Below is an extract from a Server Access Log showing a record for a request made to an AWS S3 bucket.
What does the first field starting with "385f9e" represent?
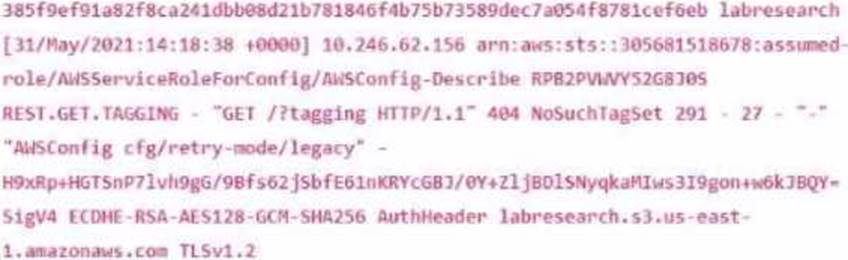
- A . Bucket Owner
- B . Request ID
- C . Host ID
- D . Cipher Suite
Which is the effective access when aws user is assigned to an S3 bucket?
- A . A user must have an employee account
- B . A user must have an account under any AWS account
- C . A user must be under the same AWS account as the S3 bucket
- D . A user must have the AWS IAM role assigned
What logical AWS structure type is used to chain together accounts in a trust relationship which allows for single sign-on and cross-account management?
- A . Subscription
- B . Organisation
- C . OU
- D . Tenant
An Azure blob is accessed using the link below.
What is the name of the blob container?
- A . ex-storage
- B . mov.avi
- C . mymovies
- D . blob.core
In Azure, which of the following describes a "Contributor"?
- A . A collection of permissions such as read, write, and delete
- B . A designation on a PKI certificate
- C . A specification of who can access a resource group
- D . An object representing an entity
What Pub/Sub component is used to forward GCP logs to their final location?
- A . Topic
- B . Log Sink
- C . Publication
- D . Subscription
Which of the following is the smallest unit of computing hardware in Kubernetes?
- A . Cluster
- B . Node
- C . Container
- D . Pod
What is a best practice recommendation when using API keys for AWS access?
- A . Delete the account’s default access keys
- B . Define specific role permissions
- C . Enable MFA protection
- D . Configure STS one-time tokens
What would prevent GCP 1AM from linking to Google Workspace to manage users and groups?
- A . A gcp-organization-admins group was not created
- B . The connector was not configured to link the services
- C . Inadequate Identity and Access Management license
- D . Google Workspace cannot be linked to GCP 1AM
What type of AWS log is the following snippet an example of?
- A . Web Application firewall Log
- B . VPC Flow Log
- C . Load Balancer Log
- D . Route 53 Query Log
An investigator confirms that phishing emails sent to users in an organization ate not being sent to their Gmall Spam folder.
What is a possible cause for this?
- A . The default setting for enhanced pre-delivery message scanning was changed
- B . The security sandbox default configuration setting was changed
- C . A third party application needs to be installed to detect phishing emails
- D . Compliance based rules need to be configured to detect phishing emails
How is storage account, cs21003200042c87633, created in an Azure resource group?
- A . PowerShell Cloud Shell audit logging was enabled
- B . A Bash Cloud Shell was used
- C . PowerShelI Cloud Shell was used
- D . Azure CLI was used from a Windows machine
An engineer has set up log forwarding for a new data source and wants to use that data to run reports and create dashboards in Kibana.
What needs to be created in order to properly handle these logs?
- A . Row
- B . Parser
- C . ingest script
- D . Beat
At what point of the OAuth delegation process does the Resource Owner approve the scope of access to be allowed?
- A . After user credentials are accepted by the Authorization Server
- B . Once the OAuth token is accepted by the Application
- C . When the Resource Server receives the OAuth token
- D . Before user credentials are sent to the Authentication Server
Which cloud service provider produces sampled flow logs?
- A . GCP
- B . Azure
- C . AWS
What method does Google use to alert Gmail account holders that they may be under attack by government sponsored attackers?
- A . Message upon successful logon
- B . SMS text message
- C . Email sent to the user
- D . Alert sent to recovery account
Which AW5 1AM policy element indicates the API that is in scope?
- A . Effect
- B . Version
- C . Action
- D . Resource
Sensitive company data is found leaked on the internet, and the security team didn’t get any alert and is unsure of how the breach occurred.
Which logs would be a preferable starting point for an investigation?
- A . Identity and Access Management
- B . Application
- C . Resource Management
- D . Endpoint
An investigator is evaluating a client’s Microsoft 365 deployment using the web portals and has identified that the Purview compliance portal states that the Unified Audit Logs are not enabled.
Based on the additional Information gathered below, what is most likely the cause of this configuration message?
Subscription creation date: December 4, 2021 Number of administrators: 2 Number of non-administrative user accounts: 74 Last tenant administration change: December 4,2021
- A . Explicitly been disabled by an administrator
- B . License was downgraded lower than an E5 license
- C . Tenant is configured to forward logs externally
- D . Default configuration, service was never enabled
At what organizational level are EC2 services managed by customers?
- A . Data center
- B . Regional
- C . Global
- D . Continental
An investigator his successfully installed the ExchangeOnlineManagement module on their investigation system and is attempting to search a client’s Microsoft 365 Unified Audit Log using PowerShell. PowerShell returns a "command not found" error each time they try to execute the Search-UnifiedAuditLog cmdlet.
How should the investigator troubleshoot this issue?
- A . Ensure their system has .NFT version 4.b or later Installed
- B . Ensure that MFA has been disabled for The account used
- C . Check that they are using PowerShell Core
- D . Check the permissions of the account used in Microsoft 365
The attack technique "Access Kubelet API" falls under which Mitre ATT&CK tactic?
- A . Execution
- B . Credential Access
- C . Discovery
- D . Initial Access
An analyst successfully authenticated to Microsoft 365 using the following command.
What would cause the analyst to be unable to search UAL events for a specific time period?
Ps> connect fxrhangeOnline userPrincipalName sysanalystatexanpteco.com
- A . The tmdlets to search the UAl were not Imported into the session
- B . The UAL cannot be searched when using Microsoft 365 PowerShell
- C . The incorrect version of the FxhangeOnlineManagement module was installed
- D . The ExchangeOnlineManagement module was not installed
Which statement describes how an organization could use IPv6 in a Google Cloud deployment?
- A . IPv6 has to be configured for each compute node Individually
- B . IPv6 b enabled by default for global traffic between VPCs
- C . IPv6 is enabled by default for traffic within VPCs
- D . IPv6 needs to be terminated at an edge load balancer
A company using PaaS to host and develop their software application is experiencing a DOS attack.
What challenge will a DFIR analyst experience when investigating this attack?
- A . Restricted access to their application logs
- B . Resource scaling will affect access to logs
- C . Network logs are unavailable for review
- D . Network monitoring disabled by the company
Which is a limitation when adding GPUs to Google cloud VMs?
- A . They can only be added at VM creation
- B . Preemptible VMs do not support GPU addition
- C . Google limits the GPUs assigned to a single VM
- D . They are only available in specific zones
What can be inferred about the ARN below?
arn:aws:!am::457787814323:user/giac
- A . giac’s is a user In the AWS account 457787814323
- B . giac’s access Is testf kted to resources owned by AWS tenant 457787814323
- C . giac’s Is limited to roles defined under a single AWS organization
- D . giac’s user’s access key 10 is 457787814323
What 1$ a drawback of analyzing a snapshot outside of AWS?
- A . Incomplete data
- B . Long download time
- C . Incompatible image format
- D . Low latency
Which of the following is available with the free tier of service for CloudTrail?
- A . Single trail of management events delivered to Amazon
- B . Access to data-related API Cloud Trail events
- C . Access to CloudTrail Insights to detect anomalies
- D . Default trail maintained by AWS for more than 90 days
Which EBS volume type would be appropriate to support a business critical SQL server hosted In AWS?
- A . ST1
- B . GP3
- C . GP2
- D . I01
