Huawei H12-731-ENU HCIE-Security (Huawei Certified Internetwork Expert-Security) Online Training
Huawei H12-731-ENU Online Training
The questions for H12-731-ENU were last updated at Dec 26,2025.
- Exam Code: H12-731-ENU
- Exam Name: HCIE-Security (Huawei Certified Internetwork Expert-Security)
- Certification Provider: Huawei
- Latest update: Dec 26,2025
There are hundreds of people in a medium-sized enterprise network accessing the Internet through the company’s firewall, and the company has deployed a corporate portal website in the firewall DMZ. Which of the following criteria should be followed as an IT security officer for purchasing and deploying Internet access auditing products?
- A . Order No. 82 of the Ministry of Public Security
- B . ISO27002
- C . State Office issued No. 28
- D . NIST800-53
The centralized networking scheme of three servers, as shown in the figure, the administrator found that only one of the three Agile Controllers in the resource pool was alive.
In this case, which of the following descriptions is correct? (Multiple Choice)
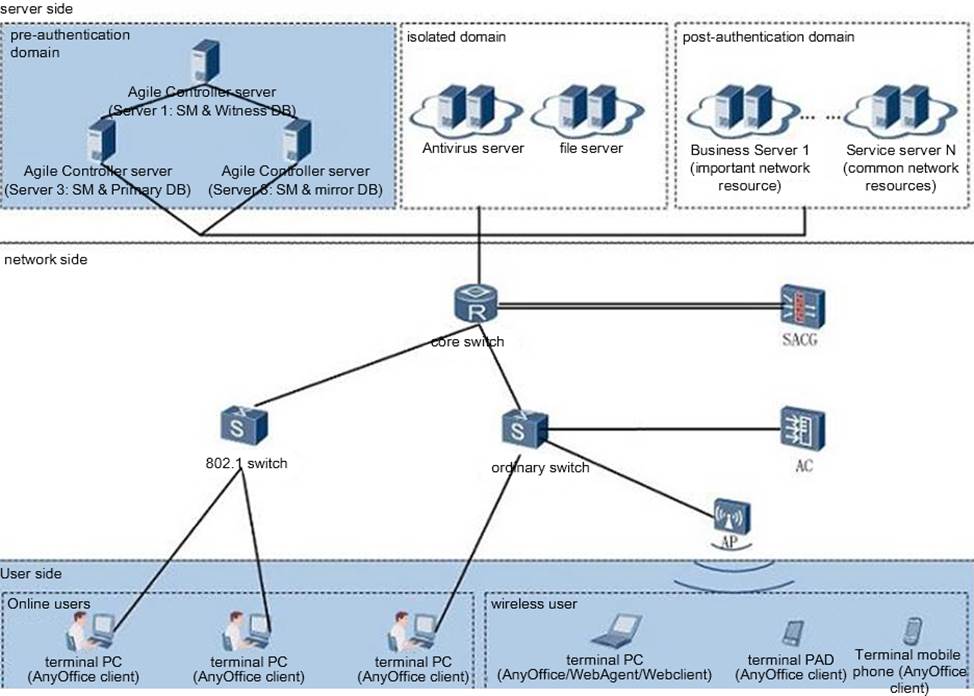
- A . All three database servers cannot work properly, and only one of the three Agile Controllers in the resource pool is alive. In this case, all Agile Controller services are transferred to the surviving Agile Controller and can operate normally, and terminal identity authentication, access control, software distribution, patch installation, and asset management will not be affected.
- B . After the Agile Controller is started, each Agile Controller will immediately read the database and save it on the local hard disk as a cache. If all databases become unavailable due to a failure, the Agile Controller will continue to maintain the operation of the Agile Controller service by using the cache saved at that time as the data source.
- C . At this point, you can try to restart the surviving Agile Controller, and repair the database server when restarting.
- D . At this time, the escape channel on the firewall has been opened.
For border network security, which of the following options are recommended for planning and deployment priorities? (Multiple Choice)
- A . Security Domain Isolation
- B . IPS real-time intrusion prevention
- C . Enable device virtualization
- D . Deploy a VPN
- E . Enable DDoS function
Regarding the description of NAT Server, which of the following is correct?
- A . If the public network address of the NAT Server and the corresponding public network interface address are in the same network segment, you do not need to configure black hole routing.
- B . If the public network address of the NAT Server and the corresponding public network interface address are not in the same network segment, you do not need to configure black hole routing.
- C . If the public network address of the NAT Server is an interface address, if a black hole route is configured for this address, service access to the firewall itself will be abnormal.
- D . The NAT Server cannot be configured on the virtual firewall for users of the root firewall.
Regarding the way SAC equipment accesses the network, which of the following descriptions are correct? (Multiple Choice)
- A . SACG equipment is required to communicate with the terminal at Layer 2.
- B . The SACG is usually side-mounted on the core switch device and uses policy routing to divert traffic.
- C . SACG supports side-hanging on non-Huawei devices.
- D . SACG devices are required to communicate with the Agile Controller at Layer 2.
The USG firewall is directly connected to other devices at Layer 3. During commissioning, it was found that the peer IP address directly connected from the firewall could not be pinged. It was confirmed that there was no problem with the peer device. What are the possible reasons? (Multiple Choice)
- A . Routing configuration error on the firewall
- B . The firewall interface is not added to the security domain
- C . The packet filtering from the firewall local to the corresponding security domain is not enabled
- D . The intra-domain packet filtering policy of the corresponding domain of the firewall is not enabled
What is the online certificate application method supported by firewall PKI?
- A . HTTP
- B . LDAP
- C . TFTP
- D . SCEP
- E . FTP
Which of the following description about SACG certification is correct? (Multiple Choice)
- A . SACG certification is generally used for existing wired networks.
- B . SACG certification is generally used for new wireless networks.
- C . SACG is generally deployed in a bypass mode without changing the original network topology.
- D . SACG essentially controls access users through 802.1X technology.
When the firewall uses the IPsec function, which protocols and ports need to be opened? (Multiple Choice)
- A . The protocols are IP packets with AH and ESP.
- B . UDP packets with source ports 500 and 4500.
- C . UDP packets with destination ports 500 and 4500.
- D . UDP packets with destination port 1701.
The firewall is deployed between the mobile terminal of the wireless user and the WAP gateway, the mobile terminal is in the trust zone, and the WAP gateway is in the untrust zone, and the following configurations are made:
[USG] ad 3000
[USG-acl-adv-3000] rule permit ip destination 202.10.10.2 0
[USG-acl-adv-3000] quit
[USG] fir-all zone trust
[USG-zone-trust] destination-nat 3000 address 200.10.10.2
[USG-zone-trust] quit
Which of the following descriptions are correct?
- A . This configuration can also be applied to server address mapping scenarios
- B . The command firewall zone trust should be changed to firewall interzone trust untrust outbound
- C . The firewall translates the destination address of the packet accessing the gateway address of 202.10.10.2 to 200.10.10.2
- D . The command firewall zone trust should be changed to firewall interzone untrust trust
Latest H12-731-ENU Dumps Valid Version with 206 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund

