Huawei H12-725_V4.0-ENU HCIP-Security V4.0 Online Training
Huawei H12-725_V4.0-ENU Online Training
The questions for H12-725_V4.0-ENU were last updated at Jan 04,2026.
- Exam Code: H12-725_V4.0-ENU
- Exam Name: HCIP-Security V4.0
- Certification Provider: Huawei
- Latest update: Jan 04,2026
IPS devices work based on specific intrusion prevention mechanisms. Which of the following is the correct ranking of intrusion prevention mechanisms?
- A . Feature matching->Reorganize application data->Protocol identification and protocol parsing->Response processing
- B . Reorganize application data->Protocol identification and protocol parsing->Feature matching->Response processing
- C . Reorganize application data->Feature matching->Protocol identification and protocol parsing->Response processing
- D . Protocol identification and protocol parsing->Reorganize application data->Feature matching->Response processing
When using iMaster NCE-Campus as the Portal server, in order to allow iMaster NCE-Campus to match the corresponding Portal page according to the user’s IP address.
When configuring the URL template on the access device, which of the following URL parameters need to be configured?
- A . ssid
- B . device-mac
- C . user-mac
- D . user-ipaddress
To implement the access control function through Huawei iMaster NCE-Campus controller, which of the following is not required for authentication and authorization configuration?
- A . Certification results
- B . Authorization results
- C . Certification rules
- D . Authorization rules
Which of the following descriptions about 802.1× authentication is incorrect?
- A . In EAP termination mode, EAP messages are directly encapsulated into RADIUS
- B . The 802.1X authentication method is divided into EAP relay method and EAP termination method. In comparison, EAP relay method supports more authentication methods.
- C . The 802.1X authentication system uses the EAP protocol to realize information exchange between the client, device and authentication server.
- D . In the 802.1X authentication method, the client must support the 802.1x protocol.
Which of the following is not a function of the Anti-DDoS Management Center?
- A . Performance management
- B . Strategic Management
- C . Alarm management
- D . Traffic detection
Which of the following descriptions of the network expansion process in SSL VPN is incorrect?
- A . The remote user’s local PC will automatically generate a virtual network card. The virtual gateway randomly selects an IP address from the address pool and assigns it to the remote user’s virtual network card.
- B . The remote user sends a service request message to the server on the enterprise intranet, and the message reaches the virtual gateway through the SSL VPN tunnel.
- C . In reliable transmission mode, SSL VPN uses SSL protocol to encapsulate messages and uses UDP protocol as the transmission protocol
- D . After the network expansion function is triggered, an SSL VPN tunnel needs to be established between the remote user and the virtual gateway first.
Use IKE v1 main mode to establish an IPSec VPN. After detecting the presence of a NAT device, which of the following ISAKMP messages will be followed by port number conversion?
- A . Message 5
- B . Message 6
- C . Message 3
- D . Message 4
As shown in the figure, enterprise A and enterprise B need to communicate securely, and an IPSec tunnel is established between firewall A and firewall B. Which of the following security protocols and encapsulation modes can meet the needs of this scenario?
- A . AH, tunnel mode
- B . ESP, tunnel mode
- C . ESP, transmission mode
- D . AH+ESP, transmission mode
The network architecture of an enterprise is as shown in the figure below. Portal authentication is deployed on SW2. Its authentication-free template is as shown in the figure. Which of the following descriptions is correct?
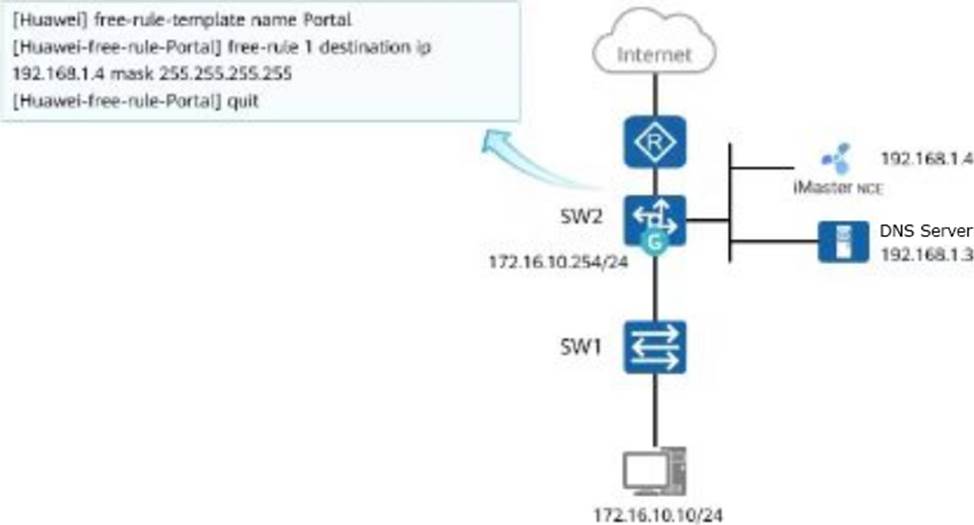
- A . At this time, the terminal can open the authentication interface.
- B . At this time, the terminal can ping its own gateway.
- C . At this time, the terminal can perform DNS resolution normally.
- D . At this time, the terminal can be redirected to the authentication interface by entering the URL in the browser.
Which of the following descriptions about virtual system resource allocation is incorrect?
- A . Unreasonable resource allocation may cause other virtual systems to be unable to obtain resources and the business to be unable to operate normally.
- B . Quota resources automatically allocate a fixed number of resources directly according to system specifications.
- C . When the administrator manually allocates resources to the virtual system, he first needs to configure the C resource class and specify the guaranteed value and maximum value of each resource item in the resource class, and then bind the source class to the virtual system
- D . Each virtual system can share and seize the entire machine resources, but they can be allocated manually.
Latest H12-725_V4.0-ENU Dumps Valid Version with 600 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund

