How should the computation of the signature be done for client apps that receive Orchestrator requests and need to check their authenticity?
DRAG DROP
How should the computation of the signature be done for client apps that receive Orchestrator requests and need to check their authenticity?
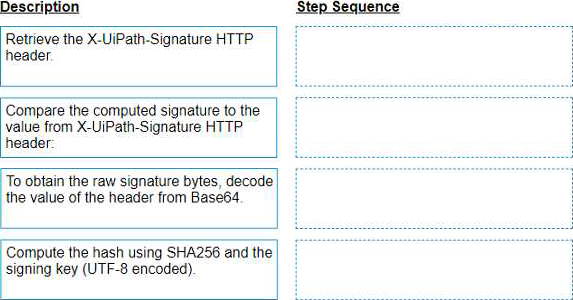
Instructions: Drag the Description found on the left and drop on the correct Step Sequence found on the right.
Answer: 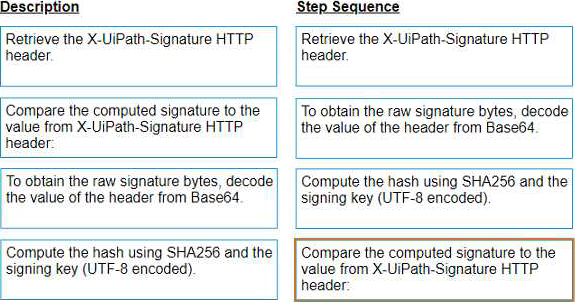
Explanation:
The correct sequence for the computation of the signature for client apps that receive Orchestrator requests and need to check their authenticity is:
Retrieve the X-UiPath-Signature HTTP header. This header contains the signature of the request body, encoded in Base64. (UiPath Orchestrator documentation1)
To obtain the raw signature bytes, decode the value of the header from Base64. You can use any tool or library that supports Base64 decoding. (UiPath Orchestrator documentation1)
Compute the hash using SHA256 and the signing key (UTF-8 encoded). The signing key is a secret value that is shared between Orchestrator and the client app. You can use any tool or library that supports SHA256 hashing. (UiPath Orchestrator documentation1)
Compare the computed signature to the value from X-UiPath-Signature HTTP header. If they match, then the request is authentic and has not been tampered with. If they do not match, then the request is invalid and should be rejected. (UiPath Orchestrator documentation1).
References:1: Webhooks – UiPath Orchestrator.
Latest UiPath-ADAv1 Dumps Valid Version with 60 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund

