Juniper JN0-335 Security, Specialist (JNCIS-SEC) Online Training
Juniper JN0-335 Online Training
The questions for JN0-335 were last updated at Mar 01,2026.
- Exam Code: JN0-335
- Exam Name: Security, Specialist (JNCIS-SEC)
- Certification Provider: Juniper
- Latest update: Mar 01,2026
A client has attempted communication with a known command-and-control server and it has reached the configured threat level threshold.
Which feed will the clients IP address be automatically added to in this situation?
- A . the command-and-control cloud feed
- B . the allowlist and blocklist feed
- C . the custom cloud feed
- D . the infected host cloud feed
Exhibit
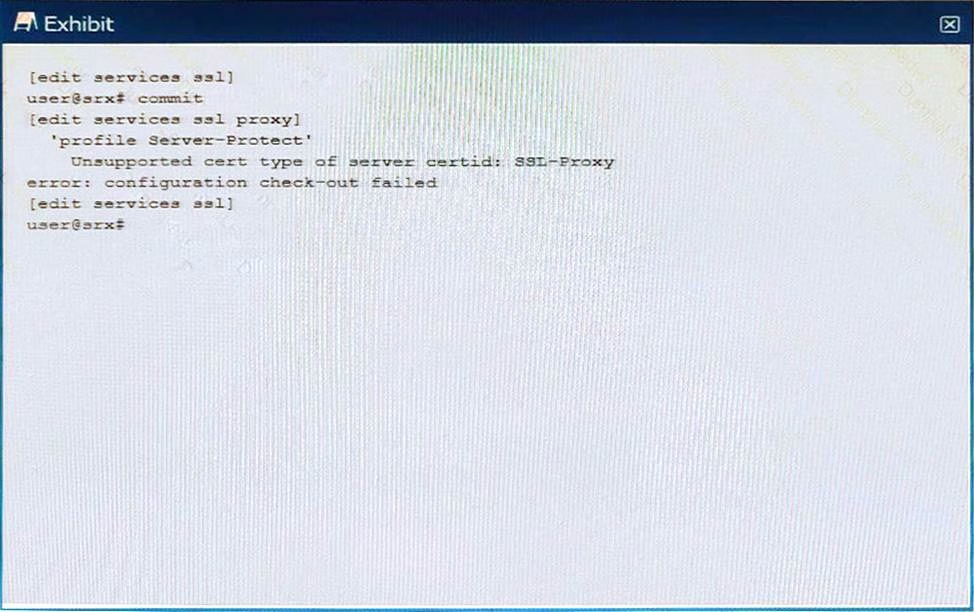
When trying to set up a server protection SSL proxy, you receive the error shown.
What are two reasons for this error? (Choose two.)
- A . The SSL proxy certificate ID is part of a blocklist.
- B . The SSL proxy certificate ID does not have the correct renegotiation option set.
- C . The SSL proxy certificate ID is for a forwarding proxy.
- D . The SSL proxy certificate ID does not exist.
You are asked to reduce the load that the JIMS server places on your
Which action should you take in this situation?
- A . Connect JIMS to the RADIUS server
- B . Connect JIMS to the domain Exchange server
- C . Connect JIMS to the domain SQL server.
- D . Connect JIMS to another SRX Series device.
Exhibit
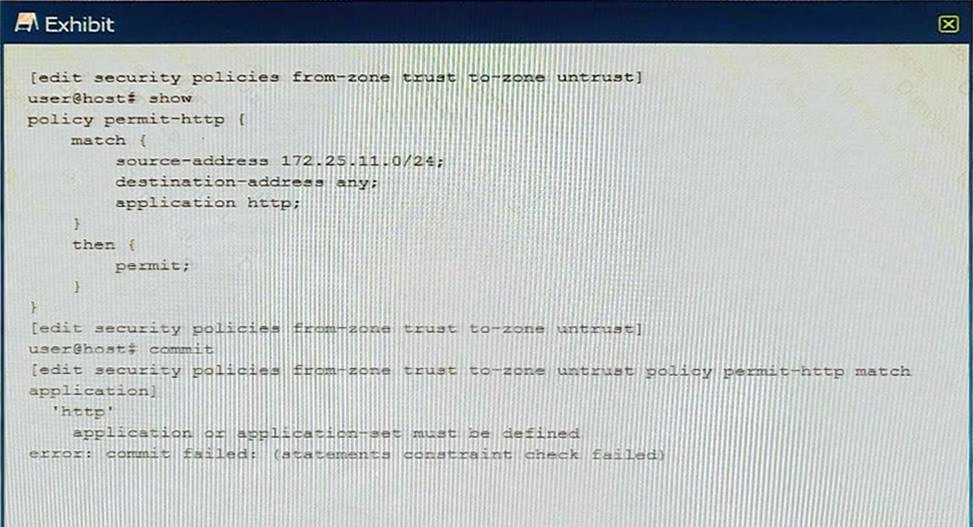
You are trying to create a security policy on your SRX Series device that permits HTTP traffic from your private 172 25.11.0/24 subnet to the Internet You create a policy named permit-http between the trust and untrust zones that permits HTTP traffic. When you issue a commit command to apply the configuration changes, the commit fails with the error shown in the exhibit.
Which two actions would correct the error? (Choose two.)
- A . Issue the rollback 1 command from the top of the configuration hierarchy and attempt the commit again.
- B . Execute the Junos commit full command to override the error and apply the configuration.
- C . Create a custom application named http at the [edit applications] hierarchy.
- D . Modify the security policy to use the built-in Junos-http applications.
What are two types of system logs that Junos generates? (Choose two.)
- A . SQL log files
- B . data plane logs
- C . system core dump files
- D . control plane logs
You are asked to ensure that if the session table on your SRX Series device gets close to exhausting its resources, that you enforce a more aggress.ve age-out of existing flows.
In this scenario, which two statements are correct? (Choose two.)
- A . The early-ageout configuration specifies the timeout value, in seconds, that will be applied once the low-watermark value is met.
- B . The early-ageout configuration specifies the timeout value, in seconds, that will be applied once the high-watermark value is met.
- C . The high-watermark configuration specifies the percentage of how much of the session table is left before disabling a more aggressive age- out timer.
- D . The high-watermark configuration specifies the percentage of how much of the session table can be allocated before applying a more aggressive age-out timer
Exhibit
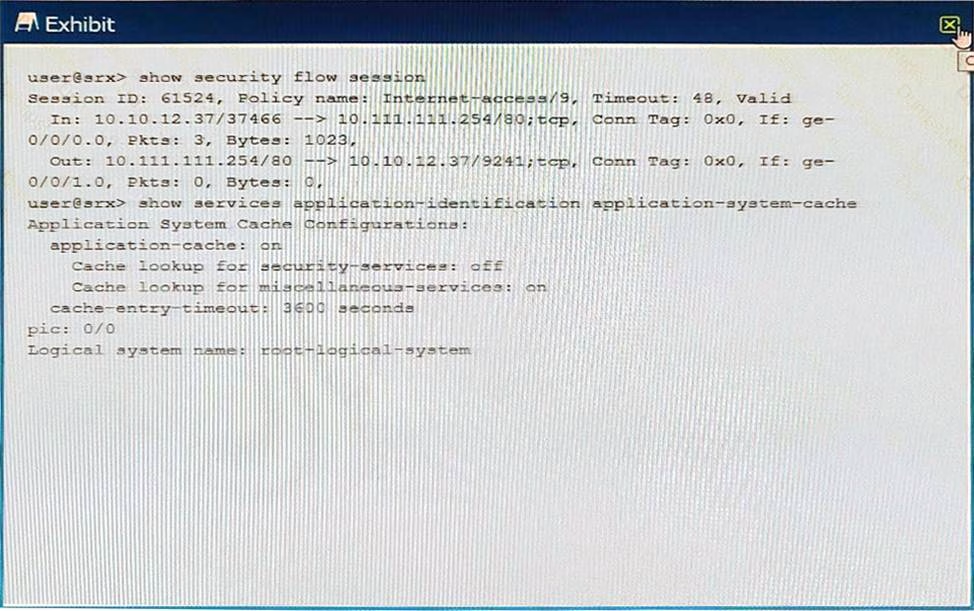
Referring to the exhibit which statement is true?
- A . SSL proxy functions will ignore the session.
- B . SSL proxy leverages post-match results.
- C . SSL proxy must wait for return traffic for the final match to occur.
- D . SSL proxy leverages pre-match result
When a security policy is deleted, which statement is correct about the default behavior of active sessions allowed by that policy?
- A . The active sessions allowed by the policy will be dropped.
- B . The active sessions allowed by the policy will be marked as a legacy flow and will continue to be forwarded.
- C . The active sessions allowed by the policy will be reevaluated by the cached
- D . The active sessions allowed by the policy will continue
You want to use IPS signatures to monitor traffic.
Which module in the AppSecure suite will help in this task?
- A . AppTrack
- B . AppQoS
- C . AppFW
- D . APPID
Exhibit
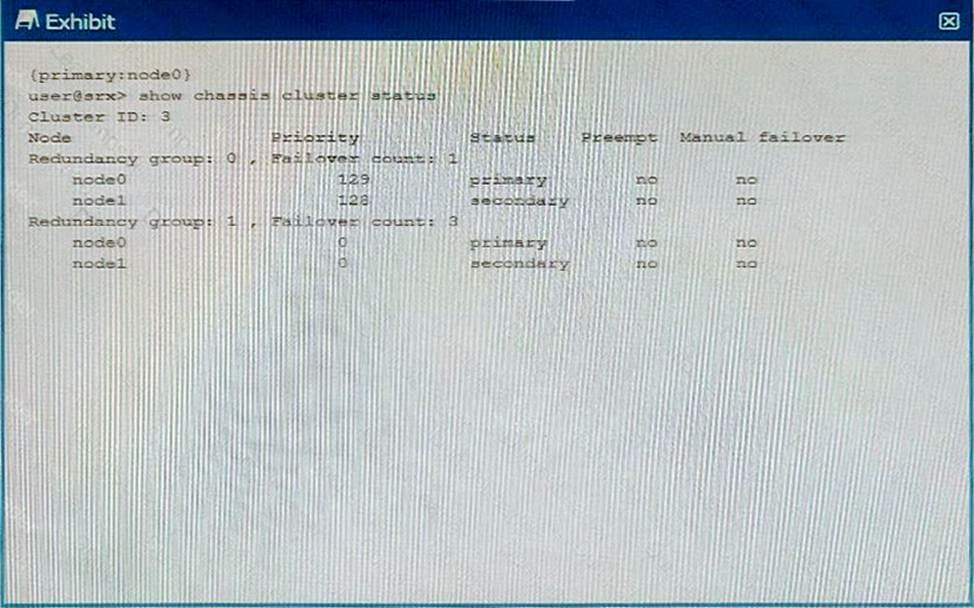
Using the information from the exhibit, which statement is correct?
- A . Redundancy group 1 is in an ineligible state.
- B . Node1 is the active node for the control plane
- C . There are no issues with the cluster.
- D . Redundancy group 0 is in an ineligible state.
Latest JN0-335 Dumps Valid Version with 91 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund

