ISTQB CTFL_SYLL_4.0 ISTQB Certified Tester Foundation Level (CTFL) Online Training
ISTQB CTFL_SYLL_4.0 Online Training
The questions for CTFL_SYLL_4.0 were last updated at Dec 20,2025.
- Exam Code: CTFL_SYLL_4.0
- Exam Name: ISTQB Certified Tester Foundation Level (CTFL)
- Certification Provider: ISTQB
- Latest update: Dec 20,2025
For each of the test cases to be executed, the following table specifies the priority order and dependencies on other test cases
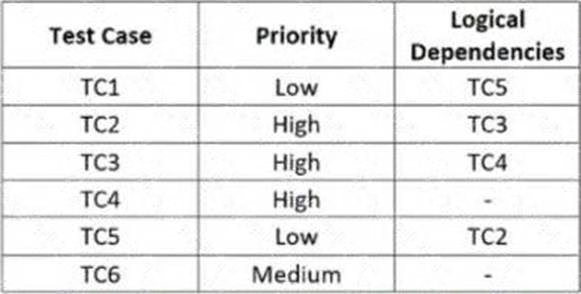
Which of the following test execution schedules is compatible with the logical dependencies and allows executing the test cases in priority order?
- A . TC4, TC3, TC2, TC6, TC5. TC1
- B . TC4, TC6, TC3, TC2, TC5, TC1
- C . TC3, TC5, TC6, TC1, TC4, TC3
- D . TC4, TC3, TC2, TC6, TC1, TC5
Which of the following statements best describes how configuration management supports testing?
- A . Configuration management helps reduce testing effort by identifying a manageable number of test environment configurations in which to test the software, out of all possible configurations of the environment in which the software will be released
- B . Configuration management is an administrative discipline that includes change control, which is the process of controlling the changes to identified items referred to as Configuration Items’
- C . Configuration management is an approach to interoperability testing where tests are executed in the cloud, as the cloud can provide cost-effective access to multiple configurations of the test environments
- D . Configuration management helps ensure that all relevant project documentation and software items are uniquely identified in all their versions and therefore can be unambiguously referenced in test documentation
Which of the following statements about exploratory testing is true?
- A . Exploratory testing is an experience-based test technique in which testers explore the requirements specification to detect non testable requirements
- B . When exploratory testing is conducted following a session-based approach, the issues detected by the testers can be documented in session sheets
- C . Exploratory testing is an experience-based test technique used by testers during informal code reviews to find defects by exploring the source code
- D . In exploratory testing, testers usually produce scripted tests and establish bidirectional traceability between these tests and the items of the test basis
In a two-hour uninterrupted test session, performed as part of an iteration on an Agile project, a heuristic checklist was used to help the tester focus on some specific usability issues of a web application.
The unscripted tests produced by the tester’s experience during such session belong to which one of the following testing quadrants?
- A . Q1
- B . Q2
- C . Q3
- D . Q4
Which of the following is not an example of a typical content of a test completion report for a test project?
- A . The additional effort spent on test execution compared to what was planned
- B . The unexpected test environment downtime that resulted in slower test execution
- C . The residual risk level if a risk-based test approach was adopted
- D . The test procedures of all test cases that have been executed
Which of the following statements about error guessing is true?
- A . Error guessing is a system that adopts artificial intelligence to predict whether software components are likely to contain defects or not
- B . Experienced testers, when applying error guessing, rely on the use of a high-level list of what needs to be tested as a guide to find defects
- C . Error guessing refers to the ability of a system or component to continue normal operation despite the presence of erroneous inputs
- D . Experienced testers, when applying error guessing technique, can anticipate where errors, defects and failures have occurred and target their tests at those issues
Which of the following is a task the Author is responsible for, as part of a typical formal review?
- A . Determining the people who will be involved in the review
- B . Recording the anomalies found during the review meeting
- C . Identifying potential anomalies in the work product under review
- D . Fixing the anomalies found in the work product under review
The whole-team approach:
- A . promotes the idea that all team members should have a thorough understanding of test techniques
- B . is a consensus-based approach that engages the whole team in estimating the user stories
- C . promotes the idea that all team members should be responsible for the quality of the product
- D . is mostly adopted in projects aimed at developing safety-critical systems, as it ensures the highest level of testing independence
Consider the following user story about the authentication functionality of an e-commerce website:
"As a logged-in user, I want to change my current password with a new one, so that I can make my account safer".
The following are some of the acceptance criteria defined for the user story:
[a] After the logged-in user has successfully changed his password, an email confirming the change must be sent to him
[b] To successfully change the password, the logged-in user must enter the current password, enter a
new valid password, and finally confirm by pressing the ‘Change Password’ button
[c] To be valid, the new password entered by the logged-in user is not only required to meet the criteria related to the length and type of characters, but must also be different form the last 5 passwords of that user
[d] A dedicated error message must be presented to the logged-in user when he enters a wrong current password
[e] A dedicated error message must be presented to the logged-in user when he enters the correct current password, but enters an invalid password
Based only on the given information, which of the following ATDD tests is most likely to be written first?
- A . The logged-in user enters a wrong current password and views the dedicated error message
- B . The logged-in user enters the correct current password, enters a valid new password (different from the last 5 passwords), presses the Change Password’ button, and finally receives the e-mail confirming that the password has been successfully changed
- C . The logged-in user enters the correct current password, enters an invalid password, and finally views the dedicated error
- D . The logged-in user submits a purchase order containing ten items, selects to pay with a Visa credit card, enters credit card information of a valid card, presses the ‘Confirm’ button, and finally views the dedicated message confirming that the purchase has been successful
Which of the following is not an example of a typical generic skill required for testing?
- A . Be able to apply test-driven development
- B . Be able to use test management tools and defect tracking tools
- C . Be able to communicate defects and failures to developers as objectively as possible
- D . Possess the necessary social skills that support effective teamwork
Latest CTFL_SYLL_4.0 Dumps Valid Version with 40 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund

