Fortinet NSE7_EFW-7.0 Fortinet NSE 7 – Enterprise Firewall 7.0 Online Training
Fortinet NSE7_EFW-7.0 Online Training
The questions for NSE7_EFW-7.0 were last updated at Dec 16,2025.
- Exam Code: NSE7_EFW-7.0
- Exam Name: Fortinet NSE 7 - Enterprise Firewall 7.0
- Certification Provider: Fortinet
- Latest update: Dec 16,2025
A FortiGate is rebooting unexpectedly without any apparent reason.
What troubleshooting tools could an administrator use to get more information about the problem? (Choose two.)
- A . Firewall monitor.
- B . Policy monitor.
- C . Logs.
- D . Crashlogs.
Refer to the exhibits, which show the configuration on FortiGate and partial internet session information from a user on the internal network.
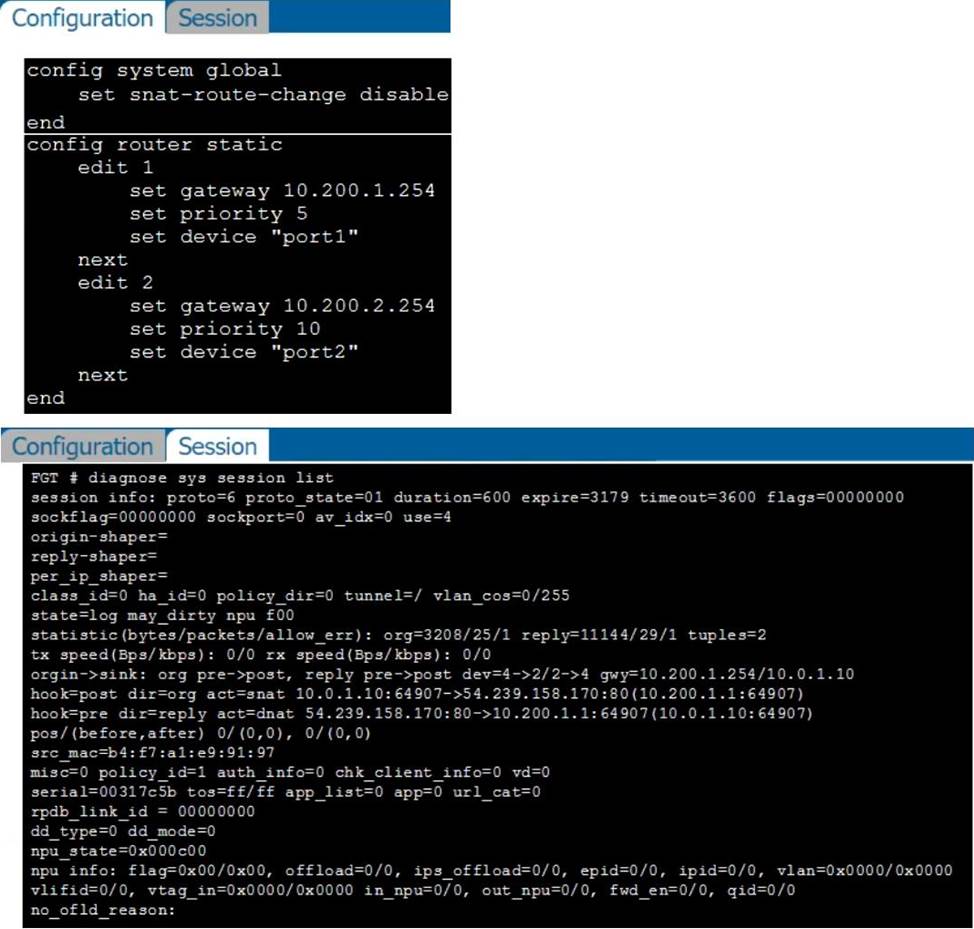
An administrator would like to test session failover between the two service provider connections.
What changes must the administrator make to force this existing session to immediately start using the other interface? (Choose two.)
- A . Configure set snat-route-change enable.
- B . Change the priority of the port2 static route to 5.
- C . Change the priority of the port1 static route to 11.
- D . unset snat-route-change to return it to the default setting.
A,C
Explanation:
Enterprise_Firewall_7.0_Study_Guide-Online.pdf p 148-149
Which statement about IKE and IKE NAT-T is true?
- A . IKE is used to encapsulate ESP traffic in some situations, and IKE NAT-T is used only when the local FortiGate is using NAT on the IPsec interface.
- B . IKE is the standard implementation for IKEv1 and IKE NAT-T is an extension added in IKEv2.
- C . They both use UDP as their transport protocol and the port number is configurable.
- D . They each use their own IP protocol number.
C
Explanation:
IKE without NAT-T runs over UDP port 500. IKE with NAT-T runs over UDP port 4500. It can be configurable – https://docs.fortinet.com/document/fortigate/7.0.0/new-features/33578/configurable-ike-port
An administrator cannot connect to the GIU of a FortiGate unit with the IP address 10.0.1.254. The administrator runs the debug flow while attempting the connection using HTTP.
The output of the debug flow is shown in the exhibit:
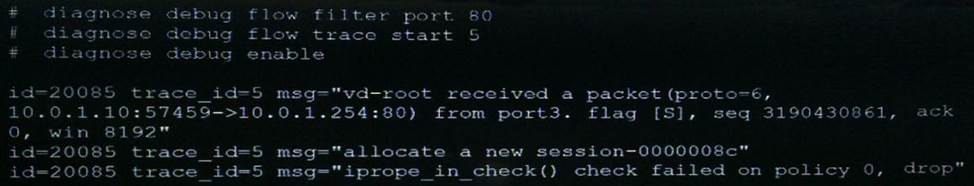
Based on the error displayed by the debug flow, which are valid reasons for this problem? (Choose two.)
- A . HTTP administrative access is disabled in the FortiGate interface with the IP address 10.0.1.254.
- B . Redirection of HTTP to HTTPS administrative access is disabled.
- C . HTTP administrative access is configured with a port number different than 80.
- D . The packet is denied because of reverse path forwarding check.
View the exhibit, which contains the output of a debug command, and then answer the question below.
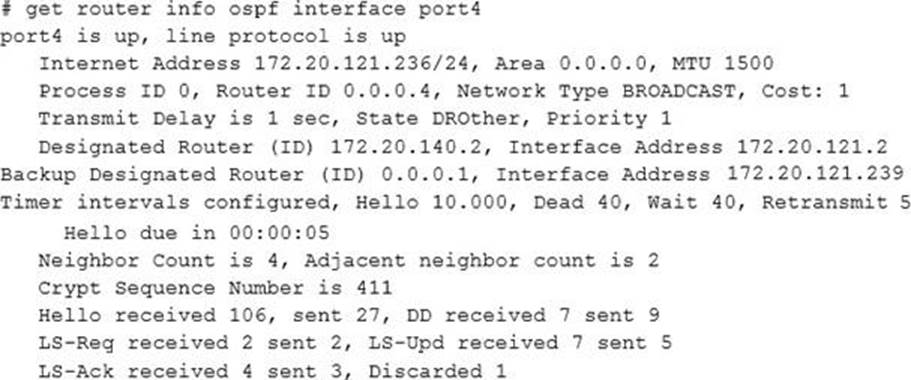
Which of the following statements about the exhibit are true? (Choose two.)
- A . In the network on port4, two OSPF routers are down.
- B . Port4 is connected to the OSPF backbone area.
- C . The local FortiGate’s OSPF router ID is 0.0.0.4
- D . The local FortiGate has been elected as the OSPF backup designated router.
Refer to the exhibit, which contains the output of a debug command.
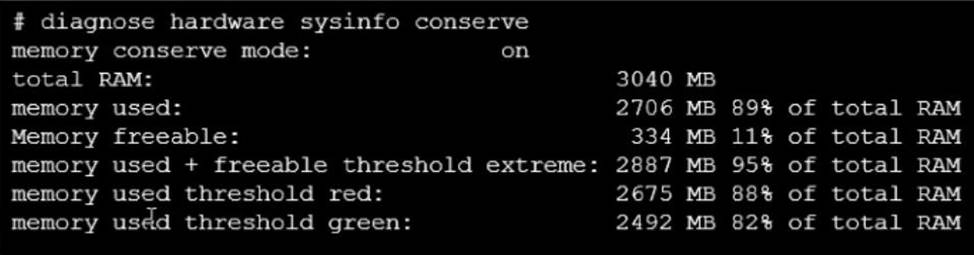
If the default settings are in place, what can be concluded about the conserve mode shown in the exhibit?
- A . FortiGate is currently blocking all new sessions regardless of the content inspection requirements or configuration settings due to high memory use.
- B . FortiGate is currently allowing new sessions that require flow-based or proxy-based content inspection but is not performing inspection on those sessions.
- C . FortiGate is currently blocking new sessions that require flow-based or proxy-based content inspection.
- D . FortiGate is currently allowing new sessions that require flow-based content inspection and blocking sessions that require proxy-based content inspection.
View the exhibit, which contains a partial web filter profile configuration, and then answer the question below.
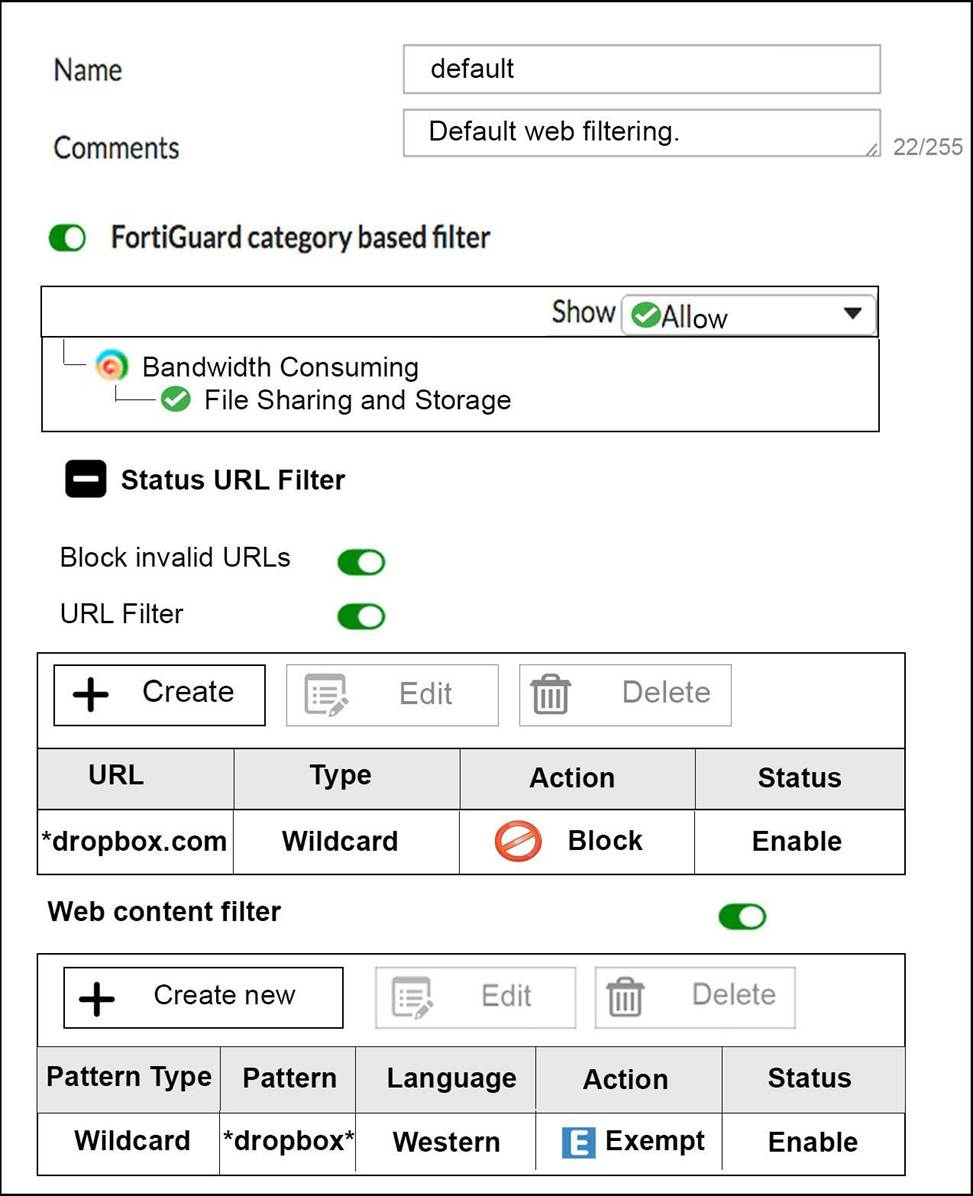
Which action will FortiGate take if a user attempts to access www.dropbox.com, which is categorized as File Sharing and Storage?
- A . FortiGate will exempt the connection based on the Web Content Filter configuration.
- B . FortiGate will block the connection based on the URL Filter configuration.
- C . FortiGate will allow the connection based on the FortiGuard category based filter configuration.
- D . FortiGate will block the connection as an invalid URL.
B
Explanation:
fortigate does it in order Static URL -> FortiGuard C > Content -> Advanced (java, cookie removal..)so block it in first step
Which of the following statements are true regarding the SIP session helper and the SIP application layer gateway (ALG)? (Choose three.)
- A . SIP session helper runs in the kernel; SIP ALG runs as a user space process.
- B . SIP ALG supports SIP HA failover; SIP helper does not.
- C . SIP ALG supports SIP over IPv6; SIP helper does not.
- D . SIP ALG can create expected sessions for media traffic; SIP helper does not.
- E . SIP helper supports SIP over TCP and UDP; SIP ALG supports only SIP over UDP.
An administrator has configured two FortiGate devices for an HA cluster. While testing HA failover, the administrator notices that some of the switches in the network continue to send traffic to the former primary device.
What can the administrator do to fix this problem?
- A . Configure remote link monitoring to detect an issue in the forwarding path.
- B . Configure set send-garp-on-failover enable under config system ha on both cluster members.
- C . Verify that the speed and duplex settings match between the FortiGate interfaces and the connected switch ports.
- D . Configure set link-failed-signal enable under config system ha on both cluster members.
D
Explanation:
Virtual MAC Address and Failover – The new primary broadcasts Gratuitous ARP packets to notify the network that each virtual MAC is now reachable through a different switch port. – Some high-end switches might not clear their MAC table correctly after a failover – Solution: Force former primary to shut down all its interfaces for one second when the failover happens (excluding heartbeat and reserved management interfaces): #Config system ha set link-failed-signal enable end – This simulates a link failure that clears the related entries from MAC table of the switches.
Examine the output of the ‘diagnose ips anomaly list’ command shown in the exhibit; then answer the question below.
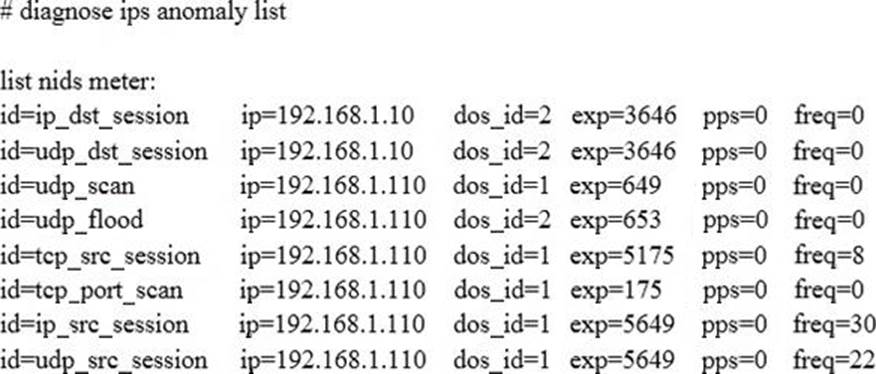
Which IP addresses are included in the output of this command?
- A . Those whose traffic matches a DoS policy.
- B . Those whose traffic matches an IPS sensor.
- C . Those whose traffic exceeded a threshold of a matching DoS policy.
- D . Those whose traffic was detected as an anomaly by an IPS sensor.
Latest NSE7_EFW-7.0 Dumps Valid Version with 115 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund

