Juniper JN0-230 Juniper Security, Associate (JNCIA-SEC) Exam Online Training
Juniper JN0-230 Online Training
The questions for JN0-230 were last updated at Mar 03,2026.
- Exam Code: JN0-230
- Exam Name: Juniper Security, Associate (JNCIA-SEC) Exam
- Certification Provider: Juniper
- Latest update: Mar 03,2026
What should you configure if you want to translate private source IP address to a single public IP address?
- A . Source NAT
- B . Destination NAT
- C . Content filtering
- D . Security Director
You are configuring an IPsec VPN tunnel between two location on your network. Each packet must be encrypted and authenticated.
Which protocol would satisfy these requirements?
- A . MD5
- B . ESP
- C . AH
- D . SHA
You have created a zones-based security policy that permits traffic to a specific webserver for the marketing team. Other groups in the company are not permitted to access the webserver. When marketing users attempt to access the server they are unable to do so.
What are two reasons for this access failure? (Choose two.)
- A . You failed to change the source zone to include any source zone.
- B . You failed to position the policy after the policy that denies access to the webserver.
- C . You failed to commit the policy change.
- D . You failed to position the policy before the policy that denies access the webserver
Referring to the exhibit.
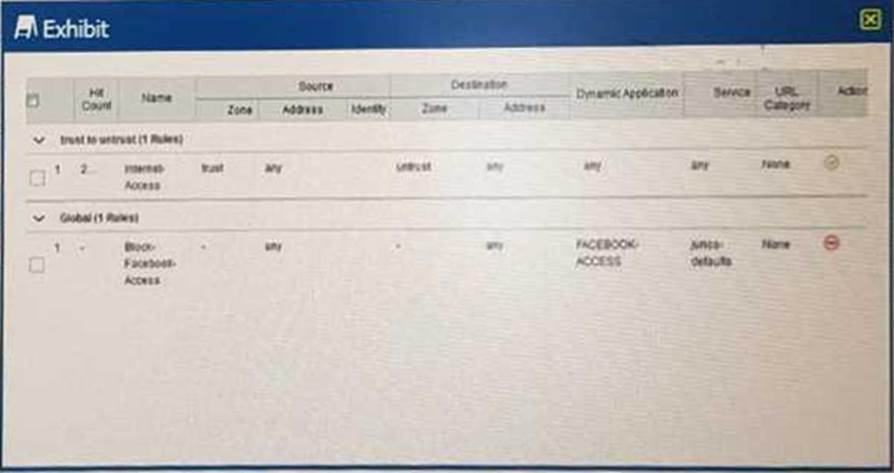
Users on the network are restricted from accessing Facebook, however, a recent examination of the logs show that users are accessing Facebook.
Why is this problem happening?
- A . Global rules are honored before zone-based rules.
- B . The internet-Access rule has a higher precedence value
- C . The internet-Access rule is listed first
- D . Zone-based rules are honored before global rules
On an SRX Series device, how should you configure your IKE gateway if the remote endpoint is a branch office-using a dynamic IP address?
- A . Configure the IPsec policy to use MDS authentication.
- B . Configure the IKE policy to use aggressive mode.
- C . Configure the IPsec policy to use aggressive mode.
- D . Configure the IKE policy to use a static IP address
Which statements is correct about SKY ATP?
- A . Sky ATP is an open-source security solution.
- B . Sky ATP is used to automatically push out changes to the AppSecure suite.
- C . Sky ATP only support sending threat feeds to vSRX Series devices
- D . Sky ATP is a cloud-based security threat analyzer that performs multiple tasks
Which type of security policy protect restricted services from running on non-standard ports?
- A . Application firewall
- B . IDP
- C . Sky ATP
- D . antivirus
Referring to the exhibit.
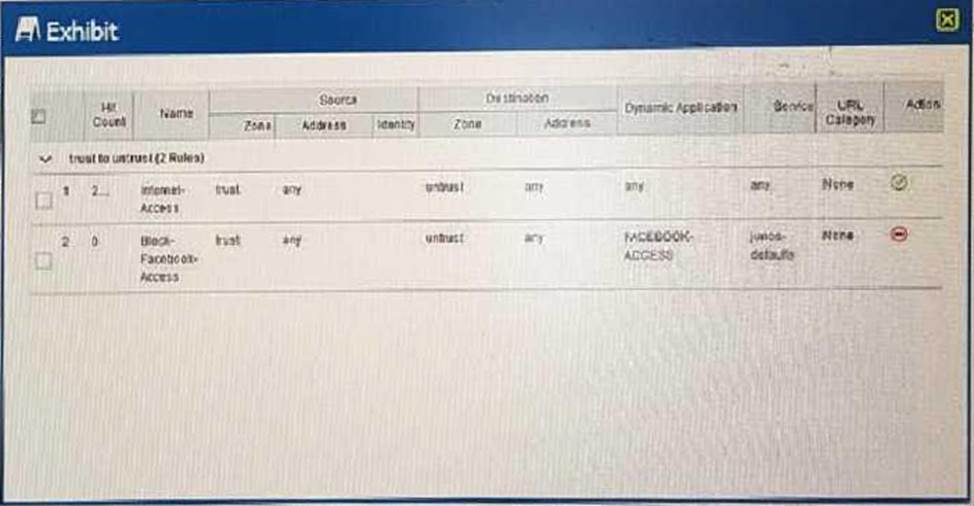
Users should not have access to Facebook, however, a recent examination of the logs security show that users are accessing Facebook.
what should you do to solve this problem?
- A . Change the source address for the Block-Facebook-Access rule to the prefix of the users
- B . Move the Block-Facebook-Access rule before the Internet-Access rule
- C . Move the Block-Facebook-Access rule from a zone policy to a global policy
- D . Change the Internet-Access rule from a zone policy to a global policy
Which statement is correct about IKE?
- A . IKE phase 1 is used to establish the data path
- B . IKE phase 1 only support aggressive mode.
- C . IKE phase 1 negotiates a secure channel between gateways.
- D . IKE phase 1 establishes the tunnel between devices
Which two statements are correct about using global-based policies over zone-based policies? (Choose two.)
- A . With global-based policies, you do not need to specify a destination zone in the match criteria.
- B . With global-based policies, you do not need to specify a source zone in the match criteria.
- C . With global-based policies, you do not need to specify a destination address in the match criteria.
- D . With global-based policies, you do not need to specify a source address in the match criteria.
Latest JN0-230 Dumps Valid Version with 82 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund

