Huawei H12-725_V4.0-ENU HCIP-Security V4.0 Online Training
Huawei H12-725_V4.0-ENU Online Training
The questions for H12-725_V4.0-ENU were last updated at Dec 17,2025.
- Exam Code: H12-725_V4.0-ENU
- Exam Name: HCIP-Security V4.0
- Certification Provider: Huawei
- Latest update: Dec 17,2025
As shown in the figure, which one of the following descriptions of dual-machine hot standby based on transparent mode is incorrect?
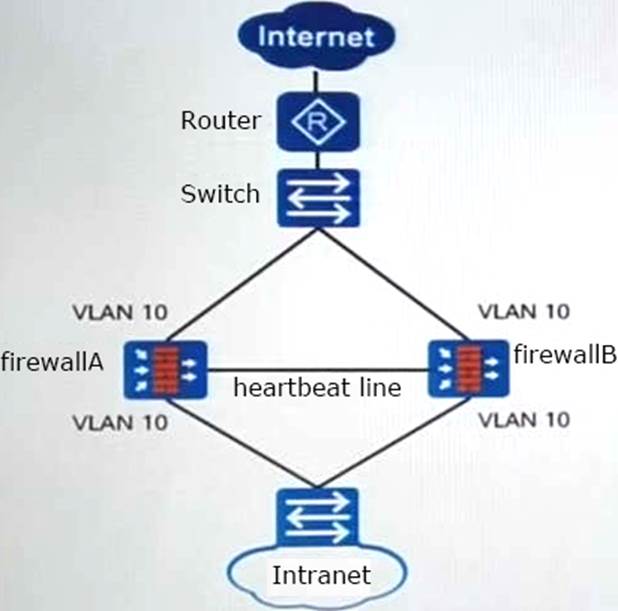
- A . Since the service interface of the firewall works on the second layer, it cannot run services related to IP addresses.
- B . In this network, the firewall is transparently connected to the original switch network without changing the network topology.
- C . It is recommended that this network work in load sharing mode to share user traffic
- D . By default, the status of any VLAN will not be adjusted based on the VGMP group status.
Which of the following descriptions about the characteristics of Eth-Trunk is incorrect?
- A . Eth-Trunk can be a Layer 2 interface or a Layer 3 interface.
- B . Eth-Trunk is a logical interface
- C . There are at least 2 Eth-Trunk member links
- D . There is at least 1 active Eth-Trunk link
Which of the following descriptions of virtual interfaces is incorrect?
- A . Mutual access between virtual systems is achieved through virtual interfaces
- B . The link layer and protocol layer of the virtual interface are always UP
- C . The virtual interface of the root system is Virtual-if1
- D . The format of the virtual interface is "Virtual-if+interface number"
Which of the following descriptions about the restrictions on the use of virtual systems is incorrect?
- A . As long as the system software is upgraded in the root system
- B . If the interface has been configured with an IP address, it will be cleared when assigned to a virtual
- C . Management ports cannot be assigned to virtual systems
- D . The virtual system administrator can log in to the device through the Console port.
When IPSec uses certificate authentication, it is necessary to verify the legitimacy of the peer certificate. Which of the following is not a factor that needs to be considered to verify the legitimacy of the certificate?
- A . Whether the certificate is applied for in the same way
- B . Whether the certificate is within the validity period
- C . Whether the certificate is located in the CRL repository
- D . Whether the certificate is issued by the same CA
As shown in the figure, IPSec tunnels are established between the headquarters and branches. To achieve IPSec traffic load sharing, at least how many IPSec tunnels need to be established?
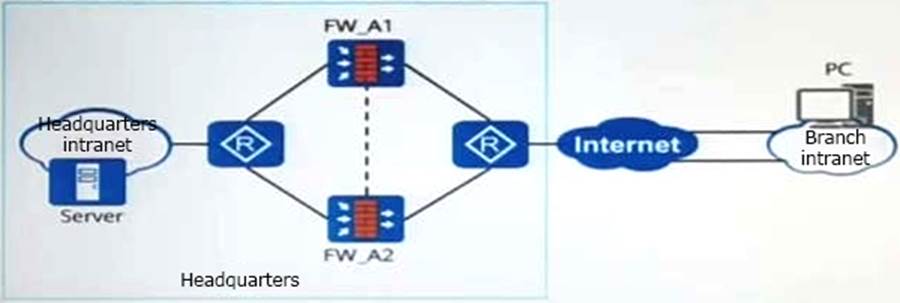
- A . 1
- B . 2
- C . 4
- D . 3
An enterprise has multiple branches. The exit IP address of the headquarters is fixed, but the exit IP addresses of the branches are random. An IPSec VPN needs to be established between the headquarters and branches. In order to reduce management and maintenance costs, which of the following is appropriate? How to configure IPSec VPN?
- A . Headquarters and branches adopt a point-to-point approach
- B . Both the headquarters and branches adopt the strategic model approach
- C . The headquarters adopts the policy template method, and the branches adopt the point-to-point method.
- D . The headquarters and branches adopt IKE v2 method
Which of the following descriptions about HTTP Flood defense is incorrect?
- A . If the free proxy used during the attack supports the redirection function, the basic mode defense will be ineffective.
- B . The source authentication defense method is to defend against HTTP
- C . Defense based on enhanced mode can determine whether the TTP access is initiated by a real user by asking the user to enter a verification code.
- D . Defense based on basic mode cannot effectively prevent access from non-browser clients
Which of the following descriptions of cleaning centers is incorrect?
- A . Back-injection methods include: policy routing back-injection, static route back-injection, VPN back-injection and Layer 2 back-injection.
- B . The cleaning device supports rich and flexible attack prevention technologies, but cannot defend against CC attacks and ICMP Flood attacks.
- C . There are two methods of traffic diversion: static traffic diversion and dynamic traffic diversion.
- D . The cleaning center completes functions such as diversion and cleaning of abnormal traffic, and reinjection of cleaned traffic.
When a firewall performs email filtering, which of the following email transfer protocols does it support?
- A . SMTPS
- B . SMTP
- C . P0P3
- D . IMAP
Latest H12-725_V4.0-ENU Dumps Valid Version with 600 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund

