HashiCorp TA-002-P HashiCorp Certified: Terraform Associate Online Training
HashiCorp TA-002-P Online Training
The questions for TA-002-P were last updated at Dec 25,2025.
- Exam Code: TA-002-P
- Exam Name: HashiCorp Certified: Terraform Associate
- Certification Provider: HashiCorp
- Latest update: Dec 25,2025
HashiCorp Configuration Language (HCL) supports user-defined functions.
- A . True
- B . False
B
Explanation:
https://www.terraform.io/language/functions
The Terraform language does not support user-defined functions, and so only the functions built into the language are available for use
You’re building a CI/CD (continuous integration/ continuous delivery) pipeline and need to inject sensitive variables into your Terraform run.
How can you do this safely?
- A . Pass variables to Terraform with a Cvar flag
- B . Copy the sensitive variables into your Terraform code
- C . Store the sensitive variables in a secure_vars.tf file
- D . Store the sensitive variables as plain text in a source code repository
A
Explanation:
https://blog.gruntwork.io/a-comprehensive-guide-to-managing-secrets-in-your-terraform-code-1d586955ace1
Terraform provisioners that require authentication can use the ______ block.
- A . connection
- B . credentials
- C . secrets
- D . ssh
A
Explanation:
https://www.terraform.io/language/resources/provisioners/connection
"Most provisioners require access to the remote resource via SSH or WinRM and expect a nested connection block with details about how to connect." "Connection blocks don’t take a block label and can be nested within either a resource or a provisioner."
You have recently started a new job at a retailer as an engineer. As part of this new role, you have been tasked with evaluating multiple outages that occurred during peak shopping time during the holiday season. Your investigation found that the team is manually deploying new compute instances and configuring each compute instance manually. This has led to inconsistent configuration between each compute instance.
How would you solve this using infrastructure as code?
- A . Implement a ticketing workflow that makes engineers submit a ticket before manually provisioning and configuring a resource
- B . Implement a checklist that engineers can follow when configuring compute instances
- C . Replace the compute instance type with a larger version to reduce the number of required deployments
- D . Implement a provisioning pipeline that deploys infrastructure configurations committed to your version control system following code reviews
In Terraform 0.13 and above, outside of the required_providers block, Terraform configurations always refer to providers by their local names.
- A . True
- B . False
A
Explanation:
Outside of the required_providers block, Terraform configurations always refer to providers by their local names.
Reference:
https://www.terraform.io/docs/language/providers/requirements.html
https://www.terraform.io/language/providers/requirements#local-names
What is one disadvantage of using dynamic blocks in Terraform?
- A . They cannot be used to loop through a list of values
- B . Dynamic blocks can construct repeatable nested blocks
- C . They make configuration harder to read and understand
- D . Terraform will run more slowly
C
Explanation:
"Overuse of dynamic blocks can make configuration hard to read and maintain, so we recommend using them only when you need to hide details in order to build a clean user interface for a re-usable module. Always write nested blocks out literally where possible."
Reference: https://github.com/hashicorp/terraform/issues/19291
You write a new Terraform configuration and immediately run terraform apply in the CLI using the local backend.
Why will the apply fail?
- A . Terraform needs you to format your code according to best practices first
- B . Terraform needs to install the necessary plugins first
- C . The Terraform CLI needs you to log into Terraform cloud first
- D . Terraform requires you to manually run terraform plan first
When should you use the force-unlock command?
- A . You see a status message that you cannot acquire the lock
- B . You have a high priority change
- C . Automatic unlocking failed
- D . Your apply failed due to a state lock
C
Explanation:
Be very careful with this command. If you unlock the state when someone else is holding the lock it could cause multiple writers. Force unlock should only be used to unlock your own lock in the situation where automatic unlocking failed. Source: https://www.terraform.io/language/state/locking https://www.terraform.io/cli/commands/force-unlock
What is the provider for this fictitious resource?
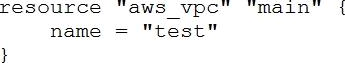
- A . vpc
- B . main
- C . aws
- D . test
C
Explanation:
Reference: https://docs.aws.amazon.com/cloudformation-cli/latest/userguide/resource-types.html
You should store secret data in the same version control repository as your Terraform configuration.
- A . True
- B . False
B
Explanation:
Reference: https://blog.gruntwork.io/a-comprehensive-guide-to-managing-secrets-in-your-terraform-code- 1d586955ace1
Latest TA-002-P Dumps Valid Version with 324 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund

