How should you configure security?
DRAG DROP
You need to set up security to meet the requirements.
How should you configure security? To answer, drag the appropriate security mechanisms to the correct users. Each security mechanism may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content. NOTE: Each correct selection is worth one point.
Answer: 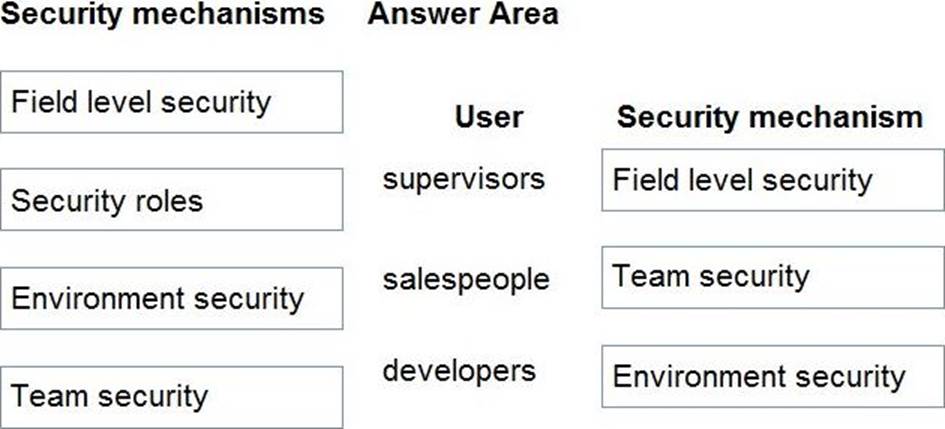
Explanation:
Box 1: Field level security
Only supervisors must be able to view phone numbers in the Accounts form.
You use field security tables to apply field-level security, which restricts field access to specified users and teams. The scope of field-level security is global, which means that it applies to all records within the organization, regardless of the business unit hierarchical level to which the record or the user belongs. Field security works in all Microsoft Dataverse clients, including the Web client, Dynamics 365 for Outlook, and Dynamics. It applies to all components, such as the Dataverse web services, reports, search, offline, filtered views, auditing, and duplicate detection.
Box 2: Team Security
Sales users must only have access to their own records.
Owner team: An owner team owns records and has security roles assigned to the team. A user’s privileges can come from their individual security roles, those of the teams that they’re part of or the ones they inherit. A team has full access rights on the records that the team owns. Team members are added manually to the owner team.
Box 3: Environment security
Developers must be able to create new apps for all users.
Environment maker: Can create new resources associated with an environment, including apps, connections, custom APIs, gateways, and flows using Microsoft Power Automate. However, this role doesn’t have any privileges to access data within an environment.
Latest PL-400 Dumps Valid Version with 171 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund

