Which two statements about running a vulnerability scan are true? (Choose two.)
- A . You should run the vulnerability scan during a maintenance window.
- B . You should run the vulnerability scan in a test environment.
- C . Vulnerability scanning increases the load on FortiWeb, so it should be avoided.
- D . You should run the vulnerability scan on a live website to get accurate results.
A, B
Explanation:
Should the Vulnerability Scanner allow it, SVMS will set the scan schedule (or schedules) to run in a maintenance window. SVMS will advise Client of the scanner’s ability to complete the scan(s) within the maintenance window.
Vulnerabilities on live web sites. Instead, duplicate the web site and its database in a test environment.
Reference:
https://www.trustwave.com/media/17427/trustwave_mss_managed-3rd-party-vulnerability-scanning.pdf
https://help.fortinet.com/fweb/552/Content/FortiWeb/fortiweb-admin/vulnerability_scans.htm
FortiWeb offers the same load balancing algorithms as FortiGate.
Which two Layer 7 switch methods does FortiWeb also offer? (Choose two.)
- A . Round robin
- B . HTTP session-based round robin
- C . HTTP user-based round robin
- D . HTTP content routes
A, D
Explanation:
Reference: https://docs.fortinet.com/document/fortiweb/6.3.0/administration-guide/399384/defining-your-web-servers
http://fortinet.globalgate.com.ar/pdfs/FortiWeb/FortiWeb_DS.pdf
Which would be a reason to implement HTTP rewriting?
- A . The original page has moved to a new URL
- B . To replace a vulnerable function in the requested URL
- C . To send the request to secure channel
- D . The original page has moved to a new IP address
B
Explanation:
Create a new URL rewriting rule.
Reference: https://docs.fortinet.com/document/fortiweb/6.3.0/administration-guide/961303/rewriting-redirecting
Refer to the exhibit.
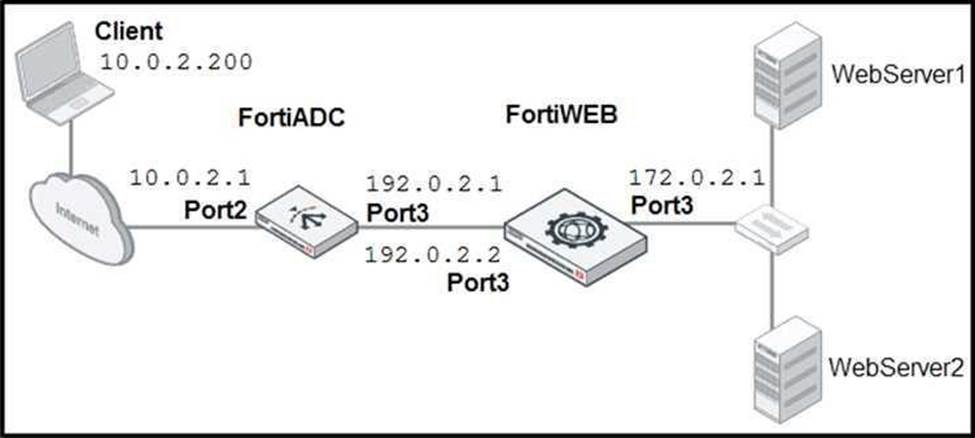
FortiADC is applying SNAT to all inbound traffic going to the servers. When an attack occurs, FortiWeb blocks traffic based on the 192.0.2.1 source IP address, which belongs to FortiADC. The setup is breaking all connectivity and genuine clients are not able to access the servers .
What must the administrator do to avoid this problem? (Choose two.)
- A . Enable the Use X-Forwarded-For setting on FortiWeb.
- B . No Special configuration is required; connectivity will be re-established after the set timeout.
- C . Place FortiWeb in front of FortiADC.
- D . Enable the Add X-Forwarded-For setting on FortiWeb.
A, C
Explanation:
Configure your load balancer to insert or append to an X-Forwarded-For:, X-Real-IP:, or other HTTP X-header. Also configure FortiWeb to find the original attacker’s or client’s IP address in that HTTP header
Reference: https://help.fortinet.com/fweb/560/Content/FortiWeb/fortiweb-admin/planning_topology.htm
Which statement about local user accounts is true?
- A . They are best suited for large environments with many users.
- B . They cannot be used for site publishing.
- C . They must be assigned, regardless of any other authentication.
- D . They can be used for SSO.
Refer to the exhibit.
Based on the configuration, what would happen if this FortiWeb were to lose power? (Choose two.)
- A . Traffic that passes between port5 and port6 will be inspected.
- B . Traffic will be interrupted between port3 and port4.
- C . All traffic will be interrupted.
- D . Traffic will pass between port5 and port6 uninspected.
B, D
Explanation:
Reference: https://docs.fortinet.com/document/fortiweb/6.3.10/administration-guide/33485/fail-to-wire-for-power-loss-reboots
Refer to the exhibit.
FortiWeb is configured to block traffic from Japan to your web application server. However, in the logs, the administrator is seeing traffic allowed from one particular IP address which is geo-located in Japan.
What can the administrator do to solve this problem? (Choose two.)
- A . Manually update the geo-location IP addresses for Japan.
- B . If the IP address is configured as a geo reputation exception, remove it.
- C . Configure the IP address as a blacklisted IP address.
- D . If the IP address is configured as an IP reputation exception, remove it.
Which algorithm is used to build mathematical models for bot detection?
- A . HCM
- B . SVN
- C . SVM
- D . HMM
C
Explanation:
FortiWeb uses SVM (Support Vector Machine) algorithm to build up the bot detection model
Reference: https://docs.fortinet.com/document/fortiweb/6.3.7/administration-guide/193258/machine-learning
A client is trying to start a session from a page that would normally be accessible only after the client has logged in.
When a start page rule detects the invalid session access, what can FortiWeb do? (Choose three.)
- A . Display an access policy message, then allow the client to continue
- B . Redirect the client to the login page
- C . Allow the page access, but log the violation
- D . Prompt the client to authenticate
- E . Reply with a 403 Forbidden HTTP error
B, C, E
Explanation:
Reference: https://help.fortinet.com/fweb/607/Content/FortiWeb/fortiweb-admin/specify_urls_to_initiate.htm
Refer to the exhibit.
Many legitimate users are being identified as bots. FortiWeb bot detection has been configured with the settings shown in the exhibit. The FortiWeb administrator has already verified that the current model is accurate.
What can the administrator do to fix this problem, making sure that real bots are not allowed through FortiWeb?
- A . Change Model Type to Strict
- B . Change Action under Action Settings to Alert
- C . Disable Dynamically Update Model
- D . Enable Bot Confirmation
D
Explanation:
Bot Confirmation
If the number of anomalies from a user has reached the Anomaly Count, the system executes Bot Confirmation before taking actions.
The Bot Confirmation is to confirm if the user is indeed a bot. The system sends RBE (Real Browser Enforcement) JavaScript or CAPTCHA to the client to double check if it’s a real bot.
Reference: https://docs.fortinet.com/document/fortiweb/6.3.1/administration-guide/600188/configuring-bot-detection-profiles
What can an administrator do if a client has been incorrectly period blocked?
- A . Nothing, it is not possible to override a period block.
- B . Manually release the ID address from the temporary blacklist.
- C . Force a new IP address to the client.
- D . Disconnect the client from the network.
B
Explanation:
Block Period
Enter the number of seconds that you want to block the requests. The valid range is 1C3,600 seconds. The default value is 60 seconds.
This option only takes effect when you choose Period Block in Action.
Note: That’s a temporary blacklist so you can manually release them from the blacklist.
Reference: https://docs.fortinet.com/document/fortiweb/6.3.1/administration-guide/600188/configuring-bot-detection-profiles
Which regex expression is the correct format for redirecting the URL http://www.example.com?
- A . www.example.com
- B . www.example.com
- C . wwwexamplecom
- D . www/.example/.com
B
Explanation:
Reference: https://learn.akamai.com/en-us/webhelp/edge-redirector/edge-redirector-guide/GUID-0C22DFC2-DCC4-42AF-BDB2-9537FBEE03FD.html
When FortiWeb triggers a redirect action, which two HTTP codes does it send to the client to inform the browser of the new URL? (Choose two.)
- A . 403
- B . 302
- C . 301
- D . 404
B, C
Explanation:
Reference: https://developer.mozilla.org/en-US/docs/Web/HTTP/Status/302
True transparent proxy mode is best suited for use in which type of environment?
- A . New networks where infrastructure is not yet defined
- B . Flexible environments where you can easily change the IP addressing scheme
- C . Small office to home office environments
- D . Environments where you cannot change the IP addressing scheme
B
Explanation:
"Because blocking is not guaranteed to succeed in offline mode, this mode is best used during the evaluation and planning phase, early in implementation. Reverse proxy is the most popular operating mode. It can rewrite URLs, offload TLS, load balance, and apply NAT. For very large MSSP, true transparent mode has a significant advantage. You can drop it in without changing any schemes of limited IPv4 spaceCin transparent mode, you don’t need to give IP addresses to the network interfaces on FortiWeb."
Review the following configuration:
What is the expected result of this configuration setting?
- A . When machine learning (ML) is in its collecting phase, FortiWeb will accept an unlimited number of samples from the same source IP address.
- B . When machine learning (ML) is in its running phase, FortiWeb will accept an unlimited number of samples from the same source IP address.
- C . When machine learning (ML) is in its collecting phase, FortiWeb will not accept any samples from any source IP addresses.
- D . When machine learning (ML) is in its running phase, FortiWeb will accept a set number of samples from the same source IP address.
Which two statements about the anti-defacement feature on FortiWeb are true? (Choose two.)
- A . Anti-defacement can redirect users to a backup web server, if it detects a change.
- B . Anti-defacement downloads a copy of your website to RAM, in order to restore a clean image, if it detects defacement.
- C . FortiWeb will only check to see if there are changes on the web server; it will not download the whole file each time.
- D . Anti-defacement does not make a backup copy of your databases.
C, D
Explanation:
Anti-defacement backs up web pages only, not databases.
If it detects any file changes, the FortiWeb appliance will download a new backup revision.
Reference: https://help.fortinet.com/fweb/551/Content/FortiWeb/fortiweb-admin/anti_defacement.htm
What must you do with your FortiWeb logs to ensure PCI DSS compliance?
- A . Store in an off-site location
- B . Erase them every two weeks
- C . Enable masking of sensitive data
- D . Compress them into a .zip file format
C
Explanation:
Reference: https://docplayer.net/8466775-Fortiweb-web-application-firewall-ensuring-compliance-for-pci-dss-requirement-6-6-solution-guide.html
What role does FortiWeb play in ensuring PCI DSS compliance?
- A . It provides the ability to securely process cash transactions.
- B . It provides the required SQL server protection.
- C . It provides the WAF required by PCI.
- D . It provides credit card processing capabilities.
Refer to the exhibit.
There is only one administrator account configured on FortiWeb .
What must an administrator do to restrict any brute force attacks that attempt to gain access to the FortiWeb management GUI?
- A . Delete the built-in administrator user and create a new one.
- B . Configure IPv4 Trusted Host # 3 with a specific IP address.
- C . The configuration changes must be made on the upstream device.
- D . Change the Access Profile to Read_Only.
B
Explanation:
Reference: https://docs.fortinet.com/document/fortiweb/6.1.1/administration-guide/397469/preventing-brute-force-logins
What key factor must be considered when setting brute force rate limiting and blocking?
- A . A single client contacting multiple resources
- B . Multiple clients sharing a single Internet connection
- C . Multiple clients from geographically diverse locations
- D . Multiple clients connecting to multiple resources
B
Explanation:
https://training.fortinet.com/course/view.php?id=3363 What is one key factor that you must consider when setting brute force rate limiting and blocking? Multiple clients sharing a single Internet connection