Which two statements describe Juniper ATP Cloud? (Choose two)
- A . Juniper ATP Cloud can use a sandbox to detect threats that use evasion techniques.
- B . Juniper ATP Cloud runs mime with network traffic to Nock all traffic before reaching endpoint.
- C . Juniper ATP Cloud provides protection against zero-day threats
- D . Juniper ATP Cloud is an added app that must be instated with Security Director
Physical security devices are ”blind” to which type of traffic?
- A . bare metal server to VM
- B . private VLAN
- C . intra-server traffic
- D . management
Which technology enables IPS inspection for users browsing websites that use Transport Layer Security (TLS)?
- A . SSL reverse proxy
- B . defense in-depth
- C . SSL forward proxy
- D . screens
You must implement a solution to deploy end-to-end security services on network elements.
Which solution will accomplish this task?
- A . Security Director
- B . Network Director
- C . JSA
- D . SRX Series devices
You are asked to implement Jumper AppSecure to increase application security. You want to analyze specific application usage In this scenario.
Which AppSecure feature would accomplish this task?
- A . AppQoS
- B . AppTrack
- C . AppFW
- D . IDP/IP
Which two statements are true about WAN security considerations? (Choose two.)
- A . MACsec increases protection on alt WAN types
- B . Provider VPN circuit require iPsec
- C . internal connections are susceptible to fragmentation
- D . IPsec increases protection on all WAN types
You are designing a security solution that includes SRX Series firewalls in a chassis cluster.
In this scenario. which two dements must be part of the design? (Choose two.)
- A . The physical interface on each SRX Series device making up the reth interface must be in the same L2 domain
- B . The physical interface on each SRX Series device making up the reth interface must be in separate L2 domains
- C . The duster ID must be the same on both SRX Series devices
- D . The node 10 must be the same on both SRX Series devices
When designing the security for a service provider core router, you are asked to add a firewall fitter on the to0 interface in this scenario, which two protocols would you want to allow through the filter? (Choose two.)
- A . LLDP
- B . SSH
- C . BGP
- D . STP
Which automation language would you use to create on-box and off-box scripts for SRX Series devices?
- A . Python
- B . Pert
- C . Java
- D . Ruby
Which three statements about Group VPNs #e true? (Choose three.)
- A . The IP pay load is encrypted
- B . Data can flow directly between sites without transiting a central hub
- C . Group VPNs use a client/server architecture
- D . All data transits through a central hub
- E . The IP headers are encrypted
You want to reduce the possibility of your data center’s server becoming an unwilling participant in a DDoS attack When tvA3 features should you use on your SRX Series devices to satisfy this requirement? (Choose two.)
- A . dynamic IPsec tunnels
- B . Juniper ATP Cloud GeolP
- C . UTMWebtaering
- D . Juniper ATP Cloud CC feeds
When using Contra! networking, security policies are distributed as access control list to which component?
- A . vSwith
- B . vSRX
- C . vMX
- D . vRouter
Exhibit.
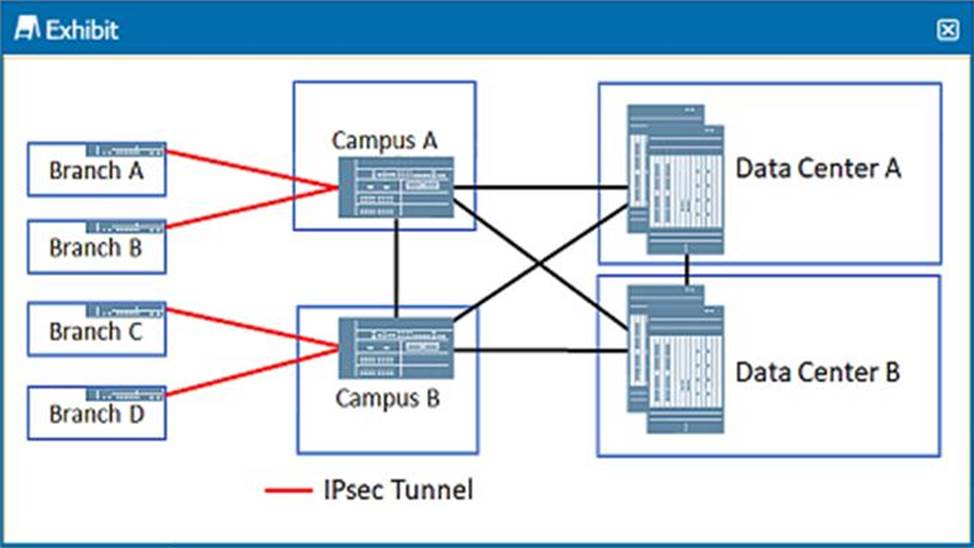
In the 3-tier VPN design shown in the exhibit, which function are the Campus A and Campus B SRX Series devices performing?
- A . Internet security gateway
- B . data center firewall
- C . WAN aggregation
- D . VPN bridging
Which statement about Junos firewall filters is correct?
- A . Firewall filters can be applied as a security policy action
- B . Firewall filters do not operate on stateful flows and they serve no purpose in a next-generation firewall
- C . Firewall filters can be applied as the packet enters the security device, and they are stateless.
- D . Firewall filters are applied to TCP packets only. and they do not block UDP pockets
According to Juniper Networks, what are two focus points when designing a secure network? (Choose two.)
- A . performance
- B . automation
- C . distributed control
- D . classification
You arc designing a high availability firewall solution You select an off-path design instead of an mime design.
What arc two reasons for this decision? (Choose two.)
- A . The off-path design is less complex
- B . The off-path design is more flexible
- C . The off-path design uses fewer interfaces at the adjacency layer
- D . The off-path design requires a proper routing configuration for selecting traffic
You are designing a security solution for an existing data center. All traffic most be secured using SRX Series devices, however, you are unable to change the existing IP addressing scheme.
Which firewall deployment method satisfies this requirement?
- A . transparent deployment
- B . two-arm deployment
- C . one-arm deployment
- D . inline deployment
You are asked to enable denial of service protection for a webserver behind an SRX Series device In this scenario, which feature would you enable?
- A . screens
- B . App Secure
- C . Web filtering
- D . Juniper ATP
Which solution would you deploy to accomplish this task?
- A . Junes Space Log Director
- B . Juniper Networks Central insights
- C . Junos Space Security Director
- D . Juniper Networks Secure Analytics
In yew network design, you must include a method to block IP addresses from certain countries that will automatically update within the SRX Series devices’ security policies.
Which technology would accomplish this goal?
- A . UTM
- B . GeolP
- C . dynamic DNS
- D . IPS