HashiCorp VA-002-P HashiCorp Certified: Vault Associate Online Training
HashiCorp VA-002-P Online Training
The questions for VA-002-P were last updated at Mar 07,2026.
- Exam Code: VA-002-P
- Exam Name: HashiCorp Certified: Vault Associate
- Certification Provider: HashiCorp
- Latest update: Mar 07,2026
What can be used to limit the scope of a credential breach?
- A . Storage of secrets in a distributed ledger
- B . Enable audit logging
- C . Use of a short-lived dynamic secrets
- D . Sharing credentials between applications
What environment variable overrides the CLI’s default Vault server address?
- A . VAULT_ADDR
- B . VAULT_HTTP_ADORESS
- C . VAULT_ADDRESS
- D . VAULT _HTTPS_ ADDRESS
Which of the following statements describe the CLI command below?
S vault login -method-1dap username-mitche11h
- A . Generates a token which is response wrapped
- B . You will be prompted to enter the password
- C . By default the generated token is valid for 24 hours
- D . Fails because the password is not provided
The following three policies exist in Vault.
What do these policies allow an organization to do?
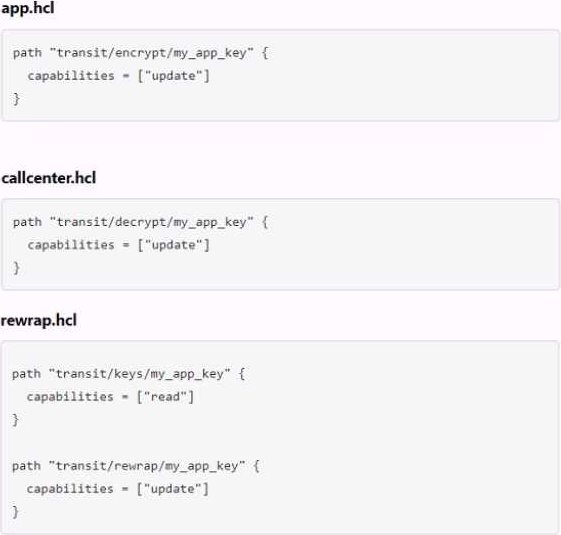
- A . Separates permissions allowed on actions associated with the transit secret engine
- B . Nothing, as the minimum permissions to perform useful tasks are not present
- C . Encrypt, decrypt, and rewrap data using the transit engine all in one policy
- D . Create a transit encryption key for encrypting, decrypting, and rewrapping encrypted data
Your DevOps team would like to provision VMs in GCP via a CICD pipeline. They would like to integrate Vault to protect the credentials used by the tool.
Which secrets engine would you recommend?
- A . Google Cloud Secrets Engine
- B . Identity secrets engine
- C . Key/Value secrets engine version 2
- D . SSH secrets engine
Which of these is not a benefit of dynamic secrets?
- A . Supports systems which do not natively provide a method of expiring credentials
- B . Minimizes damage of credentials leaking
- C . Ensures that administrators can see every password used
- D . Replaces cumbersome password rotation tools and practices
Which of the following cannot define the maximum time-to-live (TTL) for a token?
- A . By the authentication method t natively provide a method of expiring credentials
- B . By the client system f credentials leaking
- C . By the mount endpoint configuration very password used
- D . A parent token TTL e password rotation tools and practices
- E . System max TTL
What are orphan tokens?
- A . Orphan tokens are tokens with a use limit so you can set the number of uses when you create them
- B . Orphan tokens are not children of their parent; therefore, orphan tokens do not expire when their parent does
- C . Orphan tokens are tokens with no policies attached
- D . Orphan tokens do not expire when their own max TTL is reached
To give a role the ability to display or output all of the end points under the /secrets/apps/* end point it would need to have which capability set?
- A . update
- B . read
- C . sudo
- D . list
- E . None of the above
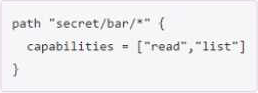
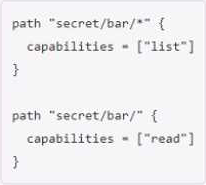
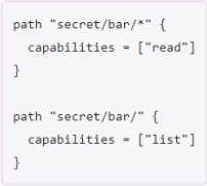
You have been tasked with writing a policy that will allow read permissions for all secrets at path secret/bar. The users that are assigned this policy should also be able to list the secrets.
What should this policy look like?
A)
B)
C)
D)
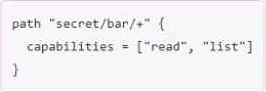
- A . Option A
- B . Option B
- C . Option C
- D . Option D
Latest VA-002-P Dumps Valid Version with 200 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund

