Juniper JN0-1331 Security Design, Specialist (JNCDS-SEC) Online Training
Juniper JN0-1331 Online Training
The questions for JN0-1331 were last updated at Dec 21,2025.
- Exam Code: JN0-1331
- Exam Name: Security Design, Specialist (JNCDS-SEC)
- Certification Provider: Juniper
- Latest update: Dec 21,2025
You are concerned about malicious attachments being transferred to your e-mail server at work through encrypted channels. You want to block these malicious files using your SRX Series device.
Which two features should you use in this scenario? (Choose two.)
- A . Sky ATP SMTP scanning
- B . Sky ATP HTTP scanning
- C . SSL forward proxy
- D . SSL reverse proxy
AC
Explanation:
Reference: https://www.juniper.net/documentation/en_US/release-independent/sky-atp/help/informationproducts/pathway-pages/email-scanning-sky-atp.html
Click the Exhibit button.
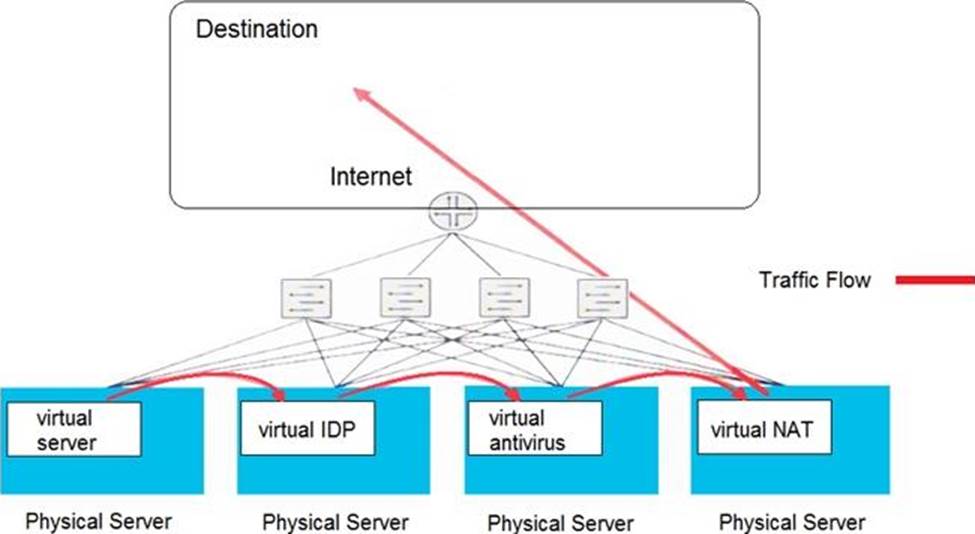
Which type of security solution is shown in this exhibit?
- A . service chain model
- B . centralized model
- C . inline security model
- D . de-centralized model
You are designing an Internet security gateway (ISG) for your company and are considering a centralized versus a distributed model for ISGs.
Which two statements are correct in this scenario? (Choose two.)
- A . Distributed ISGs typically have less latency compared to centralized ISGs
- B . Distributed ISGs reduce bandwidth for end users
- C . Distributed ISGs typically require extra bandwidth for management
- D . Distributed ISGs are harder to manage compared to centralized ISGs
You are creating a data center security design. Virtual security functions must be performed on east-west traffic. Security functions must be commissioned and decommissioned frequently, and the least resource-intensive architecture must be used.
In this scenario, what will accomplish this task?
- A . all-in-one NFV security devices with device templates
- B . service chaining with container-based security functions
- C . a security appliance segmented into logical systems
- D . filter-based forwarding to direct traffic to the required security devices
What are two reasons for using cSRX over vSRX? (Choose two.)
- A . cSRX loads faster
- B . cSRX uses less memory
- C . cSRX supports the BGP protocol
- D . cSRX supports IPsec
AB
Explanation:
Reference: https://www.juniper.net/documentation/en_US/csrx/information-products/pathway-pages/security-csrx-linux-bm-guide-pwp.pdf
Latest JN0-1331 Dumps Valid Version with 65 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund

