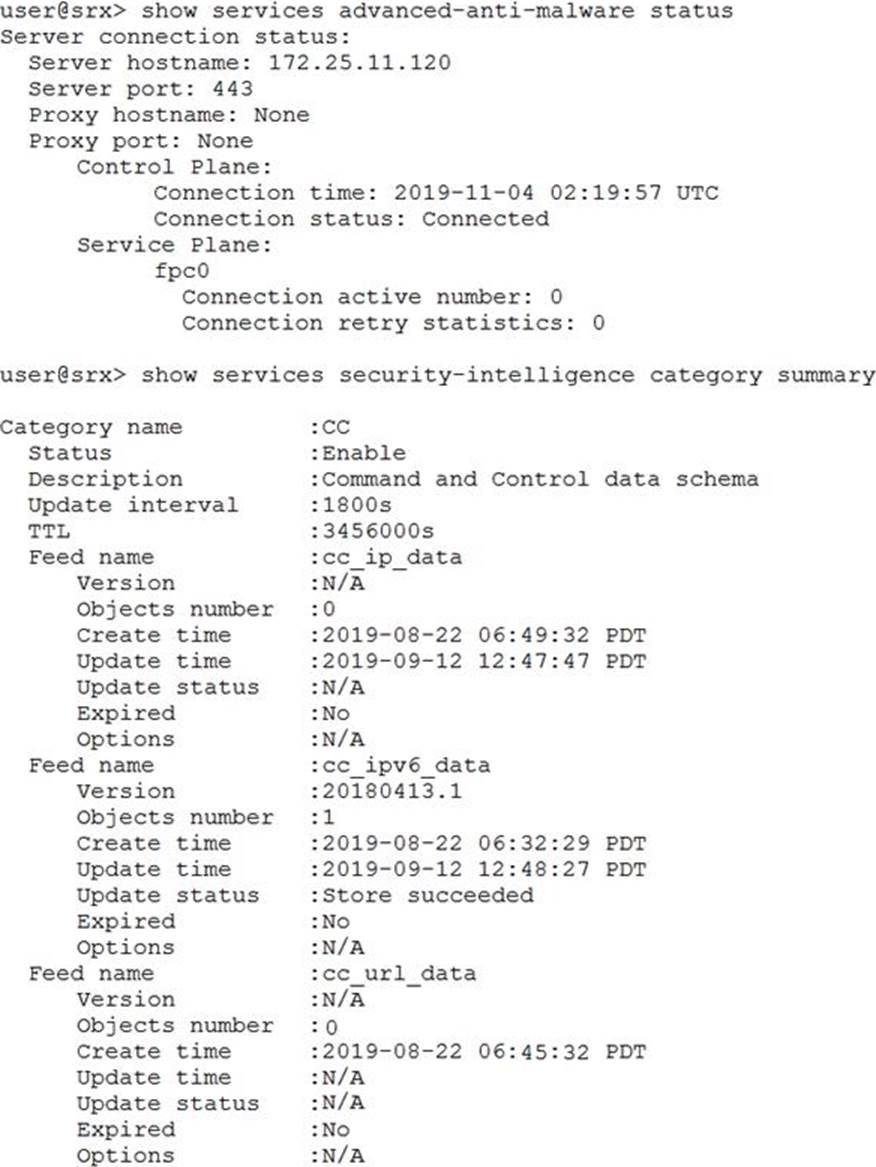
Referring to the exhibit, which two statements are true? (Choose two.)
- A . The SRX Series device is enrolled and communicating with a JATP Appliance
- B . The JATP Appliance cannot download the security feeds from the GSS servers
- C . The SRX Series device cannot download the security feeds from the JATP Appliance
- D . The SRX Series device is not enrolled but can communicate with the JATP Appliance
You have configured three logical tunnel interfaces in a tenant system on an SRX1500 device. When committing the configuration, the commit fails.
In this scenario, what would cause this problem?
- A . There is no GRE tunnel between the tenant system and master system allowing SSH traffic
- B . There is no VPLS switch on the tenant system containing a peer It-0/0/0 interface
- C . The SRX1500 device does not support more than two logical interfaces per tenant system
- D . The SRX1500 device requires a tunnel PIC to allow for logical tunnel interfaces
Click the Exhibit button.

Referring to the exhibit, which two statements are true? (Choose two.)
- A . You can secure intra-VLAN traffic with a security policy on this device
- B . You can secure inter-VLAN traffic with a security policy on this device
- C . The device can pass Layer 2 and Layer 3 traffic at the same time
- D . The device cannot pass Layer 2 and Layer 3 traffic at the same time
You are asked to configure an SRX Series device to bypass all security features for IP traffic from the engineering department.
Which firewall filter will accomplish this task?
A)
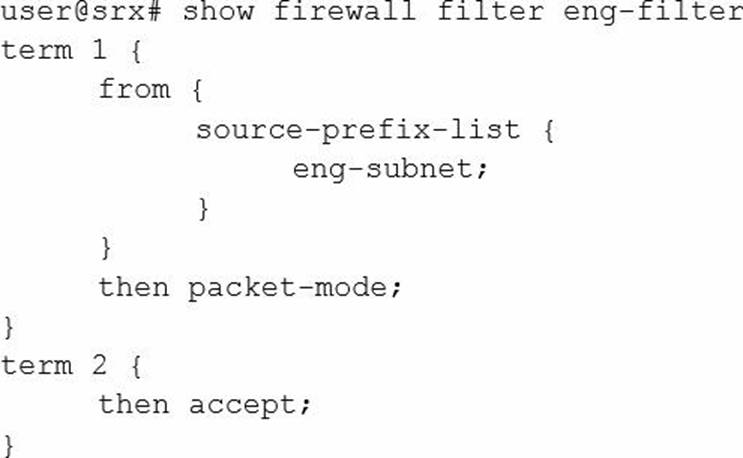
B)
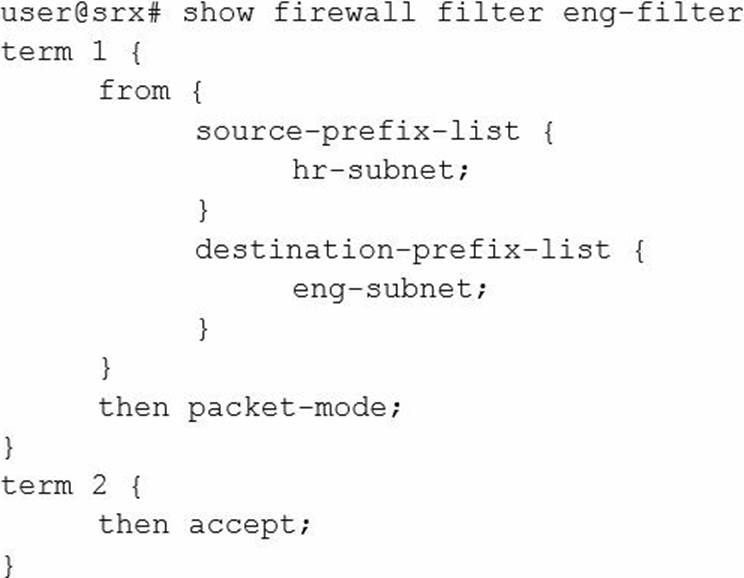
C)
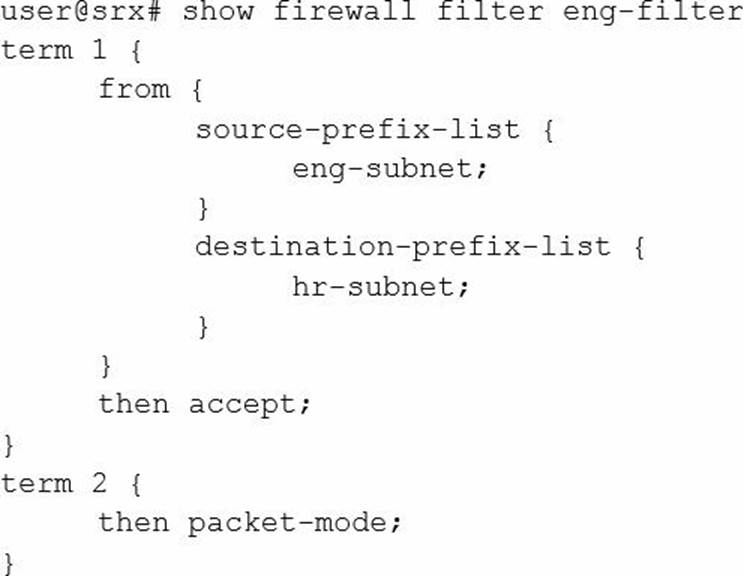
D)
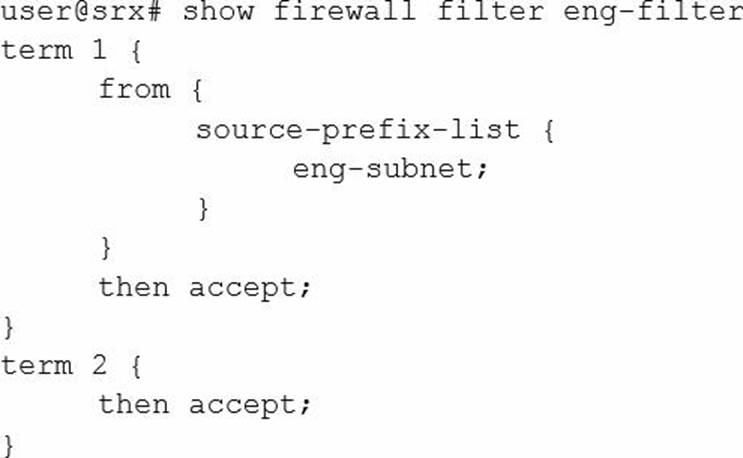
- A . Option A
- B . Option B
- C . Option C
- D . Option D
Click the Exhibit button.
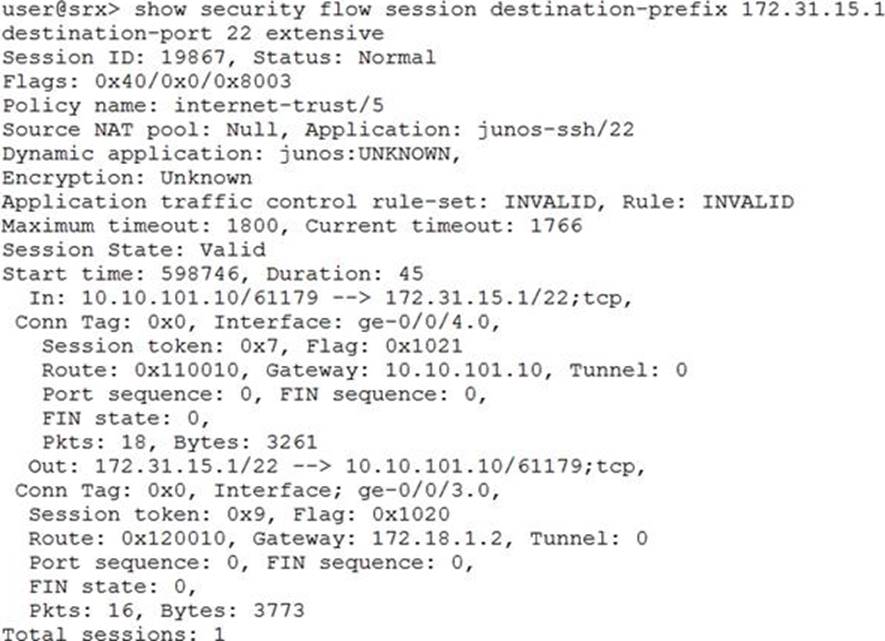
Given the command output shown in the exhibit, which two statements are true? (Choose two.)
- A . The host 172.31.15.1 is directly connected to interface ge-0/0/3.0
- B . Traffic matching this session has been received since the session was established
- C . The host 10.10.101.10 is directly connected to interface ge-0/0/4.0
- D . Network Address Translation is applied to this session
A user is unable to reach a necessary resource. You discover the path through the SRX Series device includes several security features. The traffic is not being evaluated by any security policies.
In this scenario, which two components within the flow module would affect the traffic? (Choose two.)
- A . services/ALG
- B . destination NAT
- C . source NAT
- D . route lookup
Click the Exhibit button.
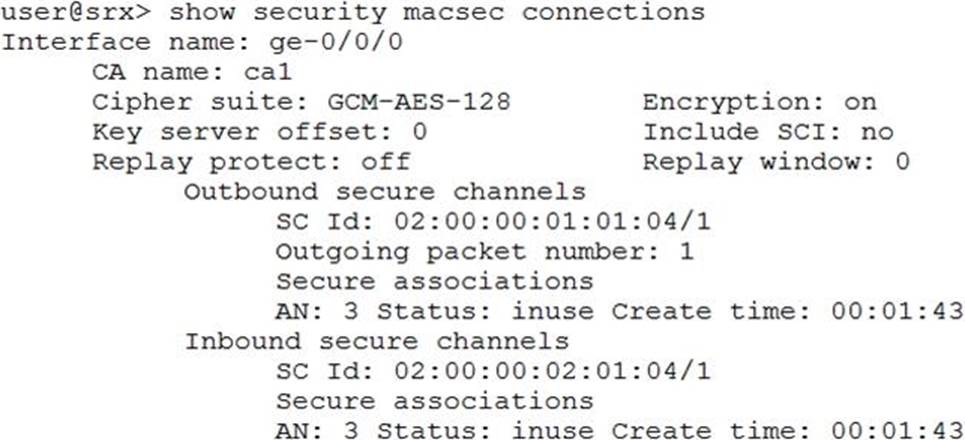
Referring to the exhibit, which two statements are true? (Choose two.)
- A . Data is transmitted across the link in plaintext
- B . The link is not protected against man-in-the-middle attacks
- C . The link is protected against man-in-the-middle attacks
- D . Data is transmitted across the link in cyphertext
Latest JN0-635 Dumps Valid Version with 88 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund


Document very useful for whom tranning exam