Huawei H12-725_V4.0-ENU HCIP-Security V4.0 Online Training
Huawei H12-725_V4.0-ENU Online Training
The questions for H12-725_V4.0-ENU were last updated at Dec 19,2025.
- Exam Code: H12-725_V4.0-ENU
- Exam Name: HCIP-Security V4.0
- Certification Provider: Huawei
- Latest update: Dec 19,2025
Which of the following descriptions about guaranteed bandwidth and maximum bandwidth is incorrect?
- A . Guaranteed bandwidth and maximum bandwidth can be set on a per-IP/user basis
- B . If the traffic is greater than the maximum bandwidth, directly discard the traffic exceeding the maximum bandwidth.
- C . If the traffic is less than the guaranteed bandwidth, this part of the traffic will compete freely with the same type of traffic in other bandwidth channels on the outbound interface for bandwidth resources.
- D . Guaranteed bandwidth and maximum bandwidth settings for IP or users can achieve more detailed bandwidth restrictions
Which of the following descriptions about deploying a firewall virtual system is incorrect?
- A . A resource class can be bound to multiple virtual systems at the same time
- B . You can view the created virtual systems and allocated resources in the "Virtual System List"
- C . Configure the resource class first, and then enable the virtual system for binding
- D . Resource class r0 is bound to the root system by default and cannot be deleted or modified.
As shown in the figure, the firewall load balancing network is used, and the upstream and downstream devices are switches.
Which of the following descriptions of the firewall VGMP group status in this scenario is correct?
- A . Firewall A: Active, Firewall B: Standby
- B . Firewall A: Master, Firewall B: Backup
- C . Firewall A: Master, Firewall B: Master
- D . Firewall A: Active, Firewall B: Active
Which of the following is not part of the consistency check of dual-machine hot standby?
- A . Interface address
- B . NAT configuration
- C . Bandwidth Policy
- D . Security policy
As shown in the figure, the firewall is deployed as a gateway dual-machine hot standby, and the upstream and downstream devices are switches.
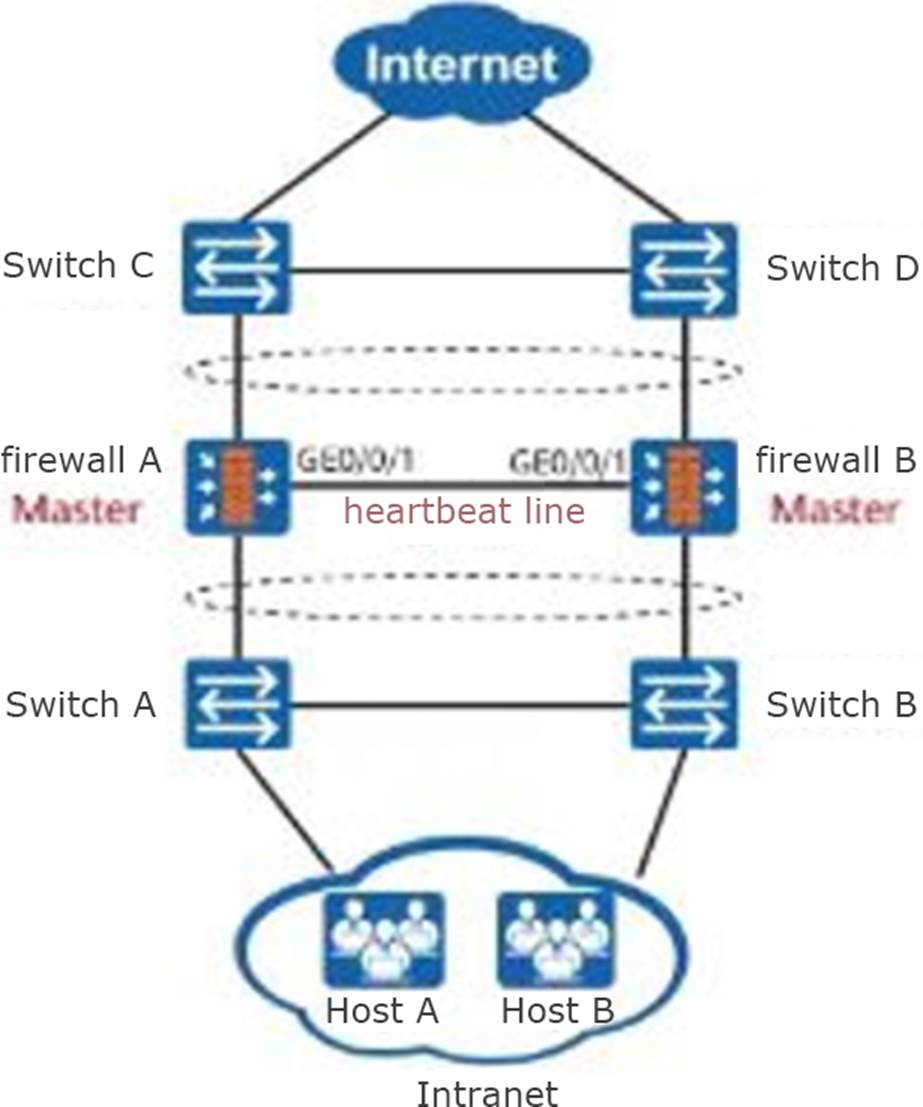
To achieve round-trip traffic load balancing, at least how many VRRP backup groups need to be configured in this scenario?
- A . 4
- B . 6
- C . 2
- D . 3
When a visitor accesses the corporate network through Portal authentication, in order to ensure a good visitor experience, the visitor is required to open the wireless network range for a short period of time. When re- entering, there is no need to enter the username and password again and they can directly access the network.
Which of the following access methods can meet the above requirements?
- A . MAC bypass authentication
- B . MAC authentication
- C . MAC priority Portal authentication
- D . 802.1X authentication
When using an LDAP server as the authentication server, if you want to perform user authentication, which of the following operations needs to be performed on the data of the LDAP server?
- A . Query class
- B . Delete class
- C . Writing class
- D . Update class
When using an LDAP server as the authentication server, which of the following protocols is used for the interaction between the device and the server?
- A . RADIUS protocol
- B . HTTP protocol
- C . LDAP protocol
- D . EAP protocol
If you want to control users’ forum postings, user logins, etc., which of the following HTTP behavior controls should be configured?
- A . POST operation
- B . Redirect
- C . File upload
- D . File download
A user uses SSL to access network resources on the intranet. The administrator has enabled file sharing and web proxy services for the user, and has allowed the traffic of the service on the firewall. However, after the user enters the address of the virtual gateway on the PC, the web page fails. I cannot see the list of file shares and web proxies. Which of the following options may cause this failure?
- A . The virtual gateway’s external NAT port is wrong.
- B . Has the virtual IP address been obtained from the virtual network card of the user’s PC?
- C . The administrator does not have the authorization to configure file sharing and web proxy for the user
- D . The route between the firewall and the client is unreachable
Latest H12-725_V4.0-ENU Dumps Valid Version with 600 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund

