Huawei H12-725_V4.0-ENU HCIP-Security V4.0 Online Training
Huawei H12-725_V4.0-ENU Online Training
The questions for H12-725_V4.0-ENU were last updated at Dec 29,2025.
- Exam Code: H12-725_V4.0-ENU
- Exam Name: HCIP-Security V4.0
- Certification Provider: Huawei
- Latest update: Dec 29,2025
Which of the following descriptions of BFD detection characteristics is incorrect?
- A . Reduce application interruption time and improve network reliability
- B . Establish a session between the two devices to monitor the bidirectional forwarding path
- C . Provide a detection time of less than 1 second to speed up network convergence
- D . Fault detection can only be performed on the bidirectional forwarding path of the directly connected physical link between network devices.
The figure shows the defense principle of HTTP Flood. Which source detection technology is shown in the figure?
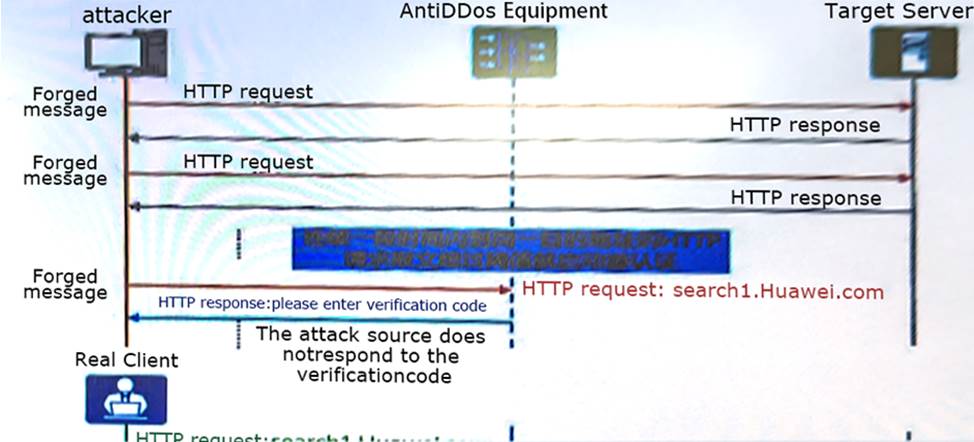
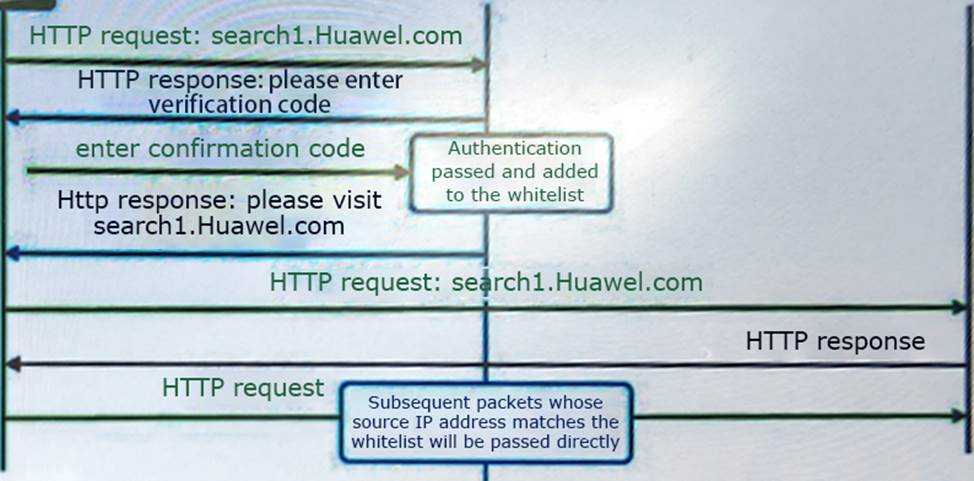
- A . 302 redirect mode
- B . Basic mode
- C . URI monitoring
- D . Enhanced mode
Which of the following descriptions of abnormal file type identification results is incorrect?
- A . The file type cannot be recognized means that the file type cannot be recognized and there is no file extension.
- B . Unrecognized file type means that neither the file type nor the file extension can be recognized.
- C . File extension mismatch means that the file type and file extension are inconsistent.
- D . File corruption refers to the inability to identify the file type due to the file being damaged.
To check whether there is an abnormal task plan (not set by the user) on the Linux host, which of the following commands can be used?
- A . crontab -u mysql
- B . crontab -e
- C . crontab -r
- D . crontab -l
According to the provisions of the "National Cyber Security Incident Emergency Plan", when national secret information, important sensitive information and relevant educational records are lost or stolen, tampered with or counterfeited, and pose a particularly serious threat to national security and social stability Which level of emergency response should be initiated?
- A . First level response
- B . Secondary response
- C . Special response
- D . Level 3 response
According to the provisions of the "National Cyber Security Incident Emergency Plan", when national secret information, important sensitive information and relevant educational records are lost or stolen, tampered with or counterfeited, and pose a particularly serious threat to national security and social stability Which level of emergency response should be initiated?
- A . First level response
- B . Secondary response
- C . Special response
- D . Level 3 response
According to the provisions of the "National Cyber Security Incident Emergency Plan", when national secret information, important sensitive information and relevant educational records are lost or stolen, tampered with or counterfeited, and pose a particularly serious threat to national security and social stability Which level of emergency response should be initiated?
- A . First level response
- B . Secondary response
- C . Special response
- D . Level 3 response
According to the provisions of the "National Cyber Security Incident Emergency Plan", when national secret information, important sensitive information and relevant educational records are lost or stolen, tampered with or counterfeited, and pose a particularly serious threat to national security and social stability Which level of emergency response should be initiated?
- A . First level response
- B . Secondary response
- C . Special response
- D . Level 3 response
According to the provisions of the "National Cyber Security Incident Emergency Plan", when national secret information, important sensitive information and relevant educational records are lost or stolen, tampered with or counterfeited, and pose a particularly serious threat to national security and social stability Which level of emergency response should be initiated?
- A . First level response
- B . Secondary response
- C . Special response
- D . Level 3 response
Latest H12-725_V4.0-ENU Dumps Valid Version with 600 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund

