Refer to the exhibits.
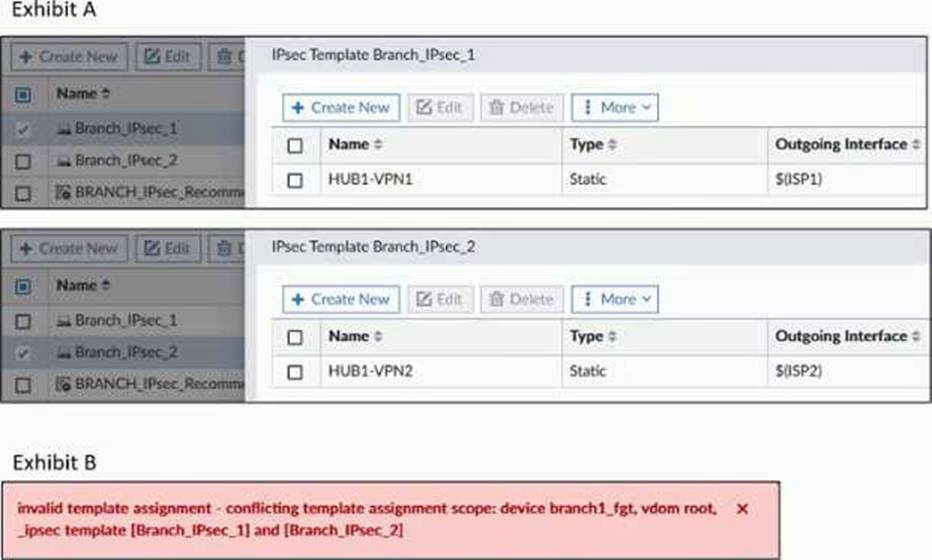
Exhibit A shows two IPsec templates to define Branch_IPsec_1 and Branch_IPsec_2. Each template defines a VPN tunnel.
Exhibit B shows the error message that FortiManager displayed when the administrator tried to assign the second template to the FortiGate device.
Which statement best explain the cause for this issue?
- A . You can assign only one template with a tunnel of fype static to each FortiGate device
- B . You can define only one IPsec tunnel from branch devices to HUB1.
- C . You can assign only one IPsec template to each FortiGate device.
- D . You should review the branch1_fgt configuration for the already configured tunnel with the name HUB1-VPN2.
C
Explanation:
The error message in Exhibit B indicates a conflicting template assignment. This occurs because FortiManager does not allow the assignment of multiple IPsec templates that define VPN tunnels with the same name or settings to the same FortiGate device. The conflict arises from trying to assign a second IPsec template to a device that already has one assigned.
Reference: This is based on Fortinet’s best practices and administrative guidelines which state that each FortiGate device should be assigned a unique IPsec template to avoid configuration conflicts.
Which statement about using BGP for ADVPN is true?
- A . You must use BGP to route traffic for both overlay and underlay links.
- B . You must configure AS path prepending.
- C . You must configure BGP communities.
- D . IBGP is preferred over EBGP, because IBGP preserves next hop information.
D
Explanation:
ADVPN is a technology that allows dynamic creation of IPsec tunnels between branch sites without requiring pre-configured policies or keys. BGP is a routing protocol that can be used to exchange routes between ADVPN peers. IBGP is a type of BGP that runs between routers in the same autonomous system (AS), while EBGP is a type of BGP that runs between routers in different ASes. IBGP is preferred over EBGP for ADVPN, because IBGP preserves the next hop information of the routes, which is needed to establish the IPsec tunnels. EBGP changes the next hop information to the EBGP peer address, which may not be reachable by the ADVPN peers. Therefore, using IBGP for ADVPN avoids the need to configure additional static routes or redistribute routes between BGP and another routing protocol. Reference = ADVPN with BGP as the routing protocol, ADVPN, SD-WAN self-healing with BGP, Technical Tip: ADVPN with BGP as the routing protocol
The statement that IBGP is preferred over EBGP for ADVPN because IBGP preserves next hop information (D) is true. In a typical ADVPN deployment, it’s beneficial to maintain next hop information across the network to ensure proper routing and optimal path selection.
Reference: This understanding comes from my knowledge of Fortinet’s SD-WAN and ADVPN configurations, where BGP’s behavior in terms of next hop preservation is a key consideration.
Which are three key routing principles in SD-WAN? (Choose three.)
- A . FortiGate performs route lookups for new sessions only.
- B . Regular policy routes have precedence over SD-WAN rules.
- C . SD-WAN rules have precedence over ISDB routes.
- D . By default, SD-WAN members are skipped if they do not have a valid route to the destination.
- E . By default, SD-WAN rules are skipped if the best route to the destination is not an SD-WAN member.
BDE
Explanation:
Study Guide 7.2, pages 125, 129, 151
Refer to the exhibit.
Which statement explains the output shown in the exhibit?
- A . FortiGate performed standard FIB routing on the session.
- B . FortiGate will not re-evaluate the session following a firewall policy change.
- C . FortiGate used 192.2.0.1 as the gateway for the original direction of the traffic.
- D . FortiGate must re-evaluate the session due to routing change.
D
Explanation:
The snat-route-change option is enabled by default. This option enables FortiGate to re-evaluate the routing table and select a new egress interface if the next hop IP address changes. This option only applies to sessions in the dirty state. Sessions in the log state are not affected by routing changes.
What are two common use cases for remote internet access (RIA)? (Choose two.)
- A . Provide direct internet access on spokes
- B . Provide internet access through the hub
- C . Centralize security inspection on the hub
- D . Provide thorough inspection on spokes
BC
Explanation:
B. Provide internet access through the hub: This involves routing branch or remote office internet traffic through a central hub, ensuring consistent security policies and possibly better management of network resources.
C. Centralize security inspection on the hub: With this approach, all internet-bound traffic from various spokes is inspected at the hub, leveraging centralized security mechanisms for thorough inspection and policy enforcement.
Refer to the exhibits.
An administrator is testing application steering in SD-WAN. Before generating test traffic, the administrator collected the information shown in exhibit A.
After generating GoToMeeting test traffic, the administrator examined the respective traffic log on FortiAnalyzer, which is shown in exhibit B. The administrator noticed that the traffic matched the implicit SD-WAN rule, but they expected the traffic to match rule ID 1.
Which two reasons explain why the traffic matched the implicit SD-WAN rule? (Choose two.)
- A . FortiGate did not refresh the routing information on the session after the application was detected.
- B . Port1 and port2 do not have a valid route to the destination.
- C . Full SSL inspection is not enabled on the matching firewall policy.
- D . The session 3-tuple did not match any of the existing entries in the ISDB application cache.
BC
Explanation:
Study guide 7.2 Page 191
Refer to the exhibit.
Which algorithm does SD-WAN use to distribute traffic that does not match any of the SD-WAN rules?
- A . All traffic from a source IP to a destination IP is sent to the same interface.
- B . All traffic from a source IP is sent to the same interface.
- C . All traffic from a source IP is sent to the most used interface.
- D . All traffic from a source IP to a destination IP is sent to the least used interface.
A
Explanation:
Study Guide 7.2, page 176.
Refer to the exhibits.
Exhibit A
Exhibit B
Exhibit A shows the SD-WAN performance SLA configuration, the SD-WAN rule configuration, and the application IDs of Facebook and YouTube. Exhibit B shows the firewall policy configuration and the underlay zone status.
Based on the exhibits, which two statements are correct about the health and performance of port1 and port2? (Choose two.)
- A . The performance is an average of the metrics measured for Facebook and YouTube traffic passing through the member.
- B . FortiGate is unable to measure jitter and packet loss on Facebook and YouTube traffic.
- C . FortiGate identifies the member as dead when there is no Facebook and YouTube traffic passing through the member.
- D . Non-TCP Facebook and YouTube traffic are not used for performance measurement.
A, D
Explanation:
Study Guide 7.2, pages 103 – 104. Another comment said "because without using application Control on the firewall policy, SDWAN can’t work" but there is a app control "default" defined on config.
Refer to the exhibit.
Which two statements about the IPsec VPN configuration and the status of the IPsec VPN tunnel are true? (Choose two.)
- A . FortiGate does not install IPsec static routes for remote protected networks in the routing table. Most Voted
- B . The phase 1 configuration supports the network-overlay setting. Most Voted
- C . FortiGate facilitated the negotiation of the T_INET_1_0_0 ADVPN shortcut over T_INET_1_0.
- D . Dead peer detection is disabled.
Refer to the exhibits.
Exhibit A shows the SD-WAN rule status and the learned BGP routes with community 65000:10.
Exhibit B shows the SD-WAN rule configuration, the BGP neighbor configuration, and the route map configuration.
The administrator wants to steer corporate traffic using routes tags in the SD-WAN rule ID 1.
However, the administrator observes that the corporate traffic does not match the SD-WAN rule ID 1.
Based on the exhibits, which configuration change is required to fix issue?
- A . In the dcl-lab-rm route map configuration, set set-route-tag to 10.
- B . In SD-WAN rule ID 1, change the destination to use ISDB entries.
- C . In the BGP neighbor configuration, apply the route map dcl-lab-rm in the outbound direction.
- D . In the dcl-lab-rm route map configuration, unset match-community.
What are two advantages of using an IPsec recommended template to configure an IPsec tunnel in a hub-and-spoke topology? (Choose two.)
- A . VPN monitor tool provides additional statistics for tunnels defined with an IPsec recommended template.
- B . FortiManager automatically installs IPsec tunnels to every spoke when they are added to the FortiManager ADOM.
- C . IPsec recommended template guides the administrator to use Fortinet recommended settings.
- D . IPsec recommended template ensures consistent settings between phase1 and phase2
CD
Explanation:
The IPsec recommended template assists administrators by providing preset configurations that align with Fortinet’s best practices, ensuring that the settings are optimally configured for security and performance. Additionally, it maintains uniformity in the settings applied across both phases of the IPsec tunnel, reducing the risk of misconfiguration and enhancing reliability and compatibility in the network.
Refer to the exhibit.
An administrator used the SD-WAN overlay template to prepare an IPsec configuration for a hub-and-spoke SD-WAN topology. The exhibit shows the installation preview for one FortiGate device.
In the exhibit, which statement best describes the configuration applied to the FortiGate device?
- A . It is a hub device. It can send ADVPN shortcut offers.
- B . It is a spoke device that establishes dynamic IPsec tunnels to the hub. The subnet range is 10.10.128.0/23.
- C . It is a spoke device that establishes dynamic IPsec tunnels to the hub. It can send ADVPN shortcut requests.
- D . It is a hub device and will automatically discover the spoke devices that are in the SD-WAN topology.
C
Explanation:
According to the SD-WAN 7.2 Study Guide, the SD-WAN overlay template simplifies the configuration of IPsec tunnels in a hub-and-spoke topology.
The template defines the following parameters:
type: dynamic for spokes, static for hubs
interface: the WAN interface to use for the IPsec tunnel
network-overlay: enable for spokes, disable for hubs
network-id: a unique identifier for each spoke
auto-discovery-sender: enable for hubs, disable for spokes
auto-discovery-receiver: enable for spokes, disable for hubs
Based on the exhibit, the FortiGate device has the following configuration:
type: dynamic
interface: port1
network-overlay: enable
network-id: 5
auto-discovery-sender: disable
auto-discovery-receiver: enable
Therefore, the FortiGate device is a spoke that establishes dynamic IPsec tunnels to the hub. It also has the network-overlay and auto-discovery-receiver options enabled, which means it can send ADVPN shortcut requests to other spokes when it receives a shortcut offer from the hub
Which three matching traffic criteria are available in SD-WAN rules? (Choose three.)
- A . Type of physical link connection
- B . Internet service database (ISDB) address object
- C . Source and destination IP address
- D . URL categories
- E . Application signatures
Which two interfaces are considered overlay links? (Choose two.)
- A . LAG
- B . IPsec
- C . Physical
- D . GRE
Refer to the exhibit.
Exhibit B
Exhibit A shows the system interface with the static routes and exhibit B shows the firewall policies on the managed FortiGate.
Based on the FortiGate configuration shown in the exhibits, what issue might you encounter when creating an SD-WAN zone for port1 and port2?
- A . port1 is assigned a manual IP address.
- B . port1 is referenced in a firewall policy.
- C . port2 is referenced in a static route.
- D . port1 and port2 are not administratively down.
Which two settings can you configure to speed up routing convergence in BGP? (Choose two.)
- A . update-source
- B . set-route-tag
- C . holdtime-timer
- D . link-down-failover
Refer to the exhibits.
Exhibit A shows the packet duplication rule configuration, the SD-WAN zone status output, and the sniffer output on FortiGate acting as the sender. Exhibit B shows the sniffer output on a FortiGate acting as the receiver.
The administrator configured packet duplication on both FortiGate devices. The sniffer output on the sender FortiGate shows that FortiGate forwards an ICMP echo request packet over three overlays, but it only receives one reply packet through T_INET_1_0.
Based on the output shown in the exhibits, which two reasons can cause the observed behavior? (Choose two.)
- A . On the receiver FortiGate, packet-de-duplication is enabled.
- B . The ICMP echo request packets sent over T_INET_0_0 and T_MPLS_0 were dropped along the way.
- C . The ICMP echo request packets received over T_INET_0_0 and T_MPLS_0 were offloaded to NPU.
- D . On the sender FortiGate, duplication-max-num is set to 3.
Which SD-WAN setting enables FortiGate to delay the recovery of ADVPN shortcuts?
- A . hold-down-time
- B . link-down-failover
- C . auto-discovery-shortcuts
- D . idle-timeout
Refer to the exhibits.
Exhibit A –
Exhibit B
Exhibit A shows a site-to-site topology between two FortiGate devices: branch1_fgt and dc1_fgt.
Exhibit B shows the system global and system settings configuration on dc1_fgt.
When branch1_client establishes a connection to dc1_host, the administrator observes that, on dc1_fgt, the reply traffic is routed over T_INET_0_0, even though T_INET_1_0 is the preferred member in the matching SD-WAN rule.
Based on the information shown in the exhibits, what configuration change must be made on dc1_fgt so dc1_fgt routes the reply traffic over T_INET_1_0?
- A . Enable auxiliary-session under config system settings.
- B . Disable tсp-session-without-syn under config system settings.
- C . Enable snat-route-change under config system global.
- D . Disable allow-subnet-overlap under config system settings.
What three characteristics apply to provisioning templates available on FortiManager? (Choose three.)
- A . You can apply a system template and a CLI template to the same FortiGate device.
- B . A CLI template can be of type CLI script or Perl script.
- C . A template group can include a system template and an SD-WAN template.
- D . A template group can contain CLI templates of both types.
- E . Templates are applied in order, from top to bottom.
BDE
Explanation:
According to the FortiManager Administration Guide, provisioning templates are used to configure FortiGate devices in a consistent and efficient way. There are different types of templates, such as system, IPsec, SD-WAN, certificate, and CLI templates. Some characteristics of provisioning templates are:
You can apply a system template and a CLI template to the same FortiGate device, as long as they do not have conflicting settings1.
A CLI template can be of type CLI script or Perl script. A CLI script template contains FortiOS CLI commands, while a Perl script template contains Perl code that can generate FortiOS CLI commands2.
A template group can include a system template and an SD-WAN template, as well as other types of templates. A template group is a collection of templates that can be applied to multiple devices at once3.
A template group can contain CLI templates of both types, as long as they do not have conflicting settings2.
Templates are applied in order, from top to bottom. The order of the templates in a template group determines the order in which they are applied to the devices3.
Refer to the exhibit.
Which configuration change is required if the responder FortiGate uses a dynamic routing protocol to exchange routes over IPsec?
- A . type must be set to static.
- B . mode-cfg must be enabled.
- C . exchange-interface-ip must be enabled.
- D . add-route must be disabled.
Which are two benefits of using CLI templates in FortiManager? (Choose two.)
- A . You can reference meta fields.
- B . You can configure interfaces as SD-WAN members without having to remove references first.
- C . You can configure FortiManager to sync local configuration changes made on the managed device,
to the CLI template. - D . You can configure advanced CLI settings.
Refer to the exhibit.
The device exchanges routes using IBGP.
Which two statements are correct about the IBGP configuration and routing information on the device? (Choose two.)
- A . Each BGP route is three hops away from the destination.
- B . ibgp-multipath is disabled.
- C . additional-path is enabled.
- D . You can run the get router info routing-table database command to display the additional paths.
Refer to the exhibit.
Based on the exhibit, which action does FortiGate take?
- A . FortiGate bounces port5 after it detects all SD-WAN members as dead.
- B . FortiGate fails over to the secondary device after it detects all SD-WAN members as dead.
- C . FortiGate brings up port5 after it detects all SD-WAN members as alive.
- D . FortiGate brings down port5 after it detects all SD-WAN members as dead.
What are two benefits of choosing packet duplication over FEC for data loss correction on noisy links? (Choose two.)
- A . Packet duplication can leverage multiple IPsec overlays for sending additional data.
- B . Packet duplication does not require a route to the destination.
- C . Packet duplication supports hardware offloading.
- D . Packet duplication uses smaller parity packets which results in less bandwidth consumption.
Refer to the exhibit.
The exhibit shows the SD-WAN rule status and configuration.
Based on the exhibit, which change in the measured packet loss will make T_INET_1_0 the new preferred member?
- A . When all three members have the same packet loss.
- B . When T_INET_0_0 has 4% packet loss.
- C . When T_INET_0_0 has 12% packet loss.
- D . When T_INET_1_0 has 4% packet loss.
What are two benefits of using the Internet service database (ISDB) in an SD-WAN rule? (Choose two.)
- A . The ISDB is dynamically updated and reduces administrative overhead.
- B . The ISDB requires application control to maintain signatures and perform load balancing.
- C . The ISDB applies rules to traffic from specific sources, based on application type.
- D . The ISDB contains the IP addresses and port ranges of well-known internet services.
Which statement about SD-WAN zones is true?
- A . An SD-WAN zone can contain only one type of interface.
- B . An SD-WAN zone can contain between 0 and 512 members.
- C . You cannot use an SD-WAN zone in static route definitions.
- D . You can configure up to 32 SD-WAN zones per VDOM.
D
Explanation:
SD-WAN zones are a group of interfaces that share the same SD-WAN settings, such as health check,
SLA, and load balancing. Some characteristics of SD-WAN zones are:
An SD-WAN zone can contain different types of interfaces, such as physical, VLAN, aggregate, and tunnel interfaces1.
An SD-WAN zone can contain up to 512 members1.
You can use an SD-WAN zone in static route definitions, as long as the destination interface is also an SD-WAN zone1.
You can configure up to 32 SD-WAN zones per VDOM1.
Which two statements about the SD-WAN zone configuration are true? (Choose two.)
- A . The service-sla-tie-break setting enables you to configure preferred member selection based on the best route to the destination.
- B . You can delete the default zones.
- C . The default zones are virtual-wan-link and SASE.
- D . An SD-WAN member can belong to two or more zones.
Exhibit.
The exhibit shows the output of the command diagnose sys sdwan health-check status collected on a FortiGate device.
Which two statements are correct about the health check status on this FortiGate device? (Choose two.)
- A . The health-check VPN_PING orders the members according to the lowest jitter.
- B . The interface T_INET_1 missed one SLA target.
- C . There is no SLA criteria configured for the health-check Level3_DNS.
- D . The interface T_INET_0 missed three SLA targets.
AC
Explanation:
According to the FortiGate / FortiOS 6.4.2 Administration Guide, the health check status command displays the status of the health check probes for each SD-WAN member interface.
The output includes the following information:
state: the current state of the interface, either alive or dead
packet-loss: the percentage of packets lost during the health check
latency: the average round-trip time in milliseconds
jitter: the variation in latency
mos: the mean opinion score, a measure of voice quality
bandwidth: the available bandwidth in kilobits per second for each direction (up, down, bi) sla map: a bitmap that indicates which SLA criteria are met or failed
Based on the exhibit, the following statements are correct:
The health-check VPN_PING orders the members according to the lowest jitter. This means that the interface with the lowest jitter value is listed first, followed by the next lowest, and so on1. In the exhibit, the order is T_MPLS, T_INET_1, and T_INET_0.
There is no SLA criteria configured for the health-check Level3_DNS. This means that the health check does not use any SLA parameters to determine the state of the interface2. In the exhibit, the sla map value is 0x0 for both port1 and port2, indicating that no SLA criteria are applied.
Refer to the exhibits.
Exhibit A
Exhibit B –
Exhibit A shows the configuration for an SD-WAN rule and exhibit B shows the respective rule status, the routing table, and the member status.
The administrator wants to understand the expected behavior for traffic matching the SD-WAN rule.
Based on the exhibits, what can the administrator expect for traffic matching the SD-WAN rule?
- A . The traffic will be load balanced across all three overlays.
- B . The traffic will be routed over T_INET_0_0.
- C . The traffic will be routed over T_MPLS_0.
- D . The traffic will be routed over T_INET_1_0.
Exhibit.
The exhibit shows VPN event logs on FortiGate.
In the output shown in the exhibit, which statement is true?
- A . There are no IPsec tunnel statistics log messages for ADVPN cuts.
- B . There is one shortcut tunnel built from master tunnel T_MPLS_0.
- C . The VPN tunnel T_MPLS_0 is a shortcut tunnel.
- D . The master tunnel T_INET_0 cannot accept the ADVPN shortcut.
B
Explanation:
VPN event logs record the status of VPN tunnels, such as the establishment, termination, or failure of a tunnel.
The output includes the following information:
logid: the log ID number
type: the log type, either traffic or event
subtype: the log subtype, either vpn or ipsec
level: the log level, either error, warning, or notice
vd: the virtual domain name
logdesc: the log description
msg: the log message
action: the log action, such as tunnel-up, tunnel-down, or tunnel-stats
remip: the remote IP address
locip: the local IP address
remport: the remote port number
locport: the local port number
outintf: the outgoing interface name
cookies: the IKE SA cookies
user: the user name
group: the user group name
useralt: the alternative user name
xauthuser: the XAuth user name
authgroup: the XAuth user group name
assignip: the assigned IP address
vpntunnel: the VPN tunnel name
tunnellip: the tunnel loopback IP address
tunnelid: the tunnel ID number
tunneltype: the tunnel type, either ipsec or ssl
duration: the tunnel duration in seconds
sentbyte: the number of bytes sent
rcvdbyte: the number of bytes received
nextstat: the next statistics interval in seconds
advpnsc: the ADVPN shortcut flag, either 0 or 1
Based on the exhibit, the following statement is true:
There is one shortcut tunnel built from master tunnel T_MPLS_0. This means that the VPN tunnel T_MPLS_0 is a master tunnel that can send ADVPN shortcut offers to other spokes, and the VPN tunnel T_MPLS_0_0 is a shortcut tunnel that is built from the master tunnel T_MPLS_01. In the exhibit, the log action for T_MPLS_0 is tunnel-up, and the log action for T_MPLS_0_0 is shortcut-up. The advpnsc flag for T_MPLS_0 is 0, indicating that it is not a shortcut tunnel, while the advpnsc flag for T_MPLS_0_0 is 1, indicating that it is a shortcut tunnel.
Refer to the exhibits.
Exhibit A
Exhibit B
Exhibit A shows the source NAT (SNAT) global setting and exhibit B shows the routing table on FortiGate.
Based on the exhibits, which two actions does FortiGate perform on existing sessions established over port2, if the administrator increases the static route priority on port2 to 20? (Choose two.)
- A . FortiGate flags the sessions as dirty.
- B . FortiGate continues routing the sessions with no SNAT, over port2.
- C . FortiGate performs a route lookup for the original traffic only.
- D . FortiGate updates the gateway information of the sessions with SNAT so that they use port1 instead of port2.
What is the route-tag setting in an SD-WAN rule used for?
- A . To indicate the routes for health check probes.
- B . To indicate the destination of a rule based on learned BGP prefixes.
- C . To indicate the routes that can be used for routing SD-WAN traffic.
- D . To indicate the members that can be used to route SD-WAN traffic.
Refer to the exhibit.
Two hub-and-spoke groups are connected through a site-to-site IPsec VPN between Hub 1 and Hub 2. The administrator configured ADVPN on both hub-and-spoke groups.
Which two outcomes are expected if a user in Toronto sends traffic to London? (Choose two.)
- A . London generates an IKE information message that contains the Toronto public IP address.
- B . Traffic from Toronto to London triggers the dynamic negotiation of a direct site-to-site VPN.
- C . Toronto needs to establish a site-to-site tunnel with Hub 2 to bypass Hub 1.
- D . The first packets from Toronto to London are routed through Hub 1 then to Hub 2.
Refer to the exhibit.
An administrator is troubleshooting SD-WAN on FortiGate. A device behind branch1_fgt generates traffic to the 10.0.0.0/8 network. The administrator expects the traffic to match SD-WAN rule ID 1 and be routed over T_INET_0_0. However, the traffic is routed over T_INET_1_0.
Based on the output shown in the exhibit, which two reasons can cause the observed behavior? (Choose two.)
- A . The traffic matches a regular policy route configured with T_INET_1_0 as the outgoing device.
- B . T_INET_1_0 has a lower route priority value (higher priority) than T_INET_0_0.
- C . T_INET_0_0 does not have a valid route to the destination.
- D . T_INET_1_0 has a higher member configuration priority than T_INET_0_0.
Refer to the exhibit.
Which statement about the role of the ADVPN device in handling traffic is true?
- A . This is a spoke that has received a query from a remote hub and has forwarded the response to its hub.
- B . Two hubs, 10.0.1.101 and 10.0.2.101, are receiving and forwarding queries between each other.
- C . This is a hub that has received a query from a spoke and has forwarded it to another spoke.
- D . Two spokes, 192.2.0.1 and 10.0.2.101, forward their queries to their hubs.
The SD-WAN overlay template helps to prepare SD-WAN deployments. To complete the tasks performed by the SD-WAN overlay template, the administrator must perform some post-run tasks.
What are three mandatory post-run tasks that must be performed? (Choose three.)
- A . Create policy packages for branch devices.
- B . Assign an sdwan_id metadata variable to each device (branch and hub}.
- C . Configure routing through overlay tunnels created by the SD-WAN overlay template.
- D . Assign a branch_id metadata variable to each branch device.
- E . Configure SD-WAN rules.
Which diagnostic command can you use to show the member utilization statistics measured by performance SLAs for the last 10 minutes?
- A . diagnose sys sdwan sla-log
- B . diagnose ays sdwan health-check
- C . diagnose sys sdwan intf-sla-log
- D . diagnose sys sdwan log
Which two statements about SLA targets and SD-WAN rules are true? (Choose two.)
- A . SD-WAN rules use SLA targets to check if the preferred members meet the SLA requirements
- B . Member metrics are measured only if an SLA target is configured
- C . When configuring an SD-WAN rule you can select multiple SLA targets of the same performance SLA
- D . SLA targets are used only by SD-WAN rules that are configured with Lowest Cost (SLA) or Maximize Bandwidth (SLA) as strategy
Which two protocols in the IPsec suite are most used for authentication and encryption? (Choose two.)
- A . Encapsulating Security Payload (ESP)
- B . Secure Shell (SSH)
- C . Internet Key Exchange (IKE)
- D . Security Association (SA)
Which two performance SLA protocols enable you to verify that the server response contains a specific value? (Choose two.)
- A . http
- B . icmp
- C . twamp
- D . dns
A, D
Explanation:
Performance SLA (Service Level Agreement) protocols are used in SD-WAN to monitor the quality and performance of various network services.
The two protocols that specifically allow for verifying a specific value in the server response are:
HTTP (Hypertext Transfer Protocol): HTTP is the foundation of data communication on the World Wide Web. It allows for fetching resources, such as HTML documents. You can configure an HTTP performance SLA to send specific requests (e.g., GET or POST) and then check if the response body contains a particular string or value. This is useful for validating web server functionality and content delivery.
DNS (Domain Name System): DNS is responsible for translating domain names into IP addresses. A DNS performance SLA can be set up to query a specific domain and verify that the returned IP address or other DNS record values match what is expected. This helps ensure proper name resolution and accessibility of resources.
Which two conclusions for traffic that matches the traffic shaper are true? (Choose two.)
- A . The traffic shaper drops packets if the bandwidth is less than 2500 KBps.
- B . The measured bandwidth is less than 100 KBps.
- C . The traffic shaper drops packets if the bandwidth exceeds 6250 KBps.
- D . The traffic shaper limits the bandwidth of each source IP to a maximum of 6250 KBps.
Which CLI command do you use to perform real-time troubleshooting for ADVPN negotiation?
- A . get router info routing-table all
- B . diagnose debug application ike
- C . diagnose vpn tunnel list
- D . get ipsec tunnel list
B
Explanation:
IKE real-time debug – useful when debugging ADVPN shortcut messages and spoke-to-spoke negotiations.
• diagnose debug console timestamp enable
• diagnose vpn ike log filter clear
• diagnose vpn ike log filter mdst-addr4 <ip.of.hub> <ip.of.spoke>
• diagnose debug application ike -1
• diagnose debug enable
Which two statements are correct when traffic matches the implicit SD-WAN rule? (Choose two.)
- A . The sdwan_service_id flag in the session information is 0.
- B . All SD-WAN rules have the default setting enabled.
- C . Traffic does not match any of the entries in the policy route table.
- D . Traffic is load balanced using the algorithm set for the v4-ecmp-mode setting.
A, C
Explanation:
sdwan_service_id is 0 = match SD-WAN implicit rule, study guide 7.0 page 120, 7.2 page 149 SD-WAN rules internally are interpreted as a Policy route, so when the traffic doesn’t match with any policy route, it will be flowing by implict policy.
