Juniper JN0-333 Security, Specialist (JNCIS-SEC) Online Training
Juniper JN0-333 Online Training
The questions for JN0-333 were last updated at Mar 04,2026.
- Exam Code: JN0-333
- Exam Name: Security, Specialist (JNCIS-SEC)
- Certification Provider: Juniper
- Latest update: Mar 04,2026
Which statement is true about functional zones?
- A . Functional zones are a collection of regulated transit network segments.
- B . Functional zones provide a means of distinguishing groups of hosts and their resources from one another.
- C . Functional zones are used for management.
- D . Functional zones are the building blocks for security policies.
You have recently configured an IPsec tunnel between two SRX Series devices. One of the devices is assigned an IP address using DHCP with an IP address that changes frequently. Initial testing indicates that the IPsec tunnel is not working. Troubleshooting has revealed that Phase 1 negotiations are failing.
Which two actions would solve the problem? (Choose two.)
- A . Verify that the device with the IP address assigned by DHCP is the traffic initiator.
- B . Verify that VPN monitoring is enabled.
- C . Verify that the IKE policy is configured for aggressive mode.
- D . Verify that PKI is properly configured.
Click the Exhibit button.
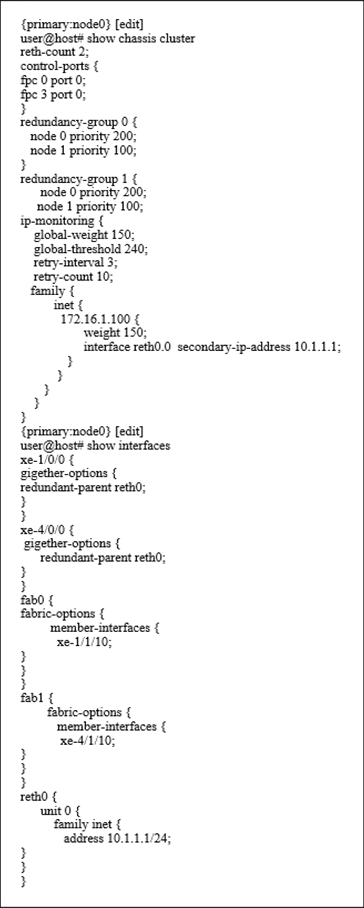
Which statement would explain why the IP-monitoring feature is functioning incorrectly?
- A . The global weight value is too large for the configured global threshold.
- B . The secondary IP address should be on a different subnet than the reth IP address.
- C . The secondary IP address is the same as the reth IP address.
- D . The monitored IP address is not on the same subnet as the reth IP address.
Click the Exhibit button.
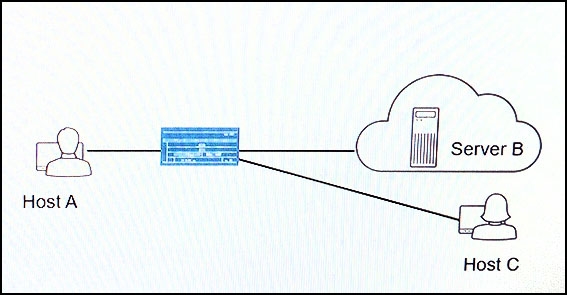
You have configured NAT on your network so that Host A can communicate with Server B. You want to ensure that Host C can initiate communication with Host A using Host A’s reflexive address.
Referring to the exhibit, which parameter should you configure on the SRX Series device to satisfy this requirement?
- A . Configure persistent NAT with the target-hostparameter.
- B . Configure persistent NAT with the target-host-portparameter.
- C . Configure persistent NAT with the any-remote-hostparameter.
- D . Configure persistent NAT with the port-overloadingparameter.
Which feature is used when you want to permit traffic on an SRX Series device only at specific times?
- A . scheduler
- B . pass-through authentication
- C . ALGs
- D . counters
Which two modes are supported during the Phase 1 IKE negotiations used to establish an IPsec tunnel? (Choose two.)
- A . transport mode
- B . aggressive mode
- C . main mode
- D . tunnel mode
Which statement describes the function of NAT?
- A . NAT encrypts transit traffic in a tunnel.
- B . NAT detects various attacks on traffic entering a security device.
- C . NAT translates a public address to a private address.
- D . NAT restricts or permits users individually or in a group.
Click the Exhibit button.
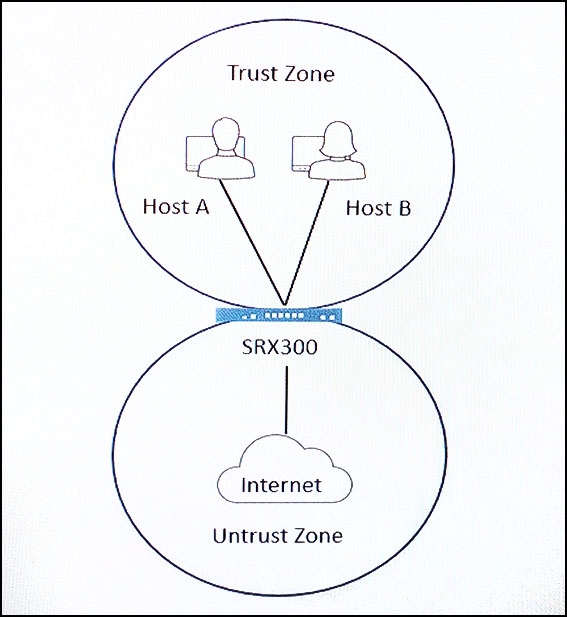
You are monitoring traffic, on your SRX300 that was configured using the factory default security parameters. You notice that the SRX300 is not blocking traffic between Host A and Host B as expected.
Referring to the exhibit, what is causing this issue?
- A . Host B was not assigned to the Untrust zone.
- B . You have not created address book entries for Host A and Host B.
- C . The default policy has not been committed.
- D . The default policy permits intrazone traffic within the Trust zone.
What is the function of redundancy group 0 in a chassis cluster?
- A . Redundancy group 0 identifies the node controlling the cluster management interface IP addresses.
- B . The primary node for redundancy group 0 identifies the first member node in a chassis cluster.
- C . The primary node for redundancy group 0 determines the interface naming for all chassis cluster nodes.
- D . The node on which redundancy group 0 is primary determines which Routing Engine is active in the cluster.
Which statement describes the function of screen options?
- A . Screen options encrypt transit traffic in a tunnel.
- B . Screen options protect against various attacks on traffic entering a security device.
- C . Screen options translate a private address to a public address.
- D . Screen options restrict or permit users individually or in a group.
Latest JN0-333 Dumps Valid Version with 75 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund

