Fortinet NSE6_FWF-6.4 Fortinet NSE 6 – Secure Wireless LAN 6.4 Online Training
Fortinet NSE6_FWF-6.4 Online Training
The questions for NSE6_FWF-6.4 were last updated at Dec 14,2025.
- Exam Code: NSE6_FWF-6.4
- Exam Name: Fortinet NSE 6 - Secure Wireless LAN 6.4
- Certification Provider: Fortinet
- Latest update: Dec 14,2025
Which two statements about distributed automatic radio resource provisioning (DARRP) are correct? (Choose two.)
- A . DARRP performs continuous spectrum analysis to detect sources of interference. It uses this information to allow the AP to select the optimum channel.
- B . DARRP performs measurements of the number of BSSIDs and their signal strength (RSSI). The controller then uses this information to select the optimum channel for the AP.
- C . DARRP measurements can be scheduled to occur at specific times.
- D . DARRP requires that wireless intrusion detection (WIDS) be enabled to detect neighboring devices.
Which factor is the best indicator of wireless client connection quality?
- A . Downstream link rate, the connection rate for the AP to the client
- B . The receive signal strength (RSS) of the client at the AP
- C . Upstream link rate, the connection rate for the client to the AP
- D . The channel utilization of the channel the client is using
When configuring Auto TX Power control on an AP radio, which two statements best describe how the radio responds? (Choose two.)
- A . When the AP detects any other wireless signal stronger that -70 dBm, it will reduce its transmission power until it reaches the minimum configured TX power limit.
- B . When the AP detects PF Interference from an unknown source such as a cordless phone with a signal stronger that -70 dBm, it will increase its transmission power until it reaches the maximum configured TX power limit.
- C . When the AP detects any wireless client signal weaker than -70 dBm, it will reduce its transmission power until it reaches the maximum configured TX power limit.
- D . When the AP detects any interference from a trusted neighboring AP stronger that -70 dBm, it will reduce its transmission power until it reaches the minimum configured TX power limit.
Refer to the exhibits.
Exhibit A
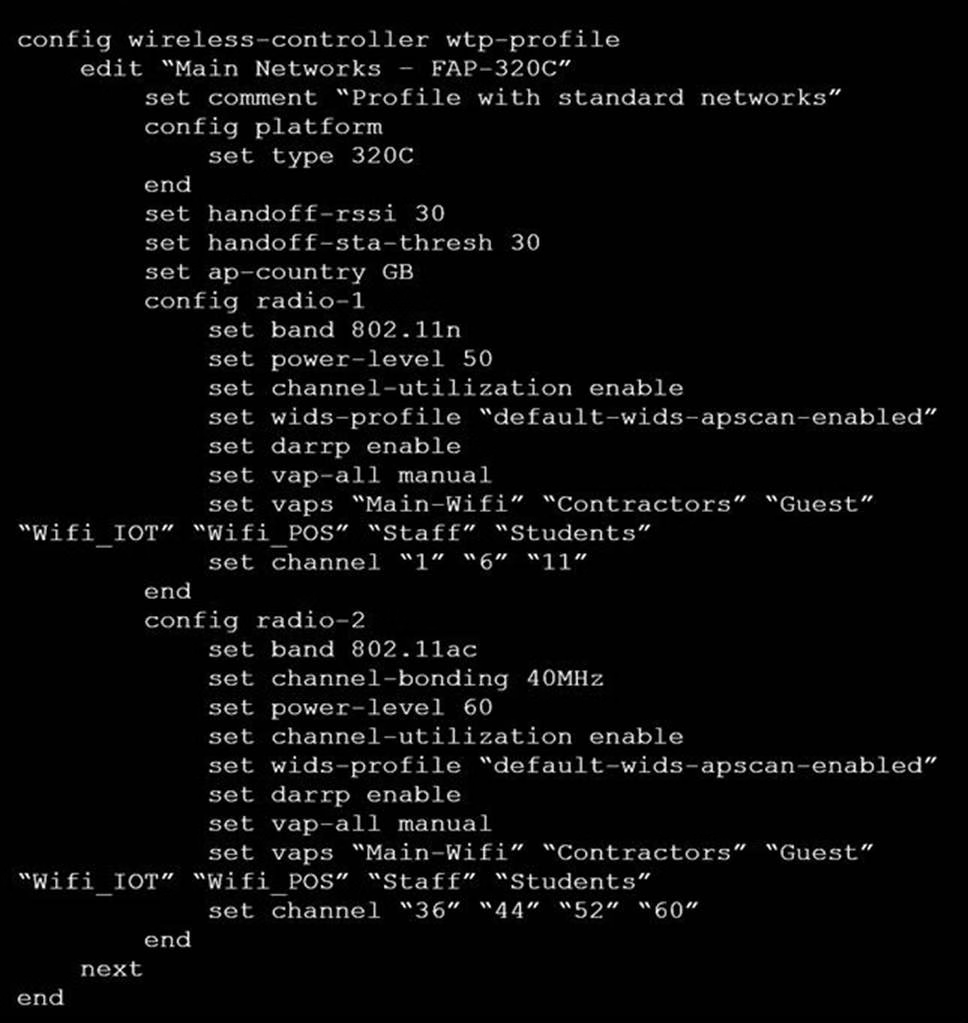
Exhibit B
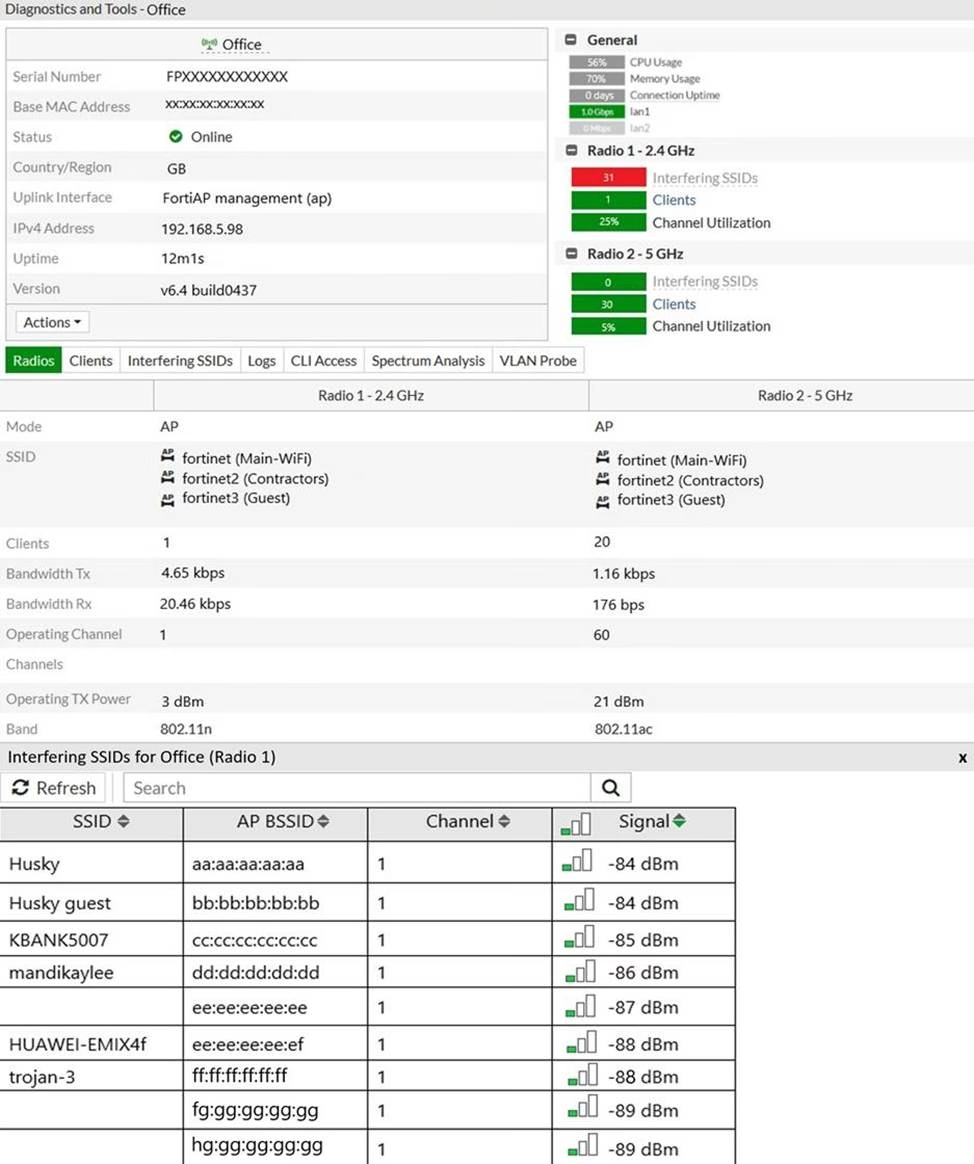
Exhibit C
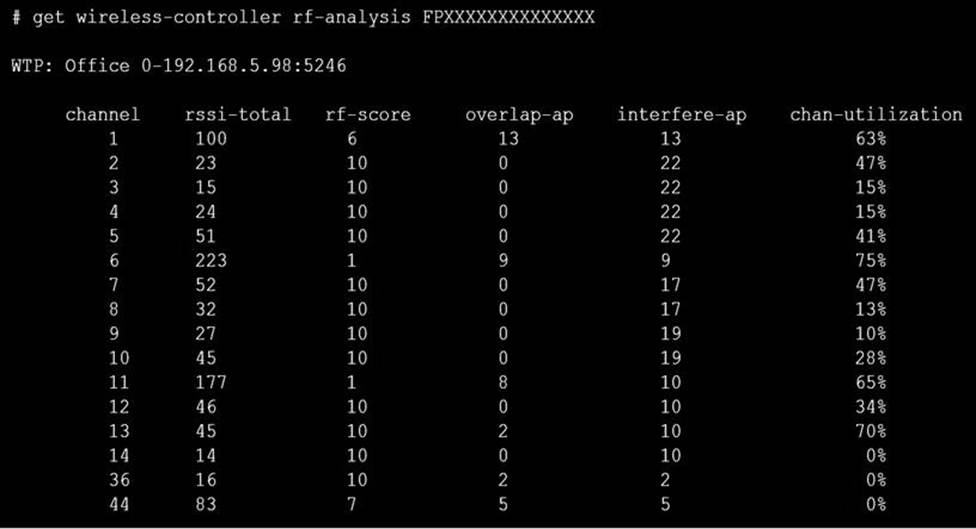
A wireless network has been installed in a small office building and is being used by a business to connect its wireless clients. The network is used for multiple purposes, including corporate access, guest access, and connecting point-of-sale and IoТ devices.
Users connecting to the guest network located in the reception area are reporting slow performance. The network administrator is reviewing the information shown in the exhibits as part of the ongoing investigation of the problem. They show the profile used for the AP and the controller RF analysis output together with a screenshot of the GUI showing a summary of the AP and its neighboring APs.
To improve performance for the users connecting to the guest network in this area, which configuration change is most likely to improve performance?
- A . Increase the transmission power of the AP radios
- B . Enable frequency handoff on the AP to band steer clients
- C . Reduce the number of wireless networks being broadcast by the AP
- D . Install another AP in the reception area to improve available bandwidth
Which two statements about background rogue scanning are correct? (Choose two.)
- A . A dedicated radio configured for background scanning can support the connection of wireless clients
- B . When detecting rogue APs, a dedicated radio configured for background scanning can suppress the rogue AP
- C . Background rogue scanning requires DARRP to be enabled on the AP instance
- D . A dedicated radio configured for background scanning can detect rogue devices on all other channels in its configured frequency band
When configuring a wireless network for dynamic VLAN allocation, which three IETF attributes must be supplied by the radius server? (Choose three.)
- A . 81 Tunnel-Private-Group-ID
- B . 65 Tunnel-Medium-Type
- C . 83 Tunnel-Preference
- D . 58 Egress-VLAN-Name
- E . 64 Tunnel-Type
Which two phases are part of the process to plan a wireless design project? (Choose two.)
- A . Project information phase
- B . Hardware selection phase
- C . Site survey phase
- D . Installation phase
When enabling security fabric on the FortiGate interface to manage FortiAPs, which two types of communication channels are established between FortiGate and FortiAPs? (Choose two.)
- A . Control channels
- B . Security channels
- C . FortLink channels
- D . Data channels
Part of the location service registration process is to link FortiAPs in FortiPresence.
Which two management services can configure the discovered AP registration information from the FortiPresence cloud? (Choose two.)
- A . AP Manager
- B . FortiAP Cloud
- C . FortiSwitch
- D . FortiGate
Which two configurations are compatible for Wireless Single Sign-On (WSSO)? (Choose two.)
- A . A VAP configured for captive portal authentication
- B . A VAP configured for WPA2 or 3 Enterprise
- C . A VAP configured to authenticate locally on FortiGate
- D . A VAP configured to authenticate using a radius server
Latest NSE6_FWF-6.4 Dumps Valid Version with 30 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund

