Juniper JN0-334 Security, Specialist (JNCIS-SEC) Online Training
Juniper JN0-334 Online Training
The questions for JN0-334 were last updated at Mar 03,2026.
- Exam Code: JN0-334
- Exam Name: Security, Specialist (JNCIS-SEC)
- Certification Provider: Juniper
- Latest update: Mar 03,2026
Click the Exhibit button.
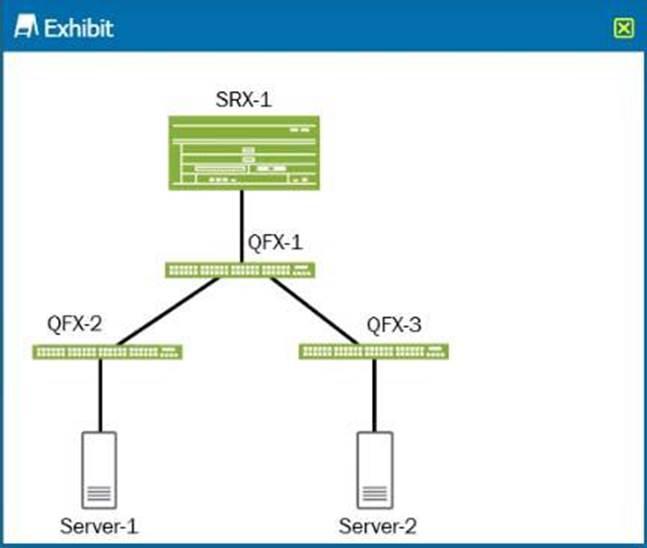
Referring to the exhibit, which two devices are considered to be part of the secure fabric site with Policy Enforcer? (Choose two.)
- A . Server-2
- B . SRX-1
- C . Server-1
- D . QFX-1
What is the maximum number of supported interfaces on a vSRX hosted in a VMware environment?
- A . 4
- B . 10
- C . 3
- D . 12
Click the Exhibit button.
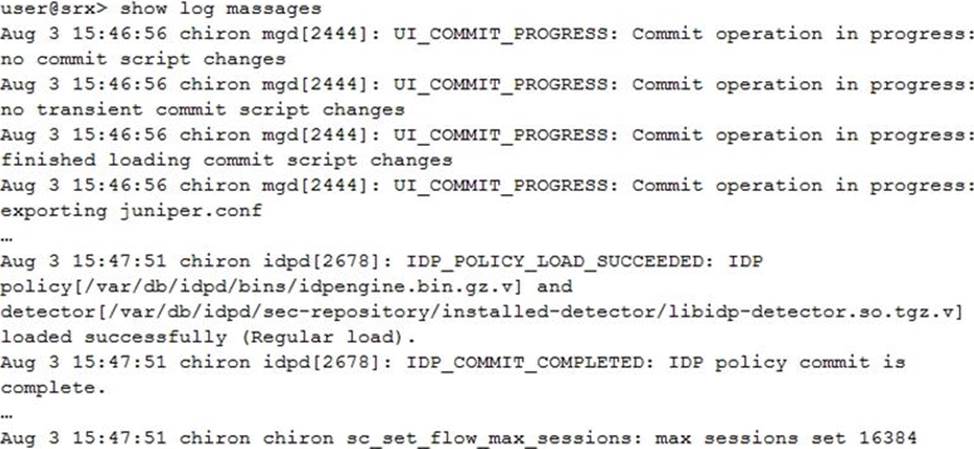
You examine the log file shown in the exhibit after running the set security idp active-policy
command.
Which two statements are true in this scenario? (Choose two.)
- A . The IDP policy compiled successfully.
- B . The IDP policy loaded successfully.
- C . The IDP hit cache is set to 16384.
- D . The entire configuration was committed.
A,B
Explanation:
Reference: https://www.juniper.net/documentation/en_US/junos/topics/topic-map/security-idp-policies-overview.html
What is the default timeout period for a TCP session in the session table of a Junos security device?
- A . 1 minute
- B . 60 minutes
- C . 15 minutes
- D . 30 minutes
Click the Exhibit button.
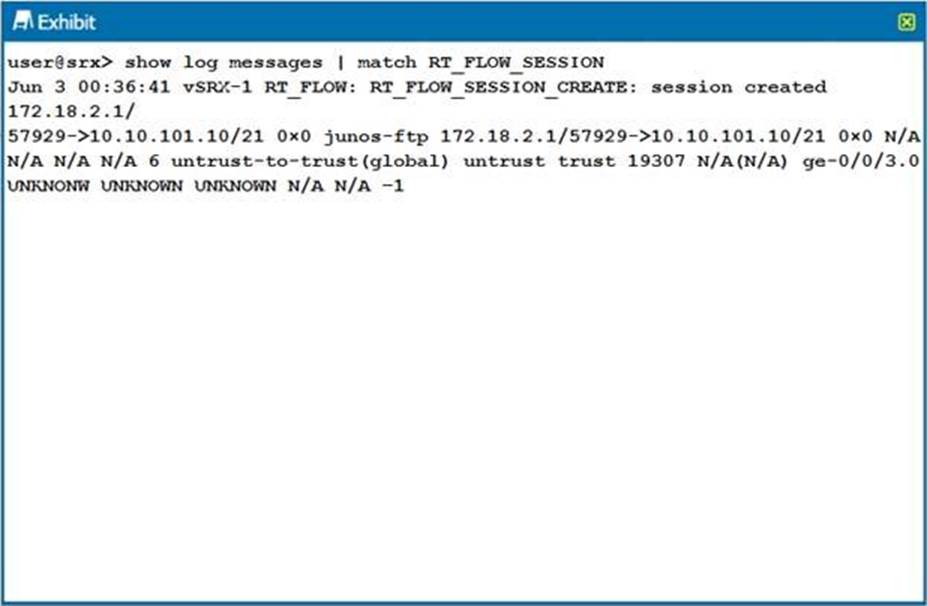
The output shown in the exhibit is displayed in which format?
- A . syslog
- B . sd-syslog
- C . binary
- D . WELF
Which two functions are performed by Juniper Identity Management Service (JIMS)? (Choose two.)
- A . JIMS synchronizes Active Directory authentication information between a primary and secondary JIMS server.
- B . JIMS forwards Active Directory authentication information to SRX Series client devices.
- C . JIMS collects and maintains a database of authentication information from Active Directory domains.
- D . JIMS replicates Active Directory authentication information to non-trusted Active Directory domain controllers.
A,C
Explanation:
https://www.juniper.net/documentation/en_US/junos/topics/reference/configuration-statement/services-user-identification-identity-management-connection-primary.html
You are deploying the Junos application firewall feature in your network.
In this scenario, which two elements are mapped to applications in the application system cache? (Choose two.)
- A . destination port
- B . source port
- C . destination IP address
- D . source IP address
You must fine tune an IPS security policy to eliminate false positives. You want to create exemptions to the normal traffic examination for specific traffic.
Which two parameters are required to accomplish this task? (Choose two.)
- A . source IP address
- B . destination IP address
- C . destination port
- D . source port
Click the Exhibit button.
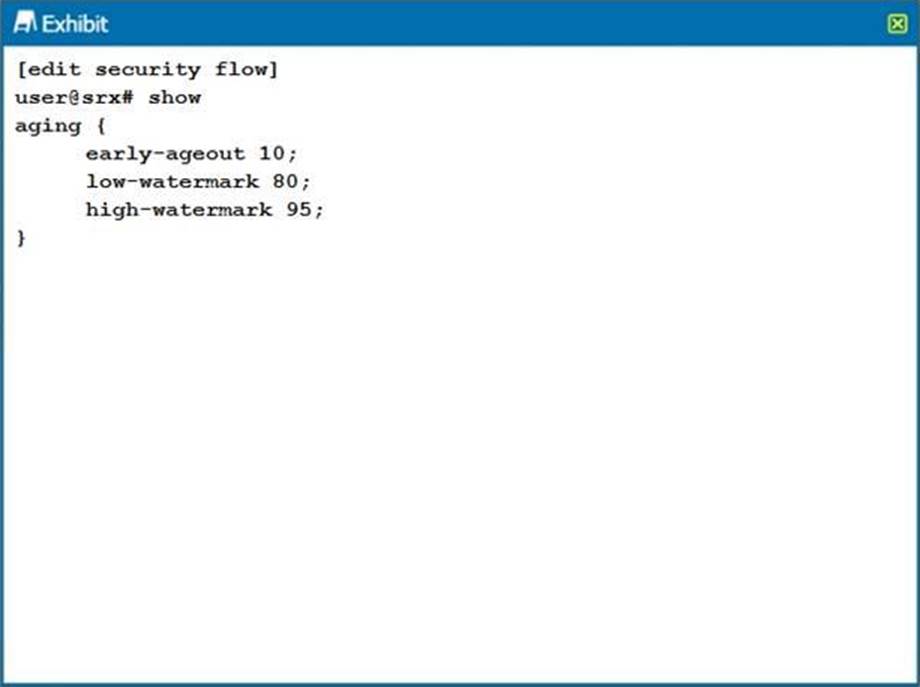
Which two statements are true about the configuration shown in the exhibit? (Choose two.)
- A . The session is removed from the session table after 10 seconds of inactivity.
- B . The session is removed from the session table after 10 milliseconds of inactivity.
- C . Aggressive aging is triggered if the session table reaches 95% capacity.
- D . Aggressive aging is triggered if the session table reaches 80% capacity.
Click the Exhibit button.
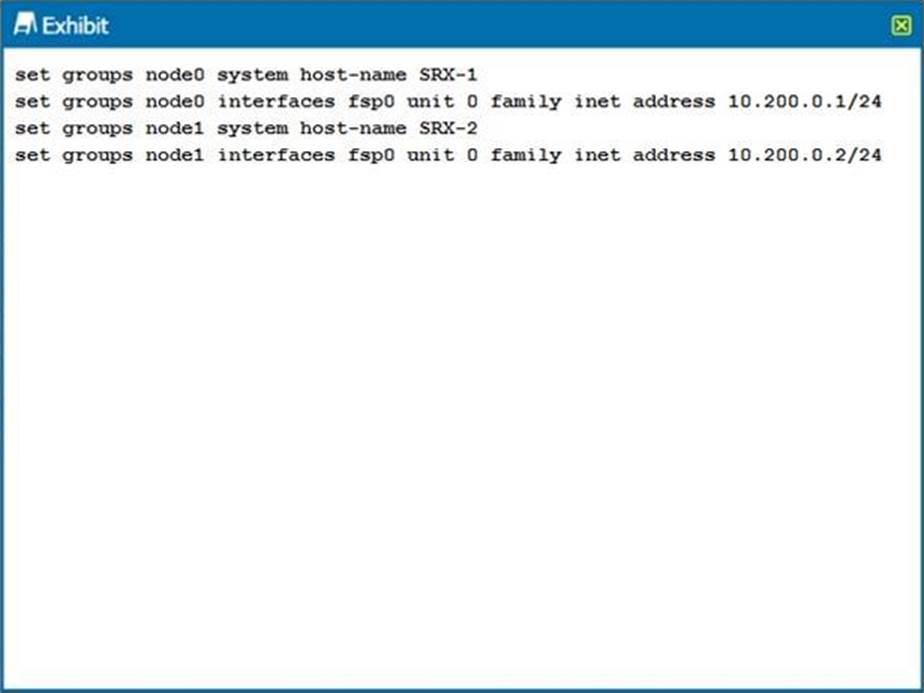
You are configuring an SRX chassis cluster with the node-specific hostname and management address. Referring to the exhibit, which configuration completes this requirement?
A)
![]()
B)
![]()
C)
![]()
D)
![]()
- A . Option A
- B . Option B
- C . Option C
- D . Option D
C
Explanation:
https://kb.juniper.net/InfoCenter/index?page=content&id=KB31080
Latest JN0-334 Dumps Valid Version with 91 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund

