HP HPE6-A78 Aruba Certified Network Security Associate Exam Online Training
HP HPE6-A78 Online Training
The questions for HPE6-A78 were last updated at Dec 17,2025.
- Exam Code: HPE6-A78
- Exam Name: Aruba Certified Network Security Associate Exam
- Certification Provider: HP
- Latest update: Dec 17,2025
You have been asked to rind logs related to port authentication on an ArubaOS-CX switch for events logged in the past several hours But. you are having trouble searching through the logs.
What is one approach that you can take to find the relevant logs?
- A . Add the "-C and *-c port-access" options to the "show logging" command.
- B . Configure a logging Tiller for the "port-access" category, and apply that filter globally.
- C . Enable debugging for "portaccess" to move the relevant logs to a buffer.
- D . Specify a logging facility that selects for "port-access" messages.
What is symmetric encryption?
- A . It simultaneously creates ciphertext and a same-size MAC.
- B . It any form of encryption mat ensures that thee ciphertext Is the same length as the plaintext.
- C . It uses the same key to encrypt plaintext as to decrypt ciphertext.
- D . It uses a Key that is double the size of the message which it encrypts.
What is one of the roles of the network access server (NAS) in the AAA framewonx?
- A . It authenticates legitimate users and uses policies to determine which resources each user is allowed to access.
- B . It negotiates with each user’s device to determine which EAP method is used for authentication
- C . It enforces access to network services and sends accounting information to the AAA server
- D . It determines which resources authenticated users are allowed to access and monitors each users session
You have detected a Rogue AP using the Security Dashboard Which two actions should you take in responding to this event? (Select two)
- A . There is no need to locale the AP If you manually contain It.
- B . This is a serious security event, so you should always contain the AP immediately regardless of your company’s specific policies.
- C . You should receive permission before containing an AP. as this action could have legal Implications.
- D . For forensic purposes, you should copy out logs with relevant information, such as the time mat the AP was detected and the AP’s MAC address.
- E . There is no need to locate the AP If the Aruba solution is properly configured to automatically contain it.
What role does the Aruba ClearPass Device Insight Analyzer play in the Device Insight architecture?
- A . It resides in the cloud and manages licensing and configuration for Collectors
- B . It resides on-prem and provides the span port to which traffic is mirrored for deep analytics.
- C . It resides on-prem and is responsible for running active SNMP and Nmap scans
- D . It resides In the cloud and applies machine learning and supervised crowdsourcing to metadata sent by Collectors
Which correctly describes a way to deploy certificates to end-user devices?
- A . ClearPass Onboard can help to deploy certificates to end-user devices, whether or not they are members of a Windows domain
- B . ClearPass Device Insight can automatically discover end-user devices and deploy the proper certificates to them
- C . ClearPass OnGuard can help to deploy certificates to end-user devices, whether or not they are members of a Windows domain
- D . in a Windows domain, domain group policy objects (GPOs) can automatically install computer, but not user certificates
How should admins deal with vulnerabilities that they find in their systems?
- A . They should apply fixes, such as patches, to close the vulnerability before a hacker exploits it.
- B . They should add the vulnerability to their Common Vulnerabilities and Exposures (CVE).
- C . They should classify the vulnerability as malware. a DoS attack or a phishing attack.
- D . They should notify the security team as soon as possible that the network has already been breached.
Refer to the exhibit.
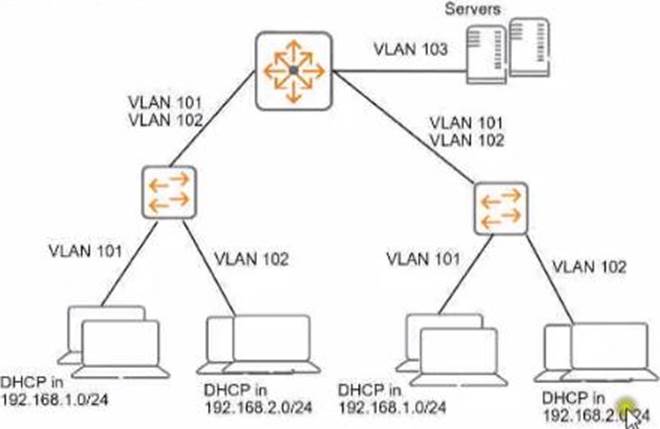
You need to ensure that only management stations in subnet 192.168.1.0/24 can access the ArubaOS-Switches’ CLI. Web Ul. and REST interfaces. The company also wants to let managers use these stations to access other parts of the network.
What should you do?
- A . Establish a Control Plane Policing class that selects traffic from 192.168 1.0/24.
- B . Specify 192.168.1.0.255.255.255.0 as authorized IP manager address
- C . Configure the switch to listen for these protocols on OOBM only.
- D . Specify vlan 100 as the management vlan for the switches.
CORRECT TEXT
What is a use case for tunneling traffic between an Aruba switch and an AruDa Mobility Controller (MC)?
- A . applying firewall policies and deep packet inspection to wired clients
- B . enhancing the security of communications from the access layer to the core with data encryption
- C . securing the network infrastructure control plane by creating a virtual out-of-band-management network
- D . simplifying network infrastructure management by using the MC to push configurations to the switches
Your Aruba Mobility Master-based solution has detected a rogue AP Among other information the ArubaOS Detected Radios page lists this Information for the AP
SSID = PubllcWiFI
BSSID = a8M27 12 34:56
Match method = Exact match
Match type = Eth-GW-wired-Mac-Table
The security team asks you to explain why this AP is classified as a rogue .
What should you explain?
- A . The AP Is connected to your LAN because It is transmitting wireless traffic with your network’s default gateway’s MAC address as a source MAC Because it does not belong to the company, it is a rogue
- B . The ap has a BSSID mat matches authorized client MAC addresses. This indicates that the AP is spoofing the MAC address to gam unauthorized access to your company’s
wireless services, so It is a rogue - C . The AP has been detected as launching a DoS attack against your company’s default gateway. This qualities it as a rogue which needs to be contained with wireless association frames immediately
- D . The AP is spoofing a routers MAC address as its BSSID. This indicates mat, even though WIP cannot determine whether the AP is connected to your LAN. it is a rogue.
Latest HPE6-A78 Dumps Valid Version with 60 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund

