Huawei H12-261-ENU HCIE-Routing&Switching (Written)(Huawei Certified ICT Expert-Routing & Switching) Online Training
Huawei H12-261-ENU Online Training
The questions for H12-261-ENU were last updated at Dec 22,2025.
- Exam Code: H12-261-ENU
- Exam Name: HCIE-Routing&Switching (Written)(Huawei Certified ICT Expert-Routing & Switching)
- Certification Provider: Huawei
- Latest update: Dec 22,2025
The LAND attack is performed by the attacker sending a source address and a destination address to the destination host are the destination host, the same SYN packet on source port and the destination port. When the receiver waits for the final ACK packet from the sender, the connection is always in a semi-connected state, resulting in waste of limited TCP resources at the receiving end.
- A . True
- B . False
The following statement about the security confederation SA in IPsec, which is wrong?
- A . The SA is uniquely identified by a triplet that includes the Security Parameter Index (SP), the source IP address and the security protocol number used (AH or ESP).
- B . Use display IPsec to view information about encryption algorithms, traffic, and other information used between another IPsec peer.
- C . IPsec only supports the use of symmetric encryption algorithms to encrypt data.
- D . There must be two-way SA between IPsec peers to establish an IPsec VPN connection.
Router HW1 and router HW2 are connected to network A and network B respectively. As shown below, if you want to establish an IPsec VPN between router HW1 and router HW2.
Which ACL does the router HW1 need to configure to enable LAN-to-LAN traffic to pass through the encrypted VPN tunnel?
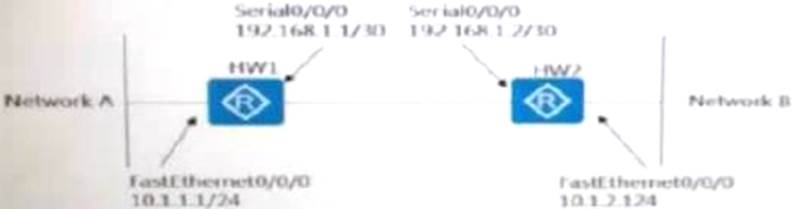
- A . rule permit ip source 192.168.1.10 destination 192.168.1.2 0
- B . rule permit ip source 10.1.1.0 0.0.0.255 destination 192.168.1.2 0
- C . rule permit ip source 10.1.1.0 0.0.0.255 destination 10.1.2.0 0.0.0.255
- D . rule permit ip source 192.168.1.10 destination 10.1.2.0 0.0.0.255
- E . rule permit ip source 10.1.2.0 0.0.0.255 destination 10.1.1.0 0.0.0.255
Which of the following options is correct for the assertion mechanism?
- A . The size of the IP address will not be used as a condition for election during the election of the winner.
- B . In the assertion mechanism, winner is responsible for forwarding multicast data to the broadcast network segment.
- C . The assertion mechanism is used for the election of the DR.
- D . In the assertion mechanism, loser shut down the interface connected to the broadcast network.
If there are multiple receivers in a multicast group, the administrator enables IGMP-Snooping on the switch connecting the receiver. After the receiver receives the general query message from the querier, the receiver receives multiple receivers. How to respond?
- A . All recipients will respond to the Report message.
- B . Only when IGMPv1 is running, all receivers respond to the Report message.
- C . The first responder with a response timeout sends a Report message, and the other recipients do not send it.
- D . Only the IGMPV2 is running, and all receivers respond to the Report message.
If running PIM-SM on a multicast network, you need to construct a multicast forwarding tree between the multicast source and the receiver to enable the receiver to receive multicast data. Which of the following description about the constructed multicast forwarding tree is correct? (Multiple Choice)
- A . The RTP tree is built between the RP and the receiver.
- B . The RPT tree is built between the multicast source and the RP.
- C . The SPT tree is built between the RP and the receiver.
- D . The SPT tree is built between the multicast source and the RP.
The following description of the BSR mechanism, which is correct? (Multiple Choice)
- A . There can be multiple C-BSR in a PIM-SM domain, but only one BSR can be elected.
- B . The BSR collects C-RP information through the received C-RP data packets.
- C . The BSR advertises BSR information and C-RP information to all routers in the PIM-SM domain by flooding Bootstrap packets.
- D . One C-BSR can also collect C-RP information through received C-RP packets.
The following are the statements about LDP reliability, which one is wrong?
- A . LDP FRR can also be used to generate an LSP for the label mapping from the non-optimal next hop. And it can be as a backup of the primary LSP to establish the transfer entries.
- B . The association between the LDP and the IGP requires the IGP to suppress the advertisement of the route and ensure that the LDP path is consistent with the IGP path.
- C . The manually configured LDP FRR policy defaults to a 32-bit backup route that triggers LDP to establish a backup LSP.
- D . LDP GR Graceful Restart uses the feature that the MPLS forwarding plane is separated from the control plane. The device does not interrupt when the protocol is restarted or the active/standby switchover is performed.
The following is about the LDP protocol session establishment process, which is the correct description? (Multiple choice)
- A . After the TCP connection is successfully established, the active party sends an initialization message to negotiate the parameters related to the LDP session.
- B . The party with the larger transmission address acts as the active party and initiates the establishment of TCP connection.
- C . The Hello message discovered by the LDP neighbor uses TCP packets. The destination address is the multicast address 224.0.0.2.
- D . After both parties receive the Keepalive message from the peer, the LDP session is established successfully.
RD is used to distinguish the same IP address in different VPNs. How many bits does the RD contain?
- A . 64
- B . 32
- C . 16
- D . 128
Latest H12-261-ENU Dumps Valid Version with 284 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund

