Juniper JN0-335 Security, Specialist (JNCIS-SEC) Online Training
Juniper JN0-335 Online Training
The questions for JN0-335 were last updated at Apr 07,2025.
- Exam Code: JN0-335
- Exam Name: Security, Specialist (JNCIS-SEC)
- Certification Provider: Juniper
- Latest update: Apr 07,2025
After JSA receives external events and flows, which two steps occur? (Choose two.)
- A . After formatting the data, the data is stored in an asset database.
- B . Before formatting the data, the data is analyzed for relevant information.
- C . Before the information is filtered, the information is formatted
- D . After the information is filtered, JSA responds with active measures
Your company is using the Juniper ATP Cloud free model. The current inspection profile is set at 10 MB You are asked to configure ATP Cloud so that executable files up to 30 MB can be scanned while at the same time minimizing the change in scan time for other file types.
Which configuration should you use in this scenario?
- A . Use the CLI to create a custom profile and increase the scan limit.
- B . Use the ATP Cloud Ul to change the default profile to increase the scan limit for all files to 30 MB.
- C . Use the CLI to change the default profile to increase the scan limit for all files to 30 MB.
- D . Use the ATP Cloud Ul to update a custom profile and increase the scan limit for executable files to 30 MB.
What are two benefits of using a vSRX in a software-defined network? (Choose two.)
- A . scalability
- B . no required software license
- C . granular security
- D . infinite number of interfaces
You enable chassis clustering on two devices and assign a cluster ID and a node ID to each device.
In this scenario, what is the correct order for rebooting the devices?
- A . Reboot the secondary device, then the primary device.
- B . Reboot only the secondary device since the primary will assign itself the correct cluster and node ID.
- C . Reboot the primary device, then the secondary device.
- D . Reboot only the primary device since the secondary will assign itself the correct cluster and node ID.
Exhibit
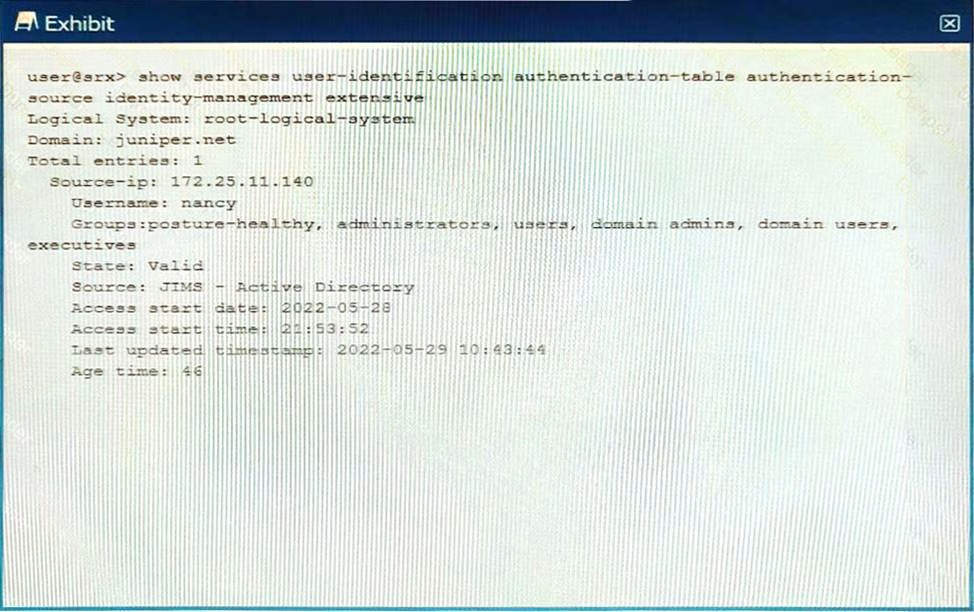
Referring to the exhibit, which two statements are true? (Choose two.)
- A . Nancy logged in to the juniper.net Active Directory domain.
- B . The IP address of Nancy’s client PC is 172.25.11.
- C . The IP address of the authenticating domain controller is 172.25.11.140.
- D . Nancy is a member of the Active Directory sales group.
Which three statements about SRX Series device chassis clusters are true? (Choose three.)
- A . Chassis cluster control links must be configured using RFC 1918 IP addresses.
- B . Chassis cluster member devices synchronize configuration using the control link.
- C . A control link failure causes the secondary cluster node to be disabled.
- D . Recovery from a control link failure requires that the secondary member device be rebooted.
- E . Heartbeat messages verify that the chassis cluster control link is working.
Which two devices would you use for DDoS protection with Policy Enforcer? (Choose two.)
- A . vQFX
- B . MX
- C . vMX
- D . QFX
You have implemented a vSRX in your VMware environment. You want to implement a second vSRX Series device and enable chassis clustering.
Which two statements are correct in this scenario about the control-link settings? (Choose two.)
- A . In the vSwitch security settings, accept promiscuous mode.
- B . In the vSwitch properties settings, set the VLAN ID to None.
- C . In the vSwitch security settings, reject forged transmits.
- D . In the vSwitch security settings, reject MAC address changes.
Which two statements are true about the fab interface in a chassis cluster? (Choose two.)
- A . The fab link does not support fragmentation.
- B . The physical interface for the fab link must be specified in the configuration.
- C . The fab link supports traditional interface features.
- D . The Junos OS supports only one fab link.
You want to manually failover the primary Routing Engine in an SRX Series high availability cluster pair.
Which step is necessary to accomplish this task?
- A . Issue the set chassis cluster disable reboot command on the primary node.
- B . Implement the control link recover/ solution before adjusting the priorities.
- C . Manually request the failover and identify the secondary node
- D . Adjust the priority in the configuration on the secondary node.
Latest JN0-335 Dumps Valid Version with 91 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund

