Fortinet NSE7_OTS-7.2 Fortinet NSE 7 – OT Security7.2 Online Training
Fortinet NSE7_OTS-7.2 Online Training
The questions for NSE7_OTS-7.2 were last updated at Apr 11,2025.
- Exam Code: NSE7_OTS-7.2
- Exam Name: Fortinet NSE 7 - OT Security7.2
- Certification Provider: Fortinet
- Latest update: Apr 11,2025
What are two benefits of a Nozomi integration with FortiNAC? (Choose two.)
- A . Enhanced point of connection details
- B . Direct VLAN assignment
- C . Adapter consolidation for multi-adapter hosts
- D . Importation and classification of hosts
Which three criteria can a FortiGate device use to look for a matching firewall policy to process traffic? (Choose three.)
- A . Services defined in the firewall policy.
- B . Source defined as internet services in the firewall policy
- C . Lowest to highest policy ID number
- D . Destination defined as internet services in the firewall policy
- E . Highest to lowest priority defined in the firewall policy
Refer to the exhibit and analyze the output.
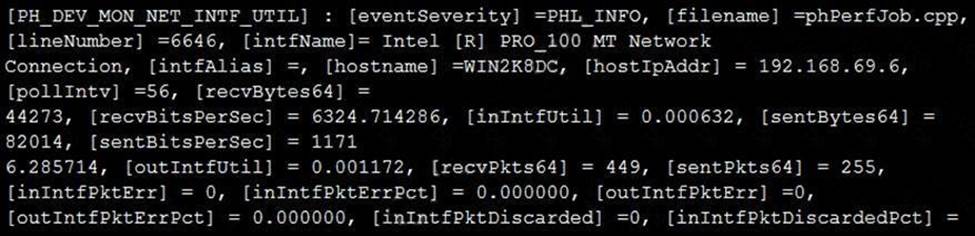
Which statement about the output is true?
- A . This is a sample of a FortiAnalyzer system interface event log.
- B . This is a sample of an SNMP temperature control event log.
- C . This is a sample of a PAM event type.
- D . This is a sample of FortiGate interface statistics.
Which three Fortinet products can be used for device identification in an OT industrial control system (ICS)? (Choose three.)
- A . FortiNAC
- B . FortiManager
- C . FortiAnalyzer
- D . FortiSIEM
- E . FortiGate
Refer to the exhibit
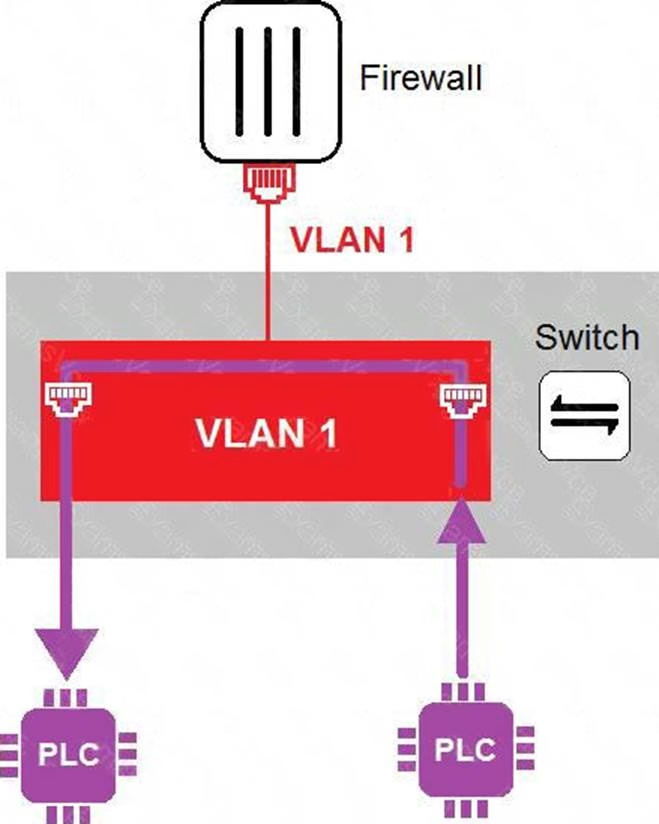
In the topology shown in the exhibit, both PLCs can communicate directly with each other, without going through the firewall.
Which statement about the topology is true?
- A . PLCs use IEEE802.1Q protocol to communicate each other.
- B . An administrator can create firewall policies in the switch to secure between PLCs.
- C . This integration solution expands VLAN capabilities from Layer 2 to Layer 3.
- D . There is no micro-segmentation in this topology.
In a wireless network integration, how does FortiNAC obtain connecting MAC address information?
- A . RADIUS
- B . Link traps
- C . End station traffic monitoring
- D . MAC notification traps
Which three common breach points can be found in a typical OT environment? (Choose three.)
- A . Global hat
- B . Hard hat
- C . VLAN exploits
- D . Black hat
- E . RTU exploits
Refer to the exhibit.
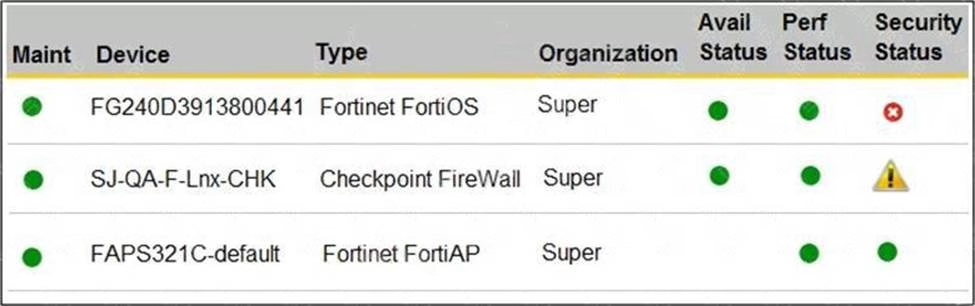
You are navigating through FortiSIEM in an OT network.
How do you view information presented in the exhibit and what does the FortiGate device security status tell you?
- A . In the PCI logging dashboard and there are one or more high-severity security incidents for the FortiGate device.
- B . In the summary dashboard and there are one or more high-severity security incidents for the FortiGate device.
- C . In the widget dashboard and there are one or more high-severity incidents for the FortiGate device.
- D . In the business service dashboard and there are one or more high-severity security incidents for the FortiGate device.
An OT network administrator is trying to implement active authentication.
Which two methods should the administrator use to achieve this? (Choose two.)
- A . Two-factor authentication on FortiAuthenticator
- B . Role-based authentication on FortiNAC
- C . FSSO authentication on FortiGate
- D . Local authentication on FortiGate
Refer to the exhibit.
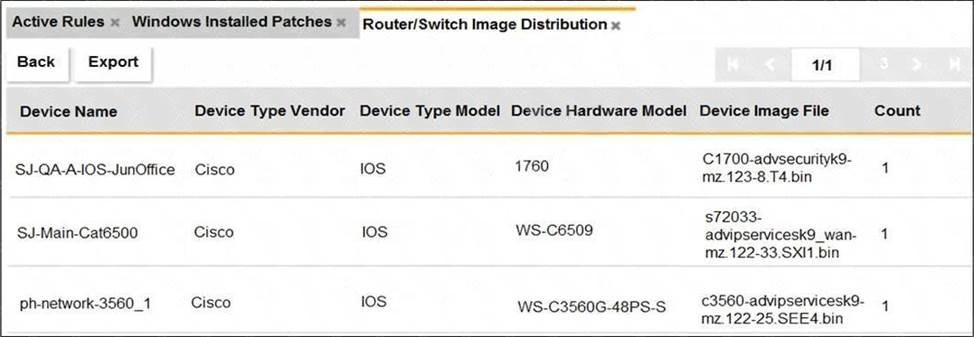
An OT administrator ran a report to identify device inventory in an OT network.
Based on the report results, which report was run?
- A . A FortiSIEM CMDB report
- B . A FortiAnalyzer device report
- C . A FortiSIEM incident report
- D . A FortiSIEM analytics report
Latest NSE7_OTS-7.2 Dumps Valid Version with 49 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund

