Huawei H12-711_V4.0-ENU HCIA-Security V4.0 Exam Online Training
Huawei H12-711_V4.0-ENU Online Training
The questions for H12-711_V4.0-ENU were last updated at Dec 11,2025.
- Exam Code: H12-711_V4.0-ENU
- Exam Name: HCIA-Security V4.0 Exam
- Certification Provider: Huawei
- Latest update: Dec 11,2025
Which of the following attacks is not a special message attack?
- A . ICMP redirect message attack
- B . ICMP unreachable message attack
- C . IP address scanning attack
- D . Oversized ICMP message attack
The attacker sends a SYN message with the same source address and destination address, or the source address is a loopback address, to the target host (the source port and destination port are the same), causing the attacker to send a SYN-ACK message to its own address.
What kind of attack does this behavior belong to?
- A . SYN flood attack
- B . TCP spoofing attack
- C . Smurf attack
- D . Land attack
Which of the following is not the default security zone of the firewall?
- A . Untrust Zone
- B . DMZ Zone
- C . Trust Zone
- D . ISP Zone
As shown in the figure, there are two Server Map entries generated after configuring NAT Server. Regarding the information presented in the figure, which of the following descriptions is incorrect?
*Type: Nat Server. ANY→1.1.1.1[192.168.1.1] Type: Nat Server Reverse. 192.168.1.1[1.1.1.1] →ANY
- A . The second Server Map function is that when 192.168.1.1 accesses any address, the source address will be converted to 1.1.1.1 after passing through the firewall.
- B . The function of the first Server Map is that when any address accesses 192.168.1.1, the destination IP will be converted to 1.1.1.1 after passing through the firewall.
- C . The Server Map with the Reverse logo can be deleted using the command.
- D . These two Server Map entries are static, that is, after the NAT Server is configured, the two Server Maps will be automatically generated and will exist permanently.
Which of the following options belongs to Layer 2 VPN technology?
- A . SSL VPN
- B . L2TP VPN
- C . GRE VPN
- D . IPsec VPN
The administrator connects to the firewall through the G1/0/0 interface (the interface has been added to the Trust zone). If the administrator is allowed to log in to the firewall through G1/0/0 for configuration management, how should the administrator configure the traffic allowed in the security policy? direction?
- A . Allow traffic from Trust Zone to Untrust Zone
- B . Allow traffic from Trust Zone to Local Zone
- C . Release traffic from Local Zone to Local Zone
- D . Allow traffic from Trust Zone to Trust Zone
Which of the following options is not a certificate saving file format supported by USG6000 series devices?
- A . PKCS#12
- B . DER
- C . PEM
- D . PKCS#
As shown in the figure, when using the Client – Initiated VPN method to establish an L2TP VPN, which of the following is the destination of the PPP packet?
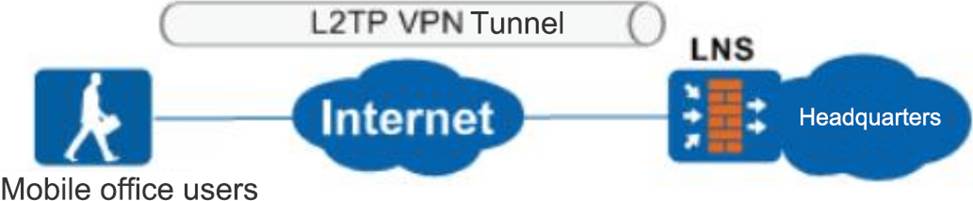
- A . Access users
- B . LNS
- C . LAC
- D . Server
When the company network administrator configures dual-machine hot backup, configure the status of VRRP backup group 1 as Active, and configure the virtual IP address as 10.1.1.1/24, then the command that needs to be typed in the blank space is?
- A . rule name c
Source-zone untrust
Destination-zone trust
Destination-address 202.106.1.132
Action permit - B . rule name d
Source-zone untrust
Destination-zone trust
Destination-address 10.10.1.132
Action permit - C . security-policy
Rule name a
Source-zone untrust
Source-address 202.106.1.132
Action permit - D . rule name b
Source-zone untrust
Destination-zone trust
Source-address 10.10.1.1 32
Action permit
Which of the following types of firewalls has the highest processing efficiency when processing non-first packet data flows?
- A . Proxy firewall
- B . Packet filtering firewall
- C . Stateful Monitoring Firewall
- D . Software firewall
Latest H12-711_V4.0-ENU Dumps Valid Version with 91 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund

