HP HPE6-A68 Aruba Certified ClearPass Professional (ACCP) V6.7 Online Training
HP HPE6-A68 Online Training
The questions for HPE6-A68 were last updated at Jan 04,2026.
- Exam Code: HPE6-A68
- Exam Name: Aruba Certified ClearPass Professional (ACCP) V6.7
- Certification Provider: HP
- Latest update: Jan 04,2026
Which types of files are stored in the Local Shared Folders database in ClearPass? (Select two.)
- A . Software image
- B . Backup files
- C . Log files
- D . Device fingerprint dictionaries
- E . Posture dictionaries
What are Operator Profiles used for?
- A . to enforce role based access control for Aruba Controllers
- B . to enforce role based access control for ClearPass Policy Manager admin users
- C . to enforce role based access control for ClearPass Guest Admin users
- D . to assign ClearPass roles to guest users
- E . to map AD attributes to admin privilege levels in ClearPass Guest
Refer to the exhibit.
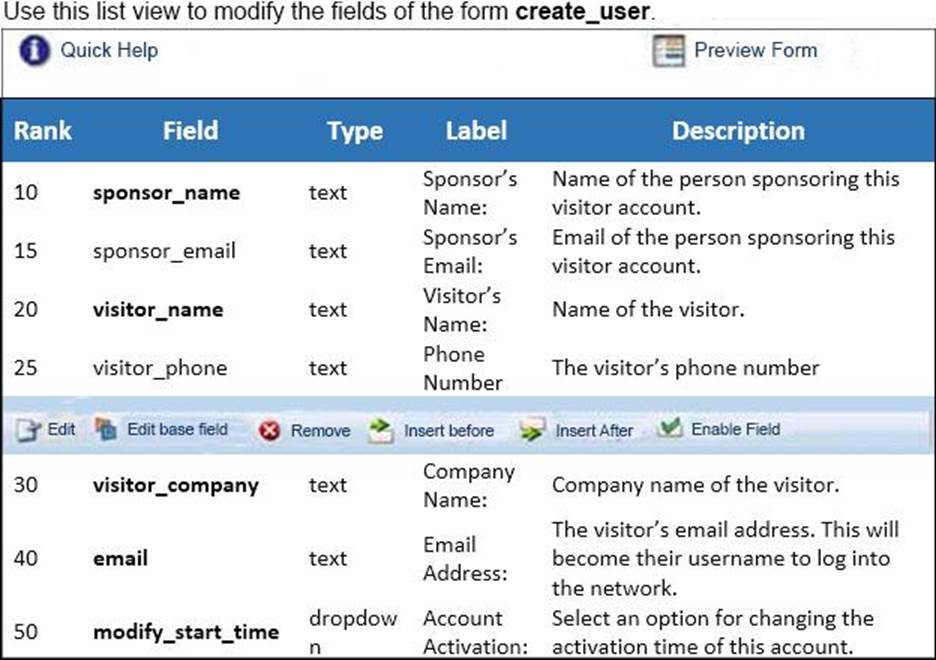
Based on the configuration of the create_user form shown, which statement accurately describes the status?
- A . The email field will be visible to guest users when they access the web login page.
- B . The visitor_company field will be visible to operators creating the account.
- C . The visitor_company field will be visible to the guest users when they access the web login page.
- D . The visitor_phone field will be visible to the guest users in the web login page.
- E . The visitor_phone field will be visible to operators creating the account.
Refer to the exhibit.
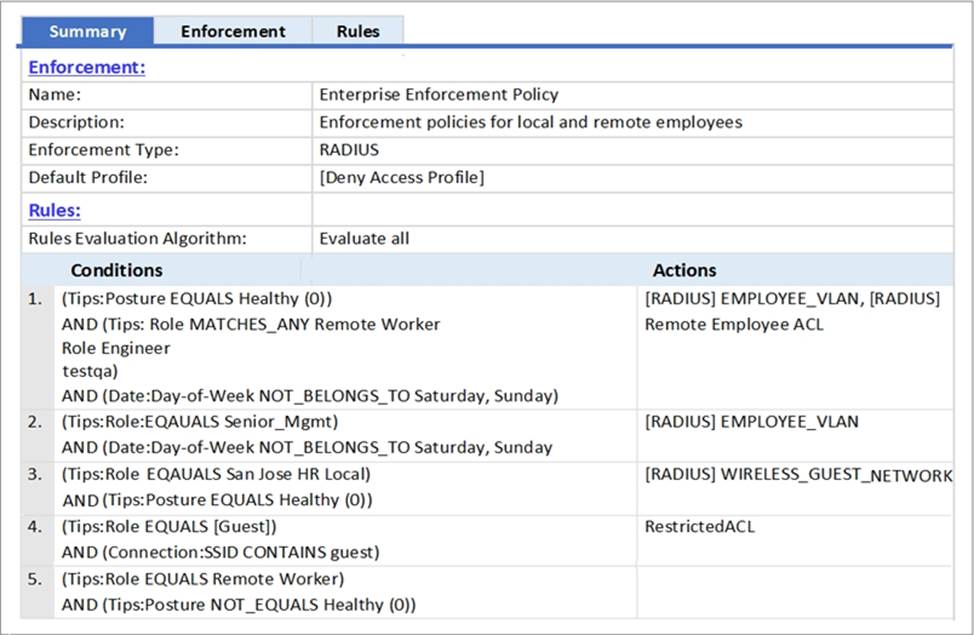
Based on the Enforcement Policy configuration shown, when a user with Role Engineer connects to the network and the posture token assigned is Unknown, which Enforcement Profile will be applied?
- A . EMPLOYEE_VLAN
- B . RestrictedACL
- C . Deny Access Profile
- D . HR VLAN
- E . Remote Employee ACL
Based on the Local User repository in ClearPass shown, which Aruba firewall role will be assigned to “mike” when this user authenticates Aruba Controller?
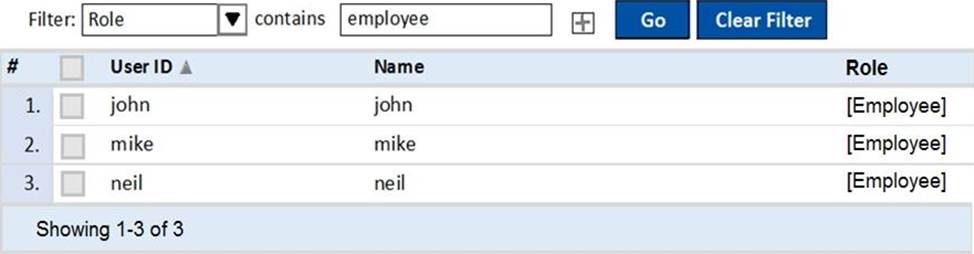
- A . We can’t know this from the screenshot above.
- B . mike
- C . Employee
- D . john
A customer would like to deploy ClearPass with these requirements:
✑ between 2000 to 3000 corporate users need to authenticate daily using EAP-TLS
✑ should allow for up to 1000 employee devices to be Onboarded
✑ should allow up to 100 guest users each day to authenticate using the web login feature
What is the license mix that customer will need to purchase?
- A . CP-HW-2k, 1000 Onboard, 100 Guest
- B . CP-HW-500, 1000 Onboard, 100 Guest
- C . CP-HW-5k, 2500 Enterprise
- D . CP-HW-5k, 1000 Enterprise
- E . CP-HW-5k, 100 Onboard, 100 Guest
What must be configured to enable RADIUS authentication with ClearPass on a network access device (NAD)? (Select two.)
- A . the ClearPass server must have the network device added as a valid NAD
- B . the ClearPass server certificate must be installed on the NAD
- C . a matching shared secret must be configured on both the ClearPass server and NAD
- D . an NTP server needs to be set up on the NAD
- E . a bind username and bind password must be provided
In which ways can ClearPass derive client roles during policy service processing? (Select two.)
- A . From the attributes configured in Active Directory
- B . From the server derivation rule in the Aruba Controller server group for the client
- C . From the Aruba Network Access Device
- D . From the attributes configured in a Network Access Device
- E . Through a role mapping policy
A hotel chain deployed ClearPass Guest. When hotel guests connect to the Guest SSID, launch a web browser and enter the address www.google.com, they are unable to immediately see the web login page.
What are the likely causes of this? (Select two.)
- A . The ClearPass server has a trusted server certificate issued by Verisign.
- B . The ClearPass server has an untrusted server certificate issued by the internal Microsoft Certificate server.
- C . The ClearPass server does not recognize the client’s certificate.
- D . The DNS server is not replying with an IP address for www.google.com.
What is the purpose of ClearPass Onboard?
- A . to provide MAC authentication for devices that don’t support 802.1x
- B . to run health checks on end user devices
- C . to provision personal devices to securely connect to the network
- D . to configure self-registration pages for guest users
- E . to provide guest access for visitors to connect to the network
Latest HPE6-A68 Dumps Valid Version with 116 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund

