Juniper JN0-634 Security, Professional (JNCIP-SEC) Online Training
Juniper JN0-634 Online Training
The questions for JN0-634 were last updated at Feb 26,2026.
- Exam Code: JN0-634
- Exam Name: Security, Professional (JNCIP-SEC)
- Certification Provider: Juniper
- Latest update: Feb 26,2026
Which Junos security feature is used for signature-based attack prevention?
- A . RADIUS
- B . AppQoS
- C . IPS
- D . PIM
Using content filtering on an SRX Series device, which three types of HTTP content are able to be blocked? (Choose three.)
- A . PDF files
- B . ZIP files
- C . Java applets
- D . Active X
- E . Flash
After using Security Director to add a new firewall policy rule on an SRX Series device, you notice that the hit count on the policy is not increasing. Upon further investigation, you find that the devices listed in the new rule are able to communicate as expected. Your firewall policy consists of hundreds of rules.
Using only Security Director, how do you find the rule that is allowing the communication to occur in this scenario?
- A . Generate a Top Firewall Rules report.
- B . Generate a Policy Analysis report.
- C . Generate a Top Source IPs report.
- D . Generate a Top Firewall Events report.
Your network includes SRX Series devices at the headquarters location. The SRX Series devices at this location are part of a high availability chassis cluster and are configured for IPS. There has been a node failover.
In this scenario, which statement is true?
- A . Existing sessions continue to be processed by IPS because of table synchronization.
- B . Existing sessions are no longer processed by IPS and become firewall sessions.
- C . Existing session continue to be processed by IPS as long as GRES is configured.
- D . Existing sessions are dropped and must be reestablished so IPS processing can occur.
You are scanning files that are being transferred from the Internet to hosts on your internal network with Sky ATP. However, you notice that files that are 1 GB in size are not being scanned by Sky ATP.
In this scenario, which two statements are true? (Choose two.)
- A . The Sky ATP failback option is set to permit.
- B . The Sky ATP engine or the SRX Series device is too busy.
- C . The 1 GB file size is larger than the scan size limit for Sky ATP.
- D . The Sky ATP policy on the SRX Series device is misconfigured.
Click the Exhibit button.
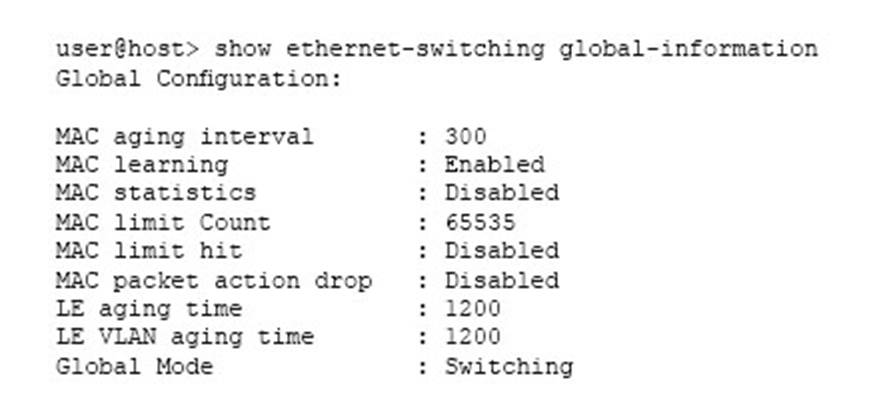
Referring to the exhibit, which two statements are true? (Choose two.)
- A . You can secure inter-VLAN traffic with a security policy on this device.
- B . You can secure intra-VLAN traffic with a security policy on this device.
- C . The device can pass Layer 2 and Layer 3 traffic at the same time.
- D . The device cannot pass Layer 2 and Layer 3 traffic at the same time.
Click the Exhibit button.
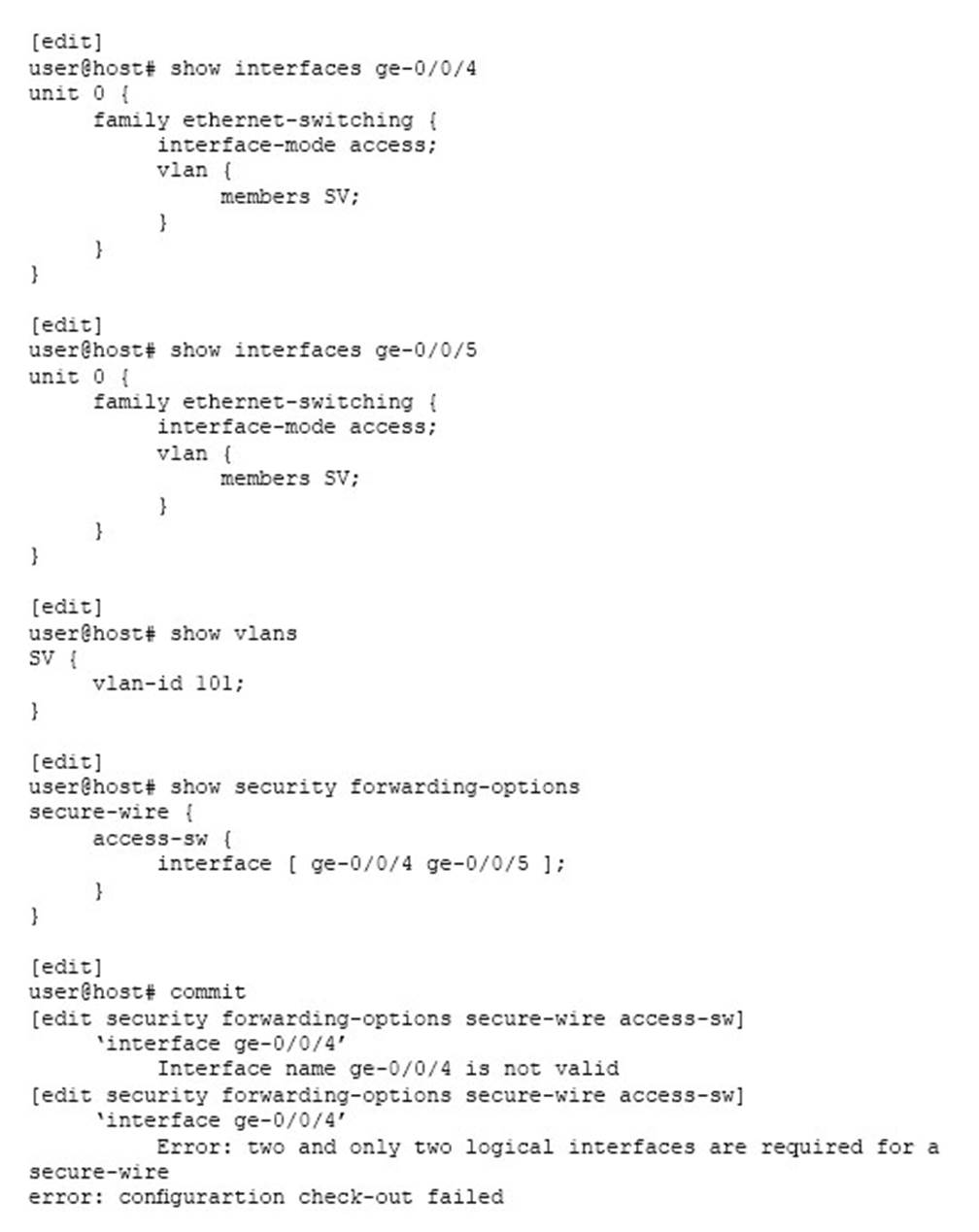
You are trying to implement secure wire on your SRX Series device. However, you are receiving the commit error shown in the exhibit.
What must you do to solve the problem?
- A . Add the correct logical units to the interfaces in the secure wire.
- B . Put the ge-0/0/4 and ge-0/0/5 interfaces in separate secure wires.
- C . Change the Ethernet switching mode from access to trunk for the ge-0/0/4 and ge-0/0/5 interfaces.
- D . Add the ge-0/0/4 and ge-0/0/5 interfaces to the SV VLAN.
You want to review AppTrack statistics to determine the characteristics of the traffic being monitored.
Which operational mode command would accomplish this task on an SRX Series device?
- A . show services application-identification statistics applications
- B . show services application-identification application detail
- C . show security application-tracking counters
- D . show services security-intelligence statistics
Which AppSecure feature identifies applications that are present in traffic?
- A . AppID
- B . AppTrack
- C . AppFW
- D . AppQoS
What is the correct application mapping sequence when a user goes to Facebook for the first time through an SRX Series device?
- A . first packet > process packet > check application system cache > classify application > process packet > match and identify application
- B . first packet > check application system cache > process packet > classify application > match and identify application
- C . first packet > check application system cache > classify application > process packet > match and identify application
- D . first packet > process packet > check application system cache > classify application > match and identify application

