Huawei H12-723-ENU HCIP-Security-CTSS(Huawei Certified ICT Professional -Constructing Terminal Security System) Online Training
Huawei H12-723-ENU Online Training
The questions for H12-723-ENU were last updated at Dec 16,2025.
- Exam Code: H12-723-ENU
- Exam Name: HCIP-Security-CTSS(Huawei Certified ICT Professional -Constructing Terminal Security System)
- Certification Provider: Huawei
- Latest update: Dec 16,2025
Which of the following are correct about 802.1X access process? (Multiple choices)
- A . Throughout the authentication process, the terminal exchanges information through the server and EAP packets.
- B . The terminal exchanges EAP packets with the 802.1X switch. The 802.1X switch and the server use Radius packets exchange information.
- C . 802.1X authentication does not require security policy checks.
- D . Use MD5 algorithm to verify the information.
BYOD solution provide products and systems cover terminals, networks, security, application and management, include serialized BYOD devices, wireless network systems, network access security, VPN gateways, terminal security client software, authentication systems, mobile device management (MDM), mobile eSpace UC, etc.
- A . True
- B . False
Which of the following is correct for terminal Wi-Fi push order?

- A . 1-2-3-4
- B . 4-2-3-1
- C . 3-2-1-4
- D . 2-3-1-4
Which of the following options is correct for PKI process sequence?
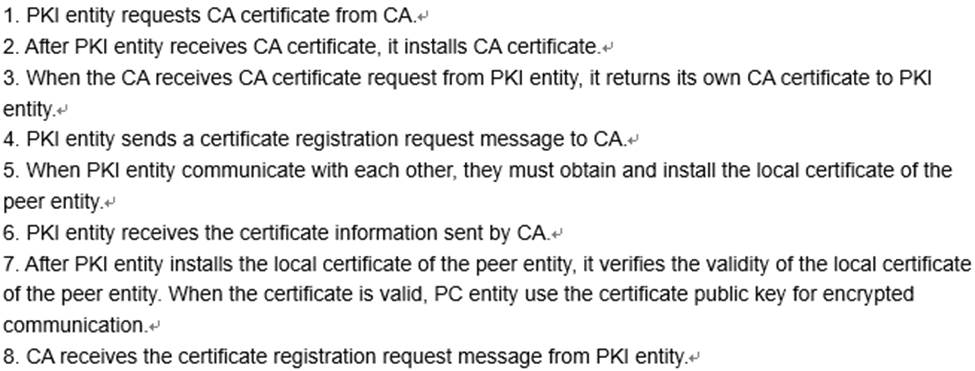
A. 1-3-5-4-2-6-7-8
B. 1-3-5-6-7-4-8-2
C. 1-3-2-7-6-4-5-8
D. 1-3-2-4-8-6-5-7
Aopt user isolation technology in WLAN networking environment, which of the following statements is wrong?
- A . User isolation between groups means that users in different groups can’t communicate with each other, and internal users in the same group can communicate
- B . Isolation in user groups means that users in the same group can’t communicate with each other
- C . User isolation function means that Layer 2 packets associated with all wireless users on the same AP can’t forward packets to each other.
- D . Group isolation and isolation between groups can’t be used at the same time
When use local guest account authentication, Portal authentication is usually used to push the authentication page to the visitor.
Before the user authentication, when the access control device receives HTTP request from the user and the resource is not the Portal server authentication URL, how does the admission control device handle it?
- A . Drop the packet
- B . URL address redirect to Portal authentication page
- C . Direct release
- D . Send authentication information to the authentication server
The administrator issues notices to users through the form of announcements, such as the latest software and patch installation notices, etc. Which of the following options is wrong?
- A . You can issue an announcement by department.
- B . The endpoint must have proxy client installed to receive announcements.
- C . If the system issues an announcement and the proxy client is not online, it will not receive the announcement information after going online.
- D . You can issue an announcement by account number.
When manage guest accounts, you need to create guest account policy and set account creation method. Which of the following descriptions is incorrect for account creation?
- A . When you add accounts individually, you can select individual creation.
- B . If the number of users is large, you can create them in batches.
- C . If the number of users is large, you can choose database synchronization.
- D . Self-registration can be used to facilitate management and enhance the user experience.
In WIDS-enabled WLAN network, which of the following statements is correct regarding the determination of illegal devices?
- A . All Ad-hoc devices will be directly identified as illegal devices
- B . AP that are not connected to this AC are illegal AP
- C . STA that are not connected to this AC are illegal STA
- D . STA that are not connected to this AC must check whether the access AP is valid
When deploy wired 802.1X authentication, if the admission control device is deployed at the convergence layer, this deployment method has features such as high security performance, multiple management devices and complicated management.
- A . True
- B . False

