Which of the following is an element of monitoring and improving a CSMS?
Available Choices (select all choices that are correct)
- A . Increase in staff training and security awareness
- B . Restricted access to the industrial control system to an as-needed basis
- C . Significant changes in identified risk round in periodic reassessments
- D . Review of system logs and other key data files
Which of the following attacks relies on a human weakness to succeed?
Available Choices (select all choices that are correct)
- A . Denial-of-service
- B . Phishing
- C . Escalation-of-privileges
- D . Spoofing
What is a feature of an asymmetric key?
Available Choices (select all choices that are correct)
- A . Uses a continuous stream
- B . Uses different keys
- C . Shares the same key OD.
- D . Has lower network overhead
Which of the following is an example of separation of duties as a part of system development and maintenance?
Available Choices (select all choices that are correct)
- A . Changes are approved by one party and implemented by another.
- B . Configuration settings are made by one party and self-reviewed using a checklist.
- C . Developers write and then test their own code.
- D . Design and implementation are performed by the same team.
Which is an important difference between IT systems and IACS?
Available Choices (select all choices that are correct)
- A . The IACS security priority is integrity.
- B . The IT security priority is availability.
- C . IACS cybersecurity must address safety issues.
- D . Routers are not used in IACS networks.
What is the name of the missing layer in the Open Systems Interconnection (OSI) model shown below?
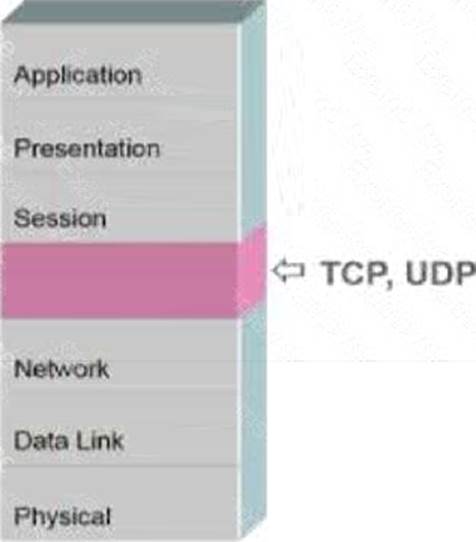
- A . Control
- B . Protocol
- C . Transport
- D . User
What are the four main categories for documents in the ISA-62443 (IEC 62443) series?
Available Choices (select all choices that are correct)
- A . General. Policies and Procedures. System, and Component
- B . End-User, Integrator, Vendor, and Regulator
- C . Assessment. Mitigation. Documentation, and Maintenance
- D . People. Processes. Technology, and Training
Safety management staff are stakeholders of what security program development?
Available Choices (select all choices that are correct)
- A . CSMS
- B . SPRP
- C . CSA
- D . ERM
What does the abbreviation CSMS round in ISA 62443-2-1 represent?
Available Choices (select all choices that are correct)
- A . Control System Management System
- B . Control System Monitoring System
- C . Cyber Security Management System
- D . Cyber Security Monitoring System
Which organization manages the ISA Secure conformance certification program?
Available Choices (select all choices that are correct)
- A . American Society for Industrial Security
- B . Automation Federation
- C . National Institute of Standards and Technology
- D . Security Compliance Institute
Which is the PRIMARY objective when defining a security zone?
Available Choices (select all choices that are correct)
- A . All assets in the zone must be from the same vendor.
- B . All assets in the zone must share the same security requirements.
- C . All assets in the zone must be at the same level in the Purdue model.
- D . All assets in the zone must be physically located in the same area.
Which layer in the Open Systems Interconnection (OSI) model would include the use of the File Transfer Protocol (FTP)?
Available Choices (select all choices that are correct)
- A . Application layer
- B . Data link layer
- C . Session layer
- D . Transport layer
Authorization (user accounts) must be granted based on which of the following?
Available Choices (select all choices that are correct)
- A . Individual preferences
- B . Common needs for large groups
- C . Specific roles
- D . System complexity
Which of the following is the BEST example of detection-in-depth best practices?
Available Choices (select all choices that are correct)
- A . Firewalls and unexpected protocols being used
- B . IDS sensors deployed within multiple zones in the production environment
- C . Role-based access control and unusual data transfer patterns
- D . Role-based access control and VPNs
What is OPC?
Available Choices (select all choices that are correct)
- A . An open standard protocol for real-time field bus communication between automation technology devices
- B . An open standard protocol for the communication of real-time data between devices from different manufacturers
- C . An open standard serial communications protocol widely used in industrial manufacturing environments
- D . A vendor-specific proprietary protocol for the communication of real-time plant data between control devices
Which analysis method is MOST frequently used as an input to a security risk assessment?
Available Choices (select all choices that are correct)
- A . Failure Mode and Effects Analysis
- B . Job Safety Analysis
- C . Process Hazard Analysis (PHA)
- D . System Safety Analysis(SSA)
What is a commonly used protocol for managing secure data transmission over a Virtual Private Network (VPN)?
Available Choices (select all choices that are correct)
- A . HTTPS
- B . IPSec
- C . MPLS
- D . SSH
Which of the following is an activity that should trigger a review of the CSMS?
Available Choices (select all choices that are correct)
- A . Budgeting
- B . New technical controls
- C . Organizational restructuring
- D . Security incident exposing previously unknown risk.
Security Levels (SLs) are broken down into which three types?
Available Choices (select all choices that are correct)
- A . SL-1, SL-2, and SL-3
- B . Target.capability, and achieved
- C . Target.capability, and availability
- D . Target.capacity, and achieved
Which is one of the PRIMARY goals of providing a framework addressing secure product development life-cycle requirements?
Available Choices (select all choices that are correct)
- A . Aligned development process
- B . Aligned needs of industrial users
- C . Well-documented security policies and procedures
- D . Defense-in-depth approach to designing
Which activity is part of establishing policy, organization, and awareness?
Available Choices (select all choices that are correct)
- A . Communicate policies.
- B . Establish the risk tolerance.
- C . Identify detailed vulnerabilities.
- D . Implement countermeasures.
Why is patch management more difficult for IACS than for business systems?
Available Choices (select all choices that are correct)
- A . Overtime pay is required for technicians.
- B . Many more approvals are required.
- C . Patching a live automation system can create safety risks.
- D . Business systems automatically update.
Which is a reason for and physical security regulations meeting a mixed resistance?
Available Choices (select all choices that are correct)
- A . Regulations are voluntary documents.
- B . Regulations contain only informative elements.
- C . Cybersecurity risks can best be managed individually and in isolation.
- D . There are a limited number of enforced cybersecurity and physical security regulations.
How many element qroups are in the "Addressinq Risk" CSMS cateqorv?
Available Choices (select all choices that are correct)
- A . 2
- B . 3
- C . 4
- D . 5
Which is a PRIMARY reason why network security is important in IACS environments?
Available Choices (select all choices that are correct)
- A . PLCs are inherently unreliable.
- B . PLCs are programmed using ladder logic.
- C . PLCs use serial or Ethernet communications methods.
- D . PLCs under cyber attack can have costly and dangerous impacts.
Which of the following is an industry sector-specific standard?
Available Choices (select all choices that are correct)
- A . ISA-62443 (EC 62443)
- B . NIST SP800-82
- C . API 1164
- D . D. ISO 27001
Using the risk matrix below, what is the risk of a medium likelihood event with high consequence?
- A . Option A
- B . Option B
- C . Option C
- D . Option D
Which is a physical layer standard for serial communications between two or more devices?
Available Choices (select all choices that are correct)
- A . RS232
- B . RS235
- C . RS432
- D . RS435
Which of the following is a recommended default rule for IACS firewalls?
Available Choices (select all choices that are correct)
- A . Allow all traffic by default.
- B . Allow IACS devices to access the Internet.
- C . Allow traffic directly from the IACS network to the enterprise network.
- D . Block all traffic by default.
Which communications system covers a large geographic area?
Available Choices (select all choices that are correct)
- A . Campus Area Network (CAN)
- B . Local Area Network (LAN)
- C . Storage Area Network
- D . Wide Area Network (WAN)