Huawei H12-721_V3.0-ENU HCIP-Security-CISN V3.0 Online Training
Huawei H12-721_V3.0-ENU Online Training
The questions for H12-721_V3.0-ENU were last updated at Feb 26,2025.
- Exam Code: H12-721_V3.0-ENU
- Exam Name: HCIP-Security-CISN V3.0
- Certification Provider: Huawei
- Latest update: Feb 26,2025
Which statements about virtual interfaces are correct? (Multiple choice)
- A . The virtual interface may cause the protocol layer DOWN because the IP address is not configured.
- B . The virtual interface must be added to the security zone to work.
- C . The virtual interface may not be configured with an IP address.
- D . A virtual interface is a logical interface for which an IP address needs to be configured.
To ensure that traffic transmission is not affected by server or link failures, the administrator has configured the health check of the link, but after the configuration is completed, it is found that the status of the health check is still Down. What are the possible reasons? (Multiple choice)
- A . The TRUE end device has not released the corresponding protocol and port
- B . The security policy does not allow traffic
- C . The link for the health check fails
- D . The health check is not called on the interface
Regarding the configuration commands in the intelligent routing below, which of the following are correct? (Multiple choice)
#
multi-interface
mode priority-of-link-quality
priority-of-link-quality parameter delay jitter loss
priority-of-link-quality protocol tcp-simple
add interface GigabitEthernet1/0/1
add interface GigabitEthernet1/0/2
- A . The bandwidth-based load sharing method is used
- B . The parameters of link quality detection are delay, jitter and packet loss rate
- C . The TCP protocol used for detection
- D . 3 links are selected for load balancing
The following figure shows the application scenario of L2TP over IPSec. The client uses the pre-shared-key method for IPSec authentication. How should the IPSec security policy be configured on the LNS side? (Multiple choice)
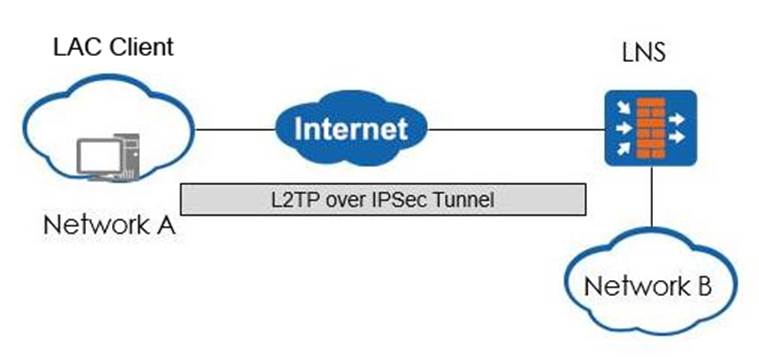
- A . Negotiate using IKE v1 main mode
- B . Negotiate using IKE v2
- C . Configure IPSec security policy
- D . Configure IPSec Policy Template
What algorithm can session persistence be based on?
- A . Least Connection algorithm
- B . Source IP hash algorithm
- C . Simple polling algorithm
- D . Weighted Round Robin algorithm
In order to prevent applications such as Email and ERP from being affected during normal working hours, an enterprise hopes that the minimum bandwidth available for such traffic is not less than 60Mbps. Which of the following configuration meets the requirements?
- A . time-range work_time
period-range 09: 00: 00 to 18: 00: 00 working-day
traffic-policy
profile profile_email
bandwidth guaranteed-bandwidth whole both 60000
rule name policy_email
source-zone trust
destination-zone untrust
application app BT
application app YouKu
time-range work_time
action qos profile profile_email - B . time-range work_time
period-range 00: 00: 00 to 09: 00: 00 working-day
traffic-policy
profile profile_email
bandwidth guaranteed-bandwidth whole both 60000
rule name policy_email
source-zone trust
destination-zone untrust
application app LotusNotes
application app OWA
time-range work_time
action qos profile profile_email - C . time-range work_time
period-range 09: 00: 00 to 18: 00: 00 working-day
traffic-policy
profile profile_email
bandwidth guaranteed-bandwidth whole both 60000
rule name policy_email
source-zone trust
destination-zone untrust
application app LotusNotes
application app OWA
time-range work_time
action qos profile profile_email - D . time-range work_time
period-range 09: 00: 00 to 18: 00: 00 working-day
traffic-policy
profile profile_email
bandwidth maximum-bandwidth whole both 60000
rule name policy_email
source-zone trust
destination-zone untrust
application app LotusNotes
application app OWA
time-range work_time
action qos profile profile_email
Which of the following information is included in the main mode negotiation process in the first phase of IKE v1 negotiation? (Multiple choice)
- A . IKE Proposal Set
- B . IPSec Proposal Set
- C . DH key exchange public information
- D . Identity information of both parties
Which of the following log categories does the firewall log, content log, policy hit log, mail filtering log, URL filtering log and audit log all belong to?
- A . Session log
- B . Packet Loss Log
- C . Business log
- D . System log
As shown in the figure below, the firewall GE0/0/0 interface is directly connected to the PC host through a network cable.
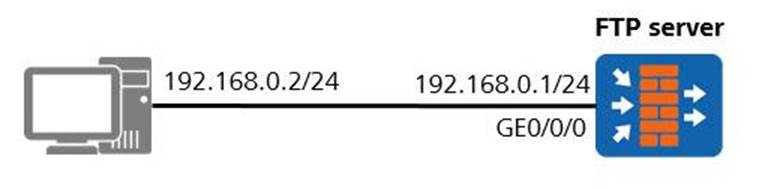
Which of the following commands can work together to complete the backup operation of the system configuration file vrpcfg.cfg? (Multiple choice)
- A . Complete the following commands on the firewall:
[USG] ftp server enable
Info: Start FTP server
[USG] aaa
[USG-aaa] local-user ftpuser password simple Ftppass#
[USG-aaa] local-user ftpuser service-type ftp
[USG-aaa] local-user ftpuser ftp-directory hda1:/ - B . Complete the following commands on the firewall:
<USG> ftp 192.168.0.2
Trying 192.168.0.2
Press CTRL+K to abort
Connected to 192.168.0.2.
220 FTP Server ready.
User ( 192.168.0.2: ( none)): ftpuser
331 Password required for ftpuser.
Password:
230 User ftpuser logged in.
[ftp] get vrpcfg .cfg - C . Complete the following commands on the PC:
C:Documents and SettingsAdministrator> ftp 192.168.0.1
Connected to 192.168.0.1.
220 FTP service ready.
User ( 192.168.0.1: ( none)): ftpuser
331 Password required for ftpuser.
Password:
230 User logged in.
ftp> get vrpcfg.cfg - D . Complete the following commands on the PC:
C:Documents and SettingsAdministrator> ftp 192.168.0.1
Connected to 192.168.0.1.
220 FFP service ready.
User ( 192.168.0.1: ( none)): ftpuser
331 Password required for ftpuser.
Password:
230 User logged in.
ftp> put vrpcfg.cfg
Which of the following statements about IPsec is false?
- A . In transport mode, ESP does not validate IP packet headers
- B . AH can only verify data packets and cannot encrypt them
- C . ESP can support NAT traversal
- D . AH protocol uses 3DES algorithm for data authentication
Latest H12-721_V3.0-ENU Dumps Valid Version with 342 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund

