Juniper JN0-634 Security, Professional (JNCIP-SEC) Online Training
Juniper JN0-634 Online Training
The questions for JN0-634 were last updated at Mar 01,2026.
- Exam Code: JN0-634
- Exam Name: Security, Professional (JNCIP-SEC)
- Certification Provider: Juniper
- Latest update: Mar 01,2026
You are creating an IPS policy with multiple rules. You want traffic that matches rule 5 to silently be dropped, along with any future packets that match the appropriate attributes of the incoming traffic.
In this scenario, which ip-action parameter should you use?
- A . ip-block
- B . ip-close
- C . log-create
- D . timeout
Click the Exhibit button.
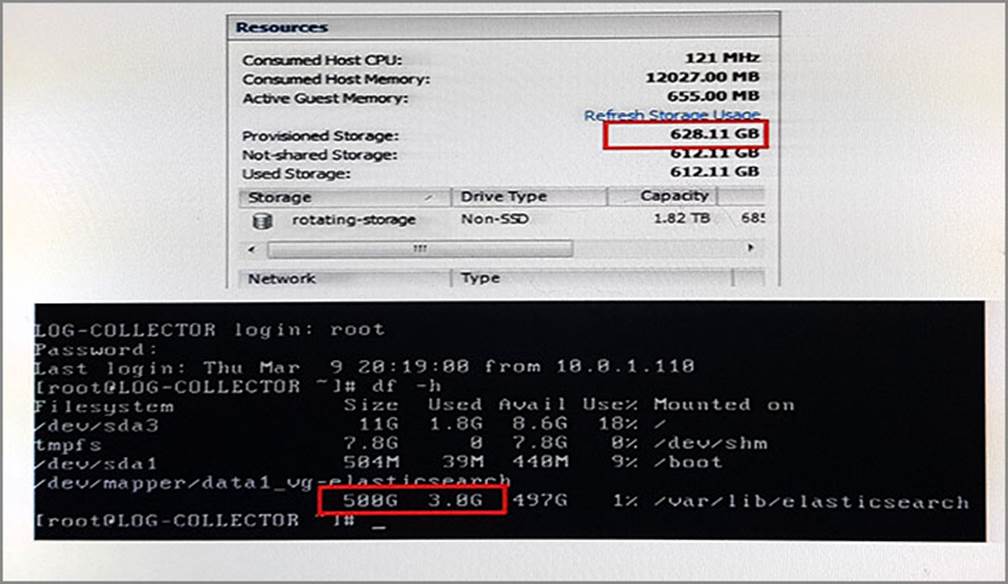
Referring to the exhibit, you have expanded the disk storage size in ESXi for your log collector from 500 GB to 600 GB. However, your log collector’s disk size has not changed.
Given the scenario, which two statements are true? (Choose two.)
- A . You must run a script from the console to expand the disk size.
- B . The ESXi storage parameter is not associated with the Elasticsearch disk size parameter.
- C . You must reboot the log collector for storage settings to be updated
- D . You must re-run the log collector setup script to update the storage settings.
Click the Exhibit button.
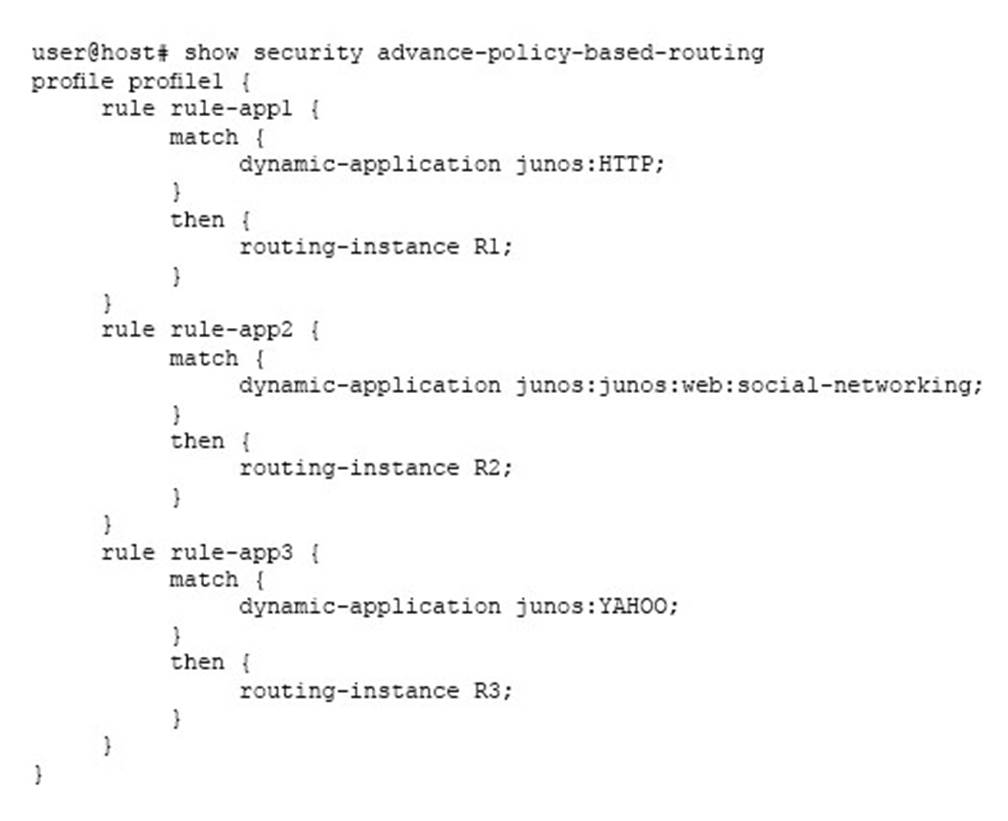
Your organization requests that you direct Facebook traffic out a different link to ensure that the bandwidth for critical applications is protected.
Referring to the exhibit, which forwarding instance will be used on your SRX Series device?
- A . R3
- B . R1
- C . R2
- D . inet.0
Click the Exhibit button.
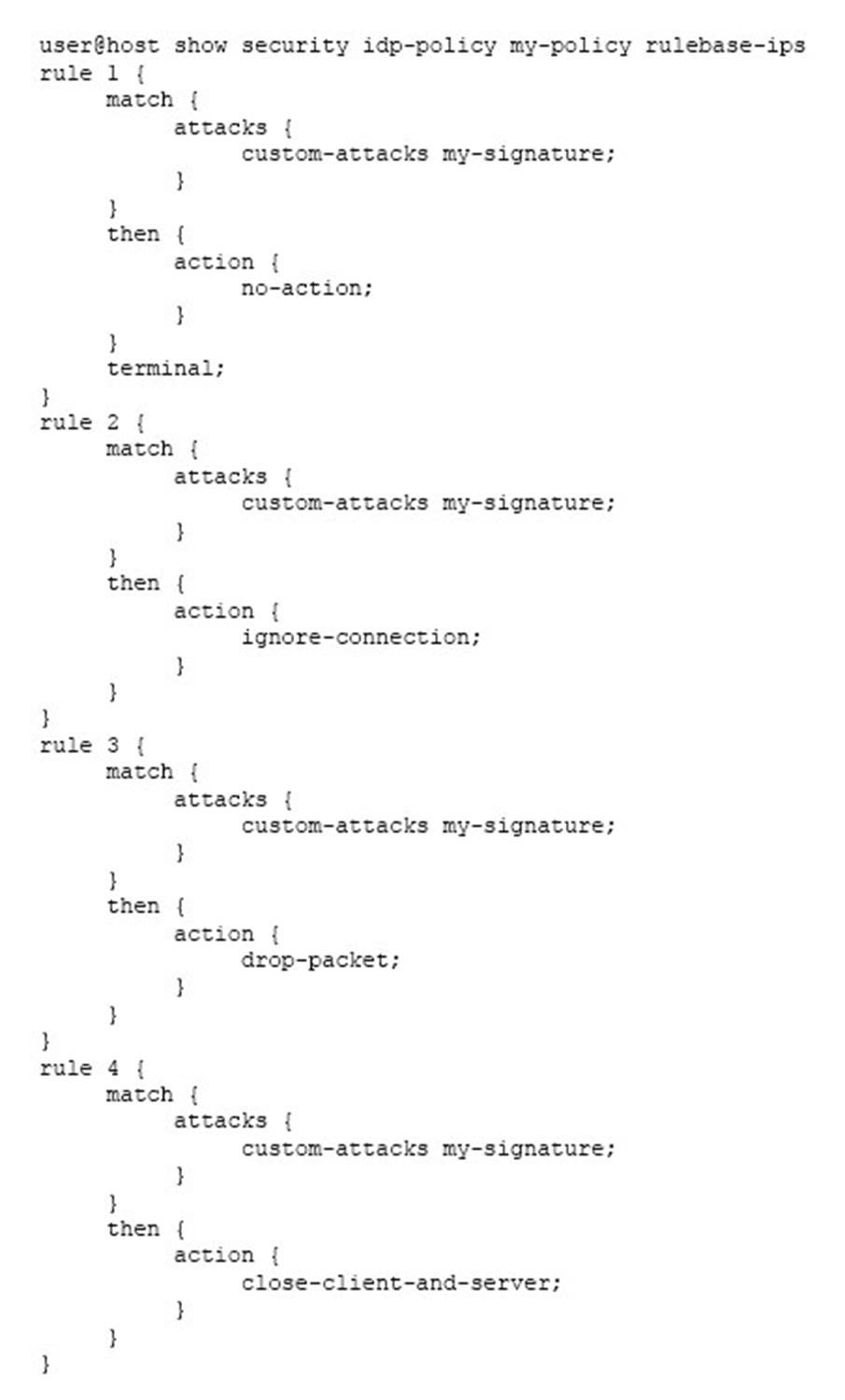
You have recently committed the IPS policy shown in the exhibit. When evaluating the expected behavior, you notice that you have a session that matches all of the rules in your IPS policy.
In this scenario, which action would be taken?
- A . ignore-connection
- B . drop packet
- C . no-action
- D . close-client-and-server
What is the required when deploying a log collector in Junos Space?
- A . root user access to the log collector
- B . a shared log file directory on the log collector
- C . the IP address of interface eth1 on the log collector
- D . a distributed deployment of the log collector nodes
Click the Exhibit button.
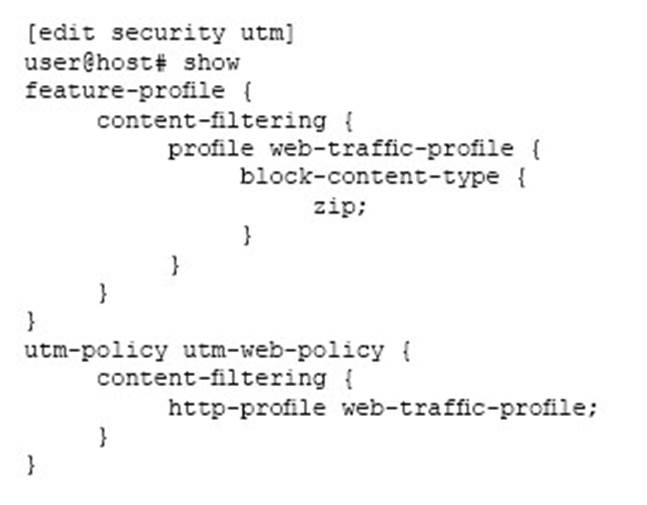
The UTM policy shown in the exhibit has been applied to a security policy on a branch SRX Series device.
In this scenario, which statement is true?
- A . HTTP downloads of ZIP files will be blocked.
- B . FTP downloads of ZIP files will be blocked.
- C . E-mail downloads of ZIP files will be blocked.
- D . ZIP files can be renamed with a new extension to pass through the filter.

