GIAC GCED GIAC Certified Enterprise Defender Online Training
GIAC GCED Online Training
The questions for GCED were last updated at Dec 14,2025.
- Exam Code: GCED
- Exam Name: GIAC Certified Enterprise Defender
- Certification Provider: GIAC
- Latest update: Dec 14,2025
Which command tool can be used to change the read-only or hidden setting of the file in the screenshot?
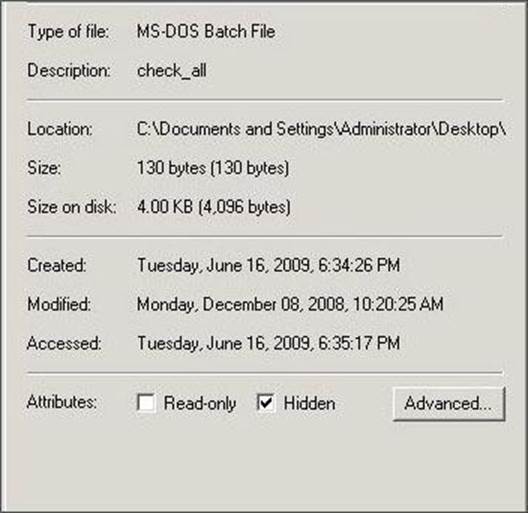
- A . attrib
- B . type
- C . tasklist
- D . dir
Which Unix administration tool is designed to monitor configuration changes to Cisco, Extreme and Foundry infrastructure devices?
- A . SNMP
- B . Netflow
- C . RANCID
- D . RMON
If a Cisco router is configured with the “service config” configuration statement, which of the following tools could be used by an attacker to apply a new router configuration?
- A . TFTPD
- B . Hydra
- C . Ettercap
- D . Yersinia
Who is ultimately responsible for approving methods and controls that will reduce any potential risk to an organization?
- A . Senior Management
- B . Data Owner
- C . Data Custodian
- D . Security Auditor
An internal host at IP address 10.10.50.100 is suspected to be communicating with a command and control whenever a user launches browser window.
What features and settings of Wireshark should be used to isolate and analyze this network traffic?
- A . Filter traffic using ip.src = = 10.10.50.100 and tcp.srcport = = 80, and use Expert Info
- B . Filter traffic using ip.src = = 10.10.50.100 and tcp.dstport = = 53, and use Expert Info
- C . Filter traffic using ip.src = = 10.10.50.100 and tcp.dstport = = 80, and use Follow TCP stream
- D . Filter traffic using ip.src = = 10.10.50.100, and use Follow TCP stream
Michael, a software engineer, added a module to a banking customer’s code. The new module deposits small amounts of money into his personal bank account. Michael has access to edit the code, but only code reviewers have the ability to commit modules to production. The code reviewers have a backlog of work, and are often willing to trust the software developers’ testing and confidence in the code.
Which technique is Michael most likely to engage to implement the malicious code?
- A . Denial of Service
- B . Race Condition
- C . Phishing
- D . Social Engineering
A company wants to allow only company-issued devices to attach to the wired and wireless networks. Additionally, devices that are not up-to-date with OS patches need to be isolated from the rest of the network until they are updated.
Which technology standards or protocols would meet these requirements?
- A . 802.1x and Network Access Control
- B . Kerberos and Network Access Control
- C . LDAP and Authentication, Authorization and Accounting (AAA)
- D . 802.11i and Authentication, Authorization and Accounting (AAA)
When attempting to collect data from a suspected system compromise, which of the following should generally be collected first?
- A . The network connections and open ports
- B . The contents of physical memory
- C . The current routing table
- D . A list of the running services
Before re-assigning a computer to a new employee, what data security technique does the IT department use to make sure no data is left behind by the previous user?
- A . Fingerprinting
- B . Digital watermarking
- C . Baselining
- D . Wiping
What feature of Wireshark allows the analysis of one HTTP conversation?
- A . Follow UDP Stream
- B . Follow TCP Stream
- C . Conversation list > IPV4
- D . Setting a display filter to ‘tcp’
Latest GCED Dumps Valid Version with 88 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund

