Huawei H12-321-ENU HCIP-WLAN CEWA(Huawei Certified ICT Professional-Wireless Local Area Network-Constructing Enterprise WLAN Architecture) Online Training
Huawei H12-321-ENU Online Training
The questions for H12-321-ENU were last updated at Apr 23,2025.
- Exam Code: H12-321-ENU
- Exam Name: HCIP-WLAN CEWA(Huawei Certified ICT Professional-Wireless Local Area Network-Constructing Enterprise WLAN Architecture)
- Certification Provider: Huawei
- Latest update: Apr 23,2025
Which of the following is correct about the Earth curvature formula?
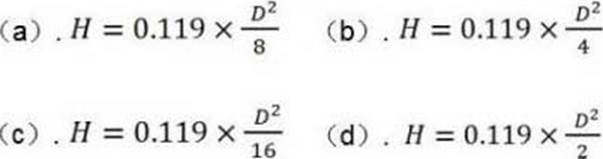
- A . A.
- B . B.
- C . C.
- D . D.
As shown in the figure, what is the load sharing method of the dual-system hot backup solution?
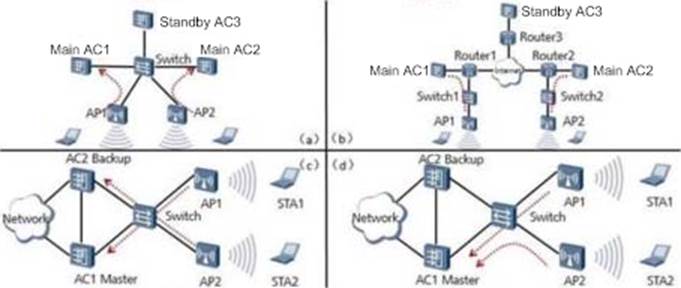
- A . A.
- B . B.
- C . C.
- D . D.
As shown in the figure, in the dual-link cold standby load sharing network, AP1 is a newly online AP, and both the two ACs have access configurations, which AC will AP1 choose for access?
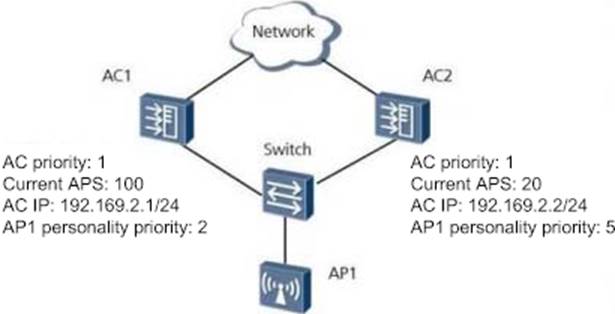
- A . AC1
- B . AC2
- C . Random access
- D . No access
As shown in the figure, in public places, such as different companies on adjacent floors in an office building, there are multiple SSIDs. After a company turns on the WIDS illegal device counter function, it will counter the AP of other companies. Which of the following function can effectively solve this problem?
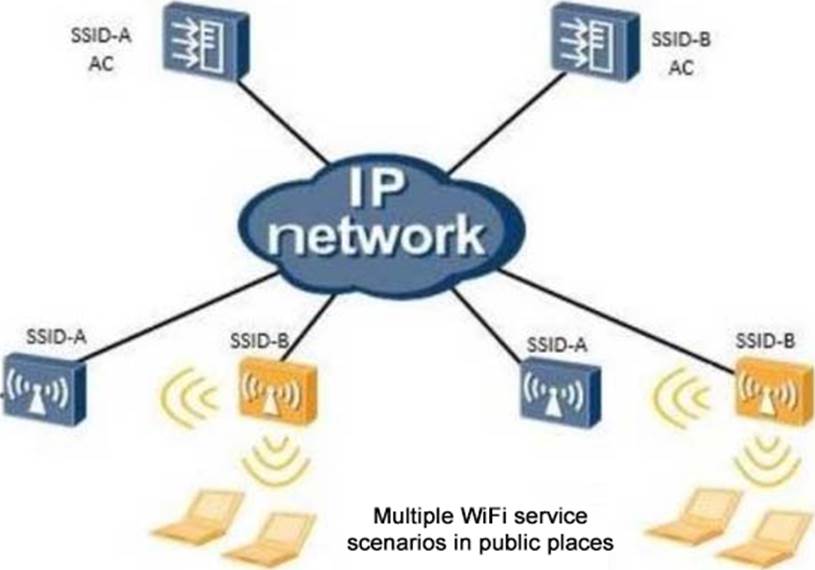
- A . Dynamic blacklist function
- B . WIDS countermeasure mode switching
- C . WIDS counterfeit SSID detection
- D . WIDS whitelist function
As shown in the figure, in order to avoid the transparent transmission of STP packets and cause loops to affect each other, which of the following does not need to enable the STP spanning tree protocol?
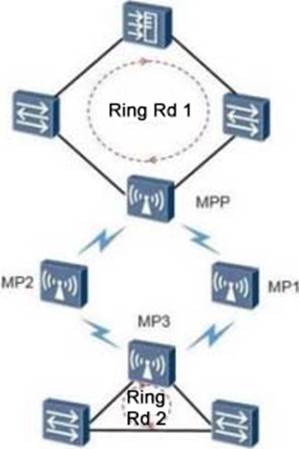
- A . Only the MPP wired side interface needs to enable the STP function
- B . Only the MP3 wired side interface needs to enable the STP function
- C . Both MPP and MP3 wired side interfaces need to enable STP function
- D . MP1 and MP2 need to enable STP
As shown in the figure is the WIDS attack detection process. After the dynamic blacklist is issued, how will the AP handle different data traffic when it is in the blacklist penalty period?
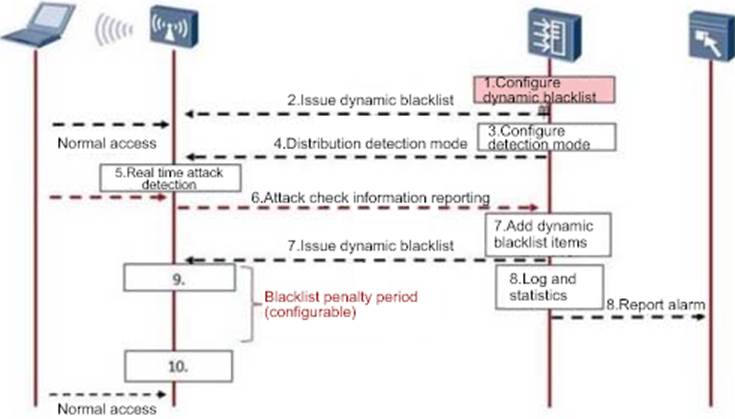
- A . Forward normal data traffic and discard attack traffic
- B . Discard normal data traffic and report attack traffic
- C . Forward normal data traffic and report attack traffic
- D . Discard normal data traffic and discard attack traffic
As shown in the figure, there are 4 online STAs (STA1-STA4) under AP1 radio frequency, and 1 online STA (STA5) under AP2 radio frequency. The load balancing start threshold 5 is exceeded, and the maximum number associated users supported by AP1 and AP2 radio frequencies is 10, and the configured load difference threshold is 10%.
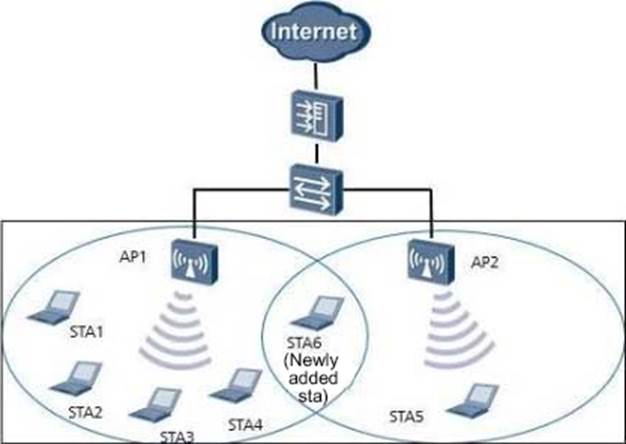
When STA6 initiates a request to AP1 for the first time, which of the following statements is correct?
- A . AP1 is first calculated according to the load balancing algorithm, and STA6 is allowed to access
- B . AP1 is calculated according to the load difference threshold algorithm first, and STA6 is allowed to access
- C . AP1 is first calculated according to the load balancing algorithm, and STA6 is denied access
- D . AP1 is calculated based on the load difference threshold algorithm first, and STA6 is denied access
In the network shown in the figure, how is the route selected from A to D in the pro-active mode?
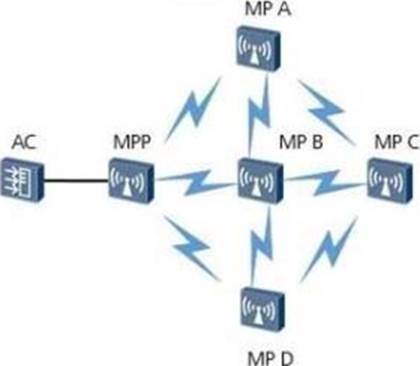
- A . A-MPP-D
- B . A-B-D
- C . A-B-C-D
- D . A-D
In the network shown in the figure below, the data traffic before roaming is forwarded as STA-HAP-HC-upper network, and the forwarding method is tunnel forwarding. After three-layer roaming, what is the direction of data forwarding traffic?
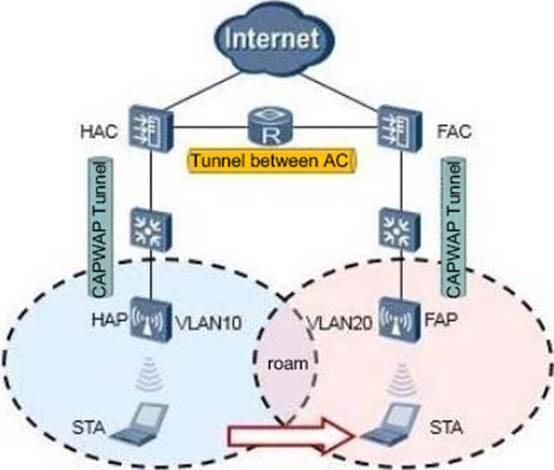
- A . STA-FAP-FAC-HAC-Upper Network
- B . STA-FAP-FAC-HAC-HAP-HAC-upper network
- C . STA-FAP-FAC-Upper Network
- D . FAP-FAC-HAC-FAC-Upper Network
In the network as shown in the figure below, the data traffic is forwarded as STA-HAP-HAC-upper network before roaming, and the forwarding method is direct forwarding, and the home agent is configured on the AC. After three-layer roaming, what is the direction of data forwarding traffic?
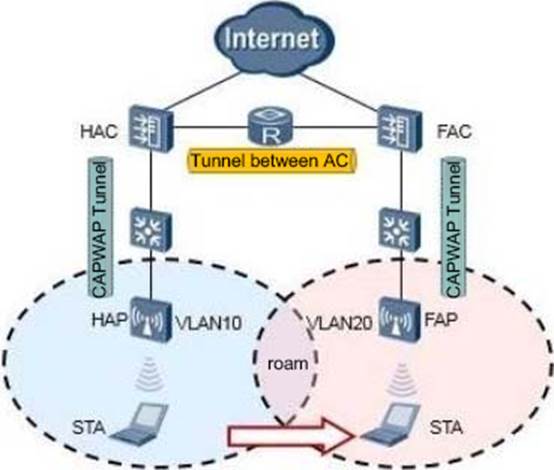
- A . STA-FAP-FAC-Upper Network
- B . STA-FAP-FAC-HAC-FAC-Upper Network
- C . STA-FAP-FAC-HAC-Upper Network
- D . STA-FAP-FAC-HAC-HAP-HAC-upper network
Latest H12-321-ENU Dumps Valid Version with 319 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund

