Huawei H12-725_V4.0-ENU HCIP-Security V4.0 Online Training
Huawei H12-725_V4.0-ENU Online Training
The questions for H12-725_V4.0-ENU were last updated at Dec 13,2025.
- Exam Code: H12-725_V4.0-ENU
- Exam Name: HCIP-Security V4.0
- Certification Provider: Huawei
- Latest update: Dec 13,2025
Which of the following parameters is not a condition for global routing policy classification?
- A . Bandwidth
- B . Port number
- C . Quality
- D . Weight
In a NAT traversal scenario, if a NAT device is detected, the destination port number of the ISAKMP message will become which of the following?
- A . 4500
- B . 51
- C . 50
- D . 500
Which of the following descriptions about GRE over IPSec is incorrect?
- A . The IP header added during the IPSec encapsulation process, that is, the source address is the interface address of the IPSec gateway to which the IPSec security policy is applied, and the destination address is the interface address of the IPSec peer to which the IPsec security policy is applied.
- B . When gateways use GRE over IPSec to connect, GRE encapsulation is performed first, and then IPSec encapsulation is performed.
- C . The IP header added during the GRE encapsulation process, that is, the source address is the source address of the IPSec tunnel, and the destination address is the destination address of the IPSec tunnel.
- D . The data flow that IPSec needs to protect is the data flow from the GRE starting point to the GRE ending point.
Which of the following descriptions of the characteristics of SSL VPN is incorrect?
- A . SSL VPN supports few authentication types and is difficult to integrate with the original identity authentication system.
- B . SSL VPN can support various IP applications
- C . SSL VPN can parse intranet resources to the application layer and publish applications in a granular manner
- D . Since the SSL VPN login method uses a browser, the automatic installation and configuration of the client is realized, so that users can quickly log in with their devices anytime and anywhere, and it also relieves the pressure of network administrators in maintaining the client.
Which of the following is not an intranet resource that SSL VPN can provide to mobile office users?
- A . File resources
- B . UDP resources
- C . Web resources
- D . IP resources
As shown in the figure, which of the following is the UDP defense principle shown in the figure?
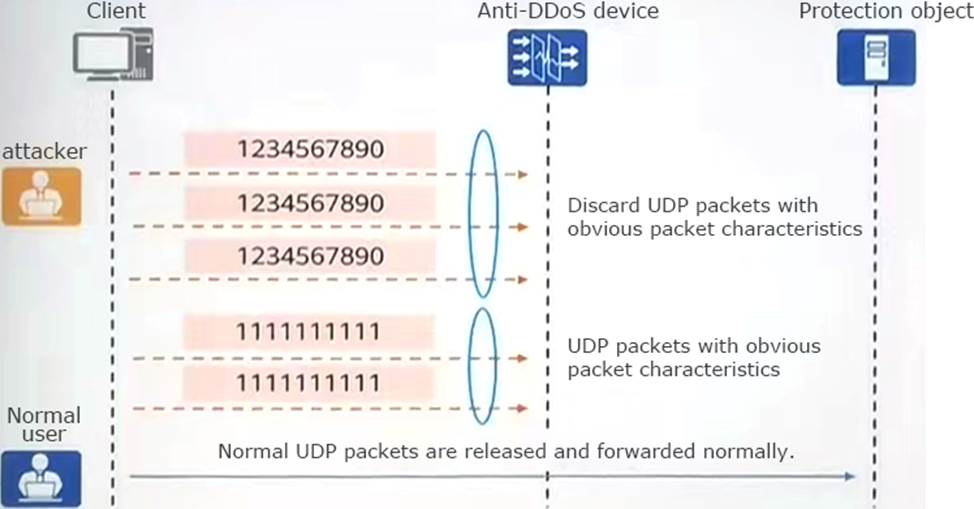
- A . Fingerprint learning
- B . Load Check
- C . Relevant defense
- D . Session check
Which of the following is a method to prevent Tracert packet attacks?
- A . Discard IP packets with time offset
- B . Discard the detected ICMP messages or UDP messages that have expired, or the destination port is unreachable.
- C . Users can configure the maximum length of ICP packets allowed to pass according to actual network needs. When the length of the actual IP packet exceeds this value, the packet will be discarded.
- D . Discard ICMP unreachable messages and record attack logs
Which of the following is not the responsibility of the Anti-DDos defense system management center?
- A . Security report analysis
- B . Device Management
- C . Issue defense strategies
- D . Carry out traffic diversion
Which of the following descriptions of URL classification is incorrect?
- A . Custom URL classification requires manual configuration by the administrator.
- B . The predefined URL categories are preset at the factory and do not require the administrator to manually load them.
- C . Predefined URL categories cannot be created, deleted, or renamed
- D . Predefined URL categories have higher priority than custom URL categories
Which of the following descriptions of keywords in content filtering is incorrect?
- A . Regular expression matching is more flexible and efficient than text matching, but the configuration needs to follow the regular expression rules.
- B . Keywords include predefined keywords and custom keywords
- C . Predefined keywords are keywords that are manually defined by the administrator and can be identified
- D . The minimum length of keywords that can be matched by text and regular expressions is 3 bytes.
Latest H12-725_V4.0-ENU Dumps Valid Version with 600 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund

