Huawei H12-725_V4.0-ENU HCIP-Security V4.0 Online Training
Huawei H12-725_V4.0-ENU Online Training
The questions for H12-725_V4.0-ENU were last updated at Dec 13,2025.
- Exam Code: H12-725_V4.0-ENU
- Exam Name: HCIP-Security V4.0
- Certification Provider: Huawei
- Latest update: Dec 13,2025
Which of the following descriptions of Web Link in web proxy is incorrect?
- A . There is a page compatibility issue, and images may be misaligned.
- B . The URL will not be rewritten, which will expose the real address of the intranet server.
- C . There are certain security risks
- D . Depends on IE controls and cannot be used normally in non-IE environments
Which of the following descriptions of smart DNS is incorrect?
- A . By configuring the smart DNS function, the firewall can intelligently modify the resolution address in the DNS response message so that the user can obtain the most appropriate resolution address, that is, an address that belongs to the same ISP network as the user.
- B . Intelligent DNS supports weighted polling to achieve link load balancing
- C . Smart DNS does not need to be combined with other technologies and can be used alone
- D . Smart DNS is divided into two scenarios: single-server smart DNS and multi-server smart DNS.
Each bandwidth policy that references a bandwidth channel is independently constrained by the bandwidth channel, that is, traffic that meets the matching conditions of the bandwidth policy has exclusive access to the maximum bandwidth resource.
Which of the following options belongs to this bandwidth channel reference method?
- A . Broadband sharing
- B . Bandwidth multiplexing
- C . Broadband exclusive
- D . Dynamic equalization
Which of the following descriptions about dual-machine hot standby is incorrect?
- A . In a load-sharing network, the configuration command can be backed up from "Configure Standby Device" to "Configure Primary Device"
- B . In an active-standby backup network, configuration commands and status information are backed up from the active device to the standby device.
- C . In load-sharing mode networking, traffic is processed by two devices, which can bear greater peak traffic than active-standby backup mode or mirroring mode networking.
- D . In a load-sharing network, both firewalls are active devices. Therefore, if the two active devices are allowed to back up each other’s commands, it may cause the problems of mutual overwriting or conflict between the commands of the two devices.
As shown in the figure, the primary and secondary backup networking based on VRRP is wrong. In the following description of this scenario, which one is wrong?
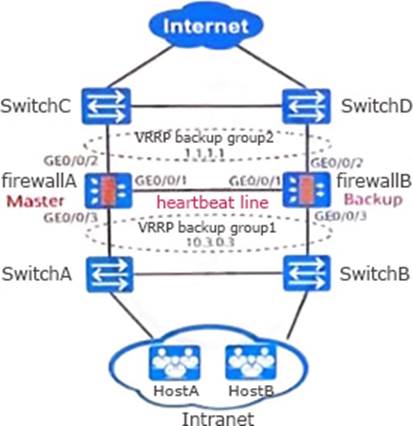
- A . In order to ensure the consistency of link switching, the firewall implements device status management based on VGMP groups.
- B . The configuration and status information of firewall A is backed up to firewall B in real time through the GE0/0/3 interface.
- C . Dual-machine hot backup can improve network reliability
- D . The firewall GE0/0/1 interface is the heartbeat interface, and the connected line is the heartbeat line.
In which of the following access authentication methods, the terminal must obtain an IP address before authentication?
- A . 802.1×Authentication
- B . Portal
- C . MAC authentication
- D . MAC bypass authentication
In Huawei’s admission control solution, after the access device receives the CoA-Roquest message or DM-Requst message from the RADTUS server, which RADIUS attribute in the message is used to identify the user?
- A . called-Station-ld
- B . Filter-ld
- C . NAS-IP-Address
- D . calling-Station-ld
In the 802.1X authentication scenario, the access device directly encapsulates the EAPoL packet sent by the 802.1X client into a RADIUS packet, without processing the data in the EAP.
Which of the following authentication methods meets the above description?
- A . EAP termination
- B . MAC-based authentication
- C . Interface-based authentication
- D . EAP relay
Common Vulnerability Scoring System (CVSS) is a widely used open standard for vulnerability scoring and adopts a modular scoring system. Which of the following does not include?
- A . Environmental dimension
- B . Time dimension
- C . Basic dimensions
- D . Spatial dimensions
Malicious URLs refer to URLs that contain malicious information. Which of the following is not the source of malicious URLs?
- A . Malicious URLs reported by the sandbox
- B . Malicious URLs reported by the intrusion prevention function
- C . URLs included in local reputation
- D . Malicious URLs reported by the anti-virus function
Latest H12-725_V4.0-ENU Dumps Valid Version with 600 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund

