Juniper JN0-1362 Service Provider Design, Specialist (JNCDS-SP) Online Training
Juniper JN0-1362 Online Training
The questions for JN0-1362 were last updated at Dec 17,2025.
- Exam Code: JN0-1362
- Exam Name: Service Provider Design, Specialist (JNCDS-SP)
- Certification Provider: Juniper
- Latest update: Dec 17,2025
Click the Exhibit button:
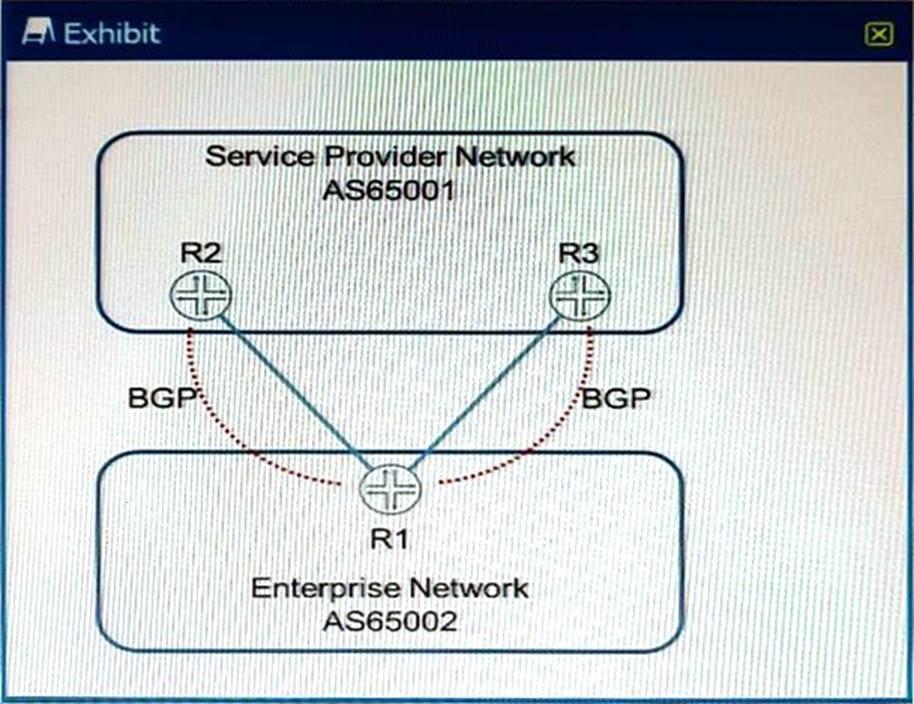
Referring to the exhibit, which mechanism is used to advertise routes from the enterprise network to the service provider network?
- A . BGP flowspec
- B . BGP export policies
- C . BGP import policies
- D . firewall filters
As a service provider network architect, you are working with a potential customer who wants to replace their WAN, consisting of two data centers, one HQ, and 76 branch offices Due to application latency requirements between branch offices, the customer insists that all traffic must take the most optimal path through the service provider network. The customer intends to encrypt all traffic between customer routers at each location.
Which WAN technology would you propose in this scenario?
- A . point-to-point Layer 2 VPNs
- B . Layer 3 VPN
- C . Internet as WAN
- D . H-VPLS
What are two benefits of including analytics in your network management design proposal? (Choose two.)
- A . Analytics can be used for troubleshooting and diagnosing network problems
- B . Analytics dynamically standardizes software and firmware versions.
- C . Analytics can allow administrators to evaluate and optimize WAN resources.
- D . Analytics dynamically makes network optimization change
You are developing a CoS policy for a service provider core network that In this scenario, which three statements are correct? (Choose three.)
- A . Core routers should use a common set of per-hop behaviors.
- B . Core routers should use shapers to ensure that customer traffic does not exceed allowed bandwidth.
- C . Core routers should use policers to ensure that customer traffic does not exceed allowed bandwidth.
- D . Core routers should use a consistent CoS configuration across the network.
- E . Core routers should use the DSCP markings already set on ingress traffic.
As a service provider network engineer, you are asked by management design a Layer 2 VPN product with a ‘’five nines’’ SLA.
Which mechanism will address this requirement?
- A . VRRP
- B . EVPN LAG
- C . GRES
- D . SyncE
What are two network management benefits of using devices in your design proposals?
- A . Virtualization allows network administrators to dynamically make configuration changes to all network devices.
- B . Virtualization can lower costs because there are fewer physical devices that need to be purchased and managed.
- C . Virtualization can increase the available network bandwidth because their interface speeds are only limited by the host device.
- D . Virtualization allows network administrators to dynamically add and remove services beingprovided
Your customer wants to enable their MX Series core so that a controller can dynamically manage their LSPs.
Which protocol provides this capability?
- A . BGP-LU
- B . PCEP
- C . PCRF
- D . BGP-LS
What are three limitations of using the Internet as the primary WAN service for enterprise organizations? (Choose three)
- A . generally higher cost
- B . no latency considerations
- C . lack of connectivity
- D . no quality of service guarantees
- E . no inherent security
Your customer’s enterprise is adding geographically dispersed branch offices and requires newWAN connections. The primary design consideration for this expansion is low cost.
Which type of WAN connection satisfies the customer’s requirement in this scenario?
- A . leased line dedicated circuit
- B . Internet connection with IPsec
- C . transparent Layer 2 service
- D . MPLS Layer 3 VPN
You are asked to create a point-to-multipoint DCI that does not overwhelm the data plane with MAC learning traffic.
Which protocol would you use in this situation?
- A . VPLS
- B . PPTP
- C . EVPN
- D . pseudowire
Latest JN0-1362 Dumps Valid Version with 65 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund

