Huawei H12-731-ENU HCIE-Security (Huawei Certified Internetwork Expert-Security) Online Training
Huawei H12-731-ENU Online Training
The questions for H12-731-ENU were last updated at Apr 26,2025.
- Exam Code: H12-731-ENU
- Exam Name: HCIE-Security (Huawei Certified Internetwork Expert-Security)
- Certification Provider: Huawei
- Latest update: Apr 26,2025
The networking of a certain network is as follows: PC—-ADSL router—–USG—–LAN
The key configurations of the USG are as follows:
l2tp enable
interface Virtual-Template1
ppp authentication-mode pap
ip address 4.1.1.1 255.255.255.0
remote address pool 1
l2tp-group 1
mandatory-Icp
allow 12tp virtual-template 1
#
user-ma page user pc1
password admin@123
aaa
domain default
ip pool 1 4.1.1.1 4.1.1.99
Assuming that other configurations are complete and correct, what is the problem with this configuration in actual work?
- A . You can dial successfully, and you can also access the intranet server.
- B . Cannot dial successfully.
- C . Disconnect immediately after successful dialing.
- D . The dial-up is successful, but the intranet server cannot be accessed.
Which of the following attack methods are network layer attacks? (Multiple Choice)
- A . Constructing data packets with wrong TTL value, causing the device to handle abnormally.
- B . Constructing many SYN packets, leading to exhaustion of host resources.
- C . Construct a packet with abnormal TCP flag bit, causing the host to process abnormally.
- D . Constructing a packet with an incorrect IP fragment flag, causing the host to process abnormally.
When the dual-system hot backup network is used, according to this configuration, PC2 sends an ARP request to the Mac of IP10.100.30.8. Which of the following options is correct?
sysname NGFW_A
#
hrp enable
hrp interface GigabitEthernet 0/0/3
#
interface GigabitEthernet0/0/1
ip address 192.168.10.2 255.255.255.0
vrrp vrid 1 virtual-ip 192.168.10.1 active
#
interface GigabitEthernet0/0/2
ip address 10.100.30.2 255.255.255.0
vrrp vrid 2 virtual-ip 10.100.30.1 active
#
Nat address-group 1
section 0 10.100.30.8 10.100.30.9
#
nat-policy
rule name trust to untrust
source-zone trust
destination-zone untrust
source-address 192.2163.10.0 24
action nat address-group 1
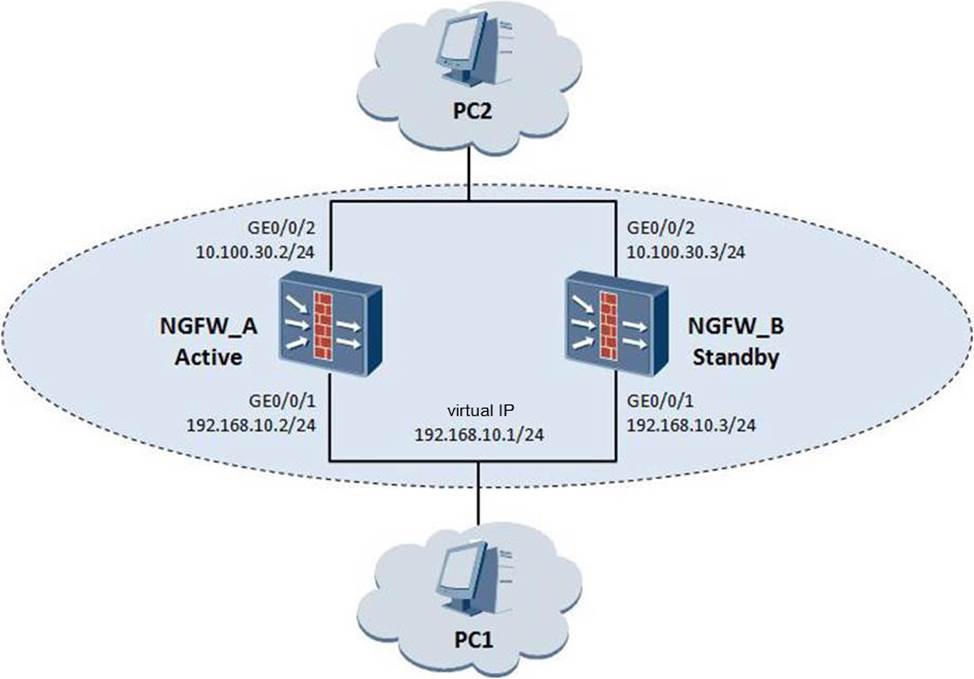
- A . NGFW_A responds to this ARP with VMAC
- B . NGFW_B responds to this ARP with VMAC
- C . The MAC of the NGFW_A interface responds to this ARP
- D . The MAC of the NGFW_B interface responds to this ARP
If the content of the visited web page contains filtered content, what will be the result?
- A . Display "Cannot open webpage"
- B . Display "The web page has been filtered".
- C . The filtered content is deleted and will not be displayed.
- D . The filter content is replaced with “*”.
The Trust zone of the USG firewall of a certain network is connected to the terminal host, and the Untrust zone is connected to the security controller. If the security controller can issue rules to the USG, which of the following security policies must be configured?
- A . security-policy
rule name local_to_trust
source-zone local
destination-zone trust
action permit - B . security-policy
rule name untrust_to_local
source-zone untrust
destination-zone local
action permit - C . security-policy
rule name to_local
source-zone untrust trust
destination-zone local
action permit - D . security-policy
rule name untrust_to_local
source-zone untrust
destination-zone local
action permit
rule name local_to_trust
source-zone local
destination-zone trust
action permit
When the network traffic is heavy, if you do not want the downstream network to be congested or directly discard many packets due to the excessive data traffic sent upstream, you can limit and cache the traffic on the outbound interface of the upstream device, so that such packets can be blocked. The text is sent out at a relatively uniform speed.
This technique can be:
- A . GTS
- B . Car
- C . WRED
- D . CBWFQ
VGMP unified management of VRRP backup group status, VGMP management group Active priority is 65001, Standby priority is 65000. When the VGMP management group detects that the interface is Down through the VRRP backup group or directly, the priority of the VGMP management group is recalculated. When each interface is Down, the priority of the VGMP management group decreases by 2.
- A . TRUE
- B . FALSE
NGFW_A and NGFW_B, NGFW_A and NGFW_C configure static routes respectively. NGFW_A -> NGFW_B is the primary link, and NGFW_A -> NGFW_C is the backup link. It is required that the traffic can be quickly switched to the backup link when the primary link fails; the traffic can be switched to the primary chromium road after the primary link is restored.
Which of the following configuration is correct? (Multiple Choice)
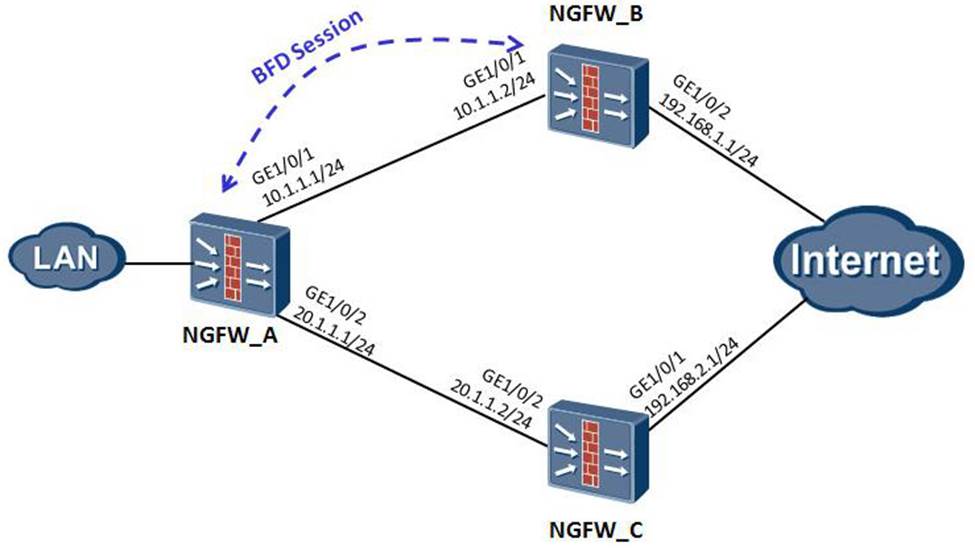
A. [USG_A] bfd
[USG_A] bfd ab bind peer-ip 10.1.1.2
[USG_A-bfd-session-ab] discriminator local 10
[USG_A-bfd-session-ab] discriminator remote 20
[USG_A-bfd-session-ab] commit
[USG_A] ip route-static 0.0.0.0 0 10.1.1.2 track bfd-session ab
[USG_A] ip route-static 0.0.0.0 0 20.1.1.2 preference 100
B. [USG_A] bfd
[USG_A] bfd ab bind peer-ip 10.1.1.2
[USG_A-bfd-session-ab] discriminator local 10
[USG_A-bfd-session-ab] discriminator remote 20
[USG_A-bfd-session-ab] commit
[USG_A] ip route-static 0.0.0.0 0 10.1.1.2
[USG_A] ip route-static 0.0.0.0 0 20.1.1.2 preference 100 track bfd-session ab
C. [USG_B] bfd
[BSG_B] bfd ab bind peer-ip 10.1.1.1
[USG_B-bfd-session-ab] discriminator local 20
[USG_B-bfd-session-ab] discriminator remote 10
[USG_B-bfd-session-ab] commit
D. [USG_B] bfd
[BSG_B] bfd ab bind peer-ip 10.1.1.1
[USG_B-bfd-session-ab] discriminator local 10
[USG_B-bfd-session-ab] discriminator remote 20
[USG_B-bfd-session-ab] commit
NGFW_A and NGFW_B, NGFW_A and NGFW_C configure static routes respectively. NGFW_A -> NGFW_B is the primary link, and NGFW_A -> NGFW_C is the backup link. It is required that the traffic can be quickly switched to the backup link when the primary link fails; the traffic can be switched to the primary chromium road after the primary link is restored.
Which of the following configuration is correct? (Multiple Choice)

A. [USG_A] bfd
[USG_A] bfd ab bind peer-ip 10.1.1.2
[USG_A-bfd-session-ab] discriminator local 10
[USG_A-bfd-session-ab] discriminator remote 20
[USG_A-bfd-session-ab] commit
[USG_A] ip route-static 0.0.0.0 0 10.1.1.2 track bfd-session ab
[USG_A] ip route-static 0.0.0.0 0 20.1.1.2 preference 100
B. [USG_A] bfd
[USG_A] bfd ab bind peer-ip 10.1.1.2
[USG_A-bfd-session-ab] discriminator local 10
[USG_A-bfd-session-ab] discriminator remote 20
[USG_A-bfd-session-ab] commit
[USG_A] ip route-static 0.0.0.0 0 10.1.1.2
[USG_A] ip route-static 0.0.0.0 0 20.1.1.2 preference 100 track bfd-session ab
C. [USG_B] bfd
[BSG_B] bfd ab bind peer-ip 10.1.1.1
[USG_B-bfd-session-ab] discriminator local 20
[USG_B-bfd-session-ab] discriminator remote 10
[USG_B-bfd-session-ab] commit
D. [USG_B] bfd
[BSG_B] bfd ab bind peer-ip 10.1.1.1
[USG_B-bfd-session-ab] discriminator local 10
[USG_B-bfd-session-ab] discriminator remote 20
[USG_B-bfd-session-ab] commit
NGFW_A and NGFW_B, NGFW_A and NGFW_C configure static routes respectively. NGFW_A -> NGFW_B is the primary link, and NGFW_A -> NGFW_C is the backup link. It is required that the traffic can be quickly switched to the backup link when the primary link fails; the traffic can be switched to the primary chromium road after the primary link is restored.
Which of the following configuration is correct? (Multiple Choice)

A. [USG_A] bfd
[USG_A] bfd ab bind peer-ip 10.1.1.2
[USG_A-bfd-session-ab] discriminator local 10
[USG_A-bfd-session-ab] discriminator remote 20
[USG_A-bfd-session-ab] commit
[USG_A] ip route-static 0.0.0.0 0 10.1.1.2 track bfd-session ab
[USG_A] ip route-static 0.0.0.0 0 20.1.1.2 preference 100
B. [USG_A] bfd
[USG_A] bfd ab bind peer-ip 10.1.1.2
[USG_A-bfd-session-ab] discriminator local 10
[USG_A-bfd-session-ab] discriminator remote 20
[USG_A-bfd-session-ab] commit
[USG_A] ip route-static 0.0.0.0 0 10.1.1.2
[USG_A] ip route-static 0.0.0.0 0 20.1.1.2 preference 100 track bfd-session ab
C. [USG_B] bfd
[BSG_B] bfd ab bind peer-ip 10.1.1.1
[USG_B-bfd-session-ab] discriminator local 20
[USG_B-bfd-session-ab] discriminator remote 10
[USG_B-bfd-session-ab] commit
D. [USG_B] bfd
[BSG_B] bfd ab bind peer-ip 10.1.1.1
[USG_B-bfd-session-ab] discriminator local 10
[USG_B-bfd-session-ab] discriminator remote 20
[USG_B-bfd-session-ab] commit
Latest H12-731-ENU Dumps Valid Version with 206 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund

