Which FortiMail option removes embedded code components in Microsoft Word, while maintaining the original file format?
- A . Behavior analysis
- B . Impersonation analysis
- C . Content disarm and reconstruction
- D . Header analysis
C
Explanation:
Reference: https://fortinetweb.s3.amazonaws.com/docs.fortinet.com/v2/attachments/8c063dd3-bafe-11e9-a989-00505692583a/fortimail-admin-620.pdf (435)
A FortiMail administrator is concerned about cyber criminals attempting to get sensitive information from employees using whaling phishing attacks.
What option can the administrator configure to prevent these types of attacks?
- A . Impersonation analysis
- B . Bounce tag verification
- C . Content disarm and reconstruction
- D . Dictionary profile with predefined smart identifiers
Which firmware upgrade method for an active-passive HA cluster ensures service outage is minimal, and there are no unnecessary failovers?
- A . Break the cluster, upgrade the units independently, and then form the cluster
- B . Upgrade both units at the same time
- C . Upgrade the standby unit, and then upgrade the active unit
- D . Upgrade the active unit, which will upgrade the standby unit automatically
B
Explanation:
Reference: https://docs.fortinet.com/document/fortimail/6.2.0/administration-guide/725928/upgrading-firmware-on-ha-units
Refer to the exhibit.
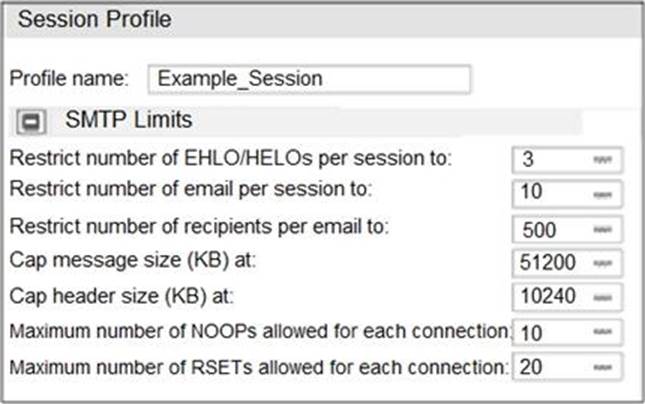
Which message size limit will FortiMail apply to the outbound email?
- A . 204800
- B . 1024
- C . 51200
- D . 10240
A FortiMail is configured with the protected domain example.com.
On this FortiMail, which two envelope addresses are considered incoming? (Choose two.)
- A . MAIL FROM: accounts@example.com RCPT TO: sales@external.org
- B . MAIL FROM: support@example.com RCPT TO: marketing@example.com
- C . MAIL FROM: training@external.org RCPT TO: students@external.org
- D . MAIL FROM: mis@hosted.net RCPT TO: noc@example.com
C,D
Explanation:
Reference: https://fortinetweb.s3.amazonaws.com/docs.fortinet.com/v2/attachments/9aa62d26-858d-11ea-9384-00505692583a/FortiMail-6.4.0-Administration_Guide.pdf (30)
What three configuration steps are required to enable DKIM signing for outbound messages on FortiMail? (Choose three.)
- A . Generate a public/private key pair in the protected domain configuration
- B . Enable DKIM check in a matching session profile
- C . Enable DKIM check in a matching antispam profile
- D . Publish the public key as a TXT record in a public DNS server
- E . Enable DKIM signing for outgoing messages in a matching session profile
Refer to the exhibit.
An administrator must enforce authentication on FML-1 for all outbound email from the example.com domain .
Which two settings should be used to configure the access receive rule? (Choose two.)
- A . The Recipient pattern should be set to *@example.com
- B . The Authentication status should be set to Authenticated
- C . The Sender IP/netmask should be set to 10.29.1.0/24
- D . The Action should be set to Reject
Which two CLI commands, if executed, will erase all data on the log disk partition? (Choose
two.)
- A . execute formatmaildisk
- B . execute formatmaildisk_backup
- C . execute formatlogdisk
- D . execute partitionlogdisk 40
C,D
Explanation:
Reference: https://docs.fortinet.com/document/fortimail/6.2.0/cli-reference/588825/formatlogdisk
Refer to the exhibit.
Which configuration change must you make to block an offending IP address temporarily?
- A . Add the offending IP address to the system block list
- B . Add the offending IP address to the user block list
- C . Add the offending IP address to the domain block list
- D . Change the authentication reputation setting status to Enable
D
Explanation:
Reference: https://help.fortinet.com/fweb/550/Content/FortiWeb/fortiweb-admin/blacklisting.htm
Which two antispam techniques query FortiGuard for rating information? (Choose two.)
- A . DNSBL
- B . SURBL
- C . IP reputation
- D . URI filter
A,B
Explanation:
Reference: https://docs.fortinet.com/document/fortimail/6.4.0/administration-guide/352990/configuring-antispam-profiles-and-antispam-action-profiles
If you are using the built-in MTA to process email in transparent mode, which two statements about FortiMail behavior are true? (Choose two.)
- A . MUAs need to be configured to connect to the built-in MTA to send email
- B . If you disable the built-in MTA, FortiMail will use its transparent proxies to deliver email
- C . FortiMail can queue undeliverable messages and generate DSNs
- D . FortiMail ignores the destination set by the sender, and uses its own MX record lookup to deliver email
While reviewing logs, an administrator discovers that an incoming email was processed using policy IDs 0:4:9.
Which two scenarios will generate this policy ID? (Choose two.)
- A . Email was processed using IP policy ID 4
- B . Incoming recipient policy ID 9 has the exclusive flag set
- C . FortiMail applies the default behavior for relaying inbound email
- D . FortiMail configuration is missing an access delivery rule
Refer to the exhibit.
Which two statements about email messages sent from User A to User B are correct? (Choose two.)
- A . User A’s MUA will perform a DNS MX record lookup to send the email message.
- B . mx.example1.org will forward the email message to the MX record that has the lowest preference.
- C . The DNS server will act as an intermediary MTA.
- D . User B will retrieve the email message using either POP3 or IMAP.
A FortiMail administrator is investigating a sudden increase in DSNs being delivered to the protected domain for undeliverable email messages. After searching the logs, the administrator identifies that the DSNs were not generated as a result of any outbound email sent from the protected domain.
Which FortiMail antispam technique can the administrator use to prevent this scenario?
- A . Spam outbreak protection
- B . Bounce address tag validation
- C . Spoofed header detection
- D . FortiGuard IP Reputation
A
Explanation:
Reference: https://docs.fortinet.com/document/fortimail/6.2.0/administration-guide/769204/managing-the-mail-queue
Refer to the exhibit.
Which two message types will trigger this DLP scan rule? (Choose two.)
- A . An email message with a subject that contains the term “credit card” will trigger this scan rule
- B . An email that contains credit card numbers in the body, attachment, and subject will trigger this scan rule
- C . An email message that contains credit card numbers in the body will trigger this scan rule
- D . An email sent from sales@internal.lab will trigger this scan rule, even without matching any conditions
An administrator sees that an excessive amount of storage space on a FortiMail device is being used up by quarantine accounts for invalid users. The FortiMail is operating in transparent mode.
Which two FortiMail features can the administrator configure to tackle this issue? (Choose two.)
- A . Automatic removal of quarantine accounts
- B . Recipient address verification
- C . Bounce address tag verification
- D . Sender address rate control
A,D
Explanation:
Reference:
https://fortinetweb.s3.amazonaws.com/docs.fortinet.com/v2/attachments/9aa62d26-858d-11ea-9384-00505692583a/FortiMail-6.4.0-Administration_Guide.pdf (322, 323)
Refer to the exhibit.
Which statement describes the pre-registered status of the IBE user extuser2@external.lab?
- A . The user has received an IBE notification email, but has not accessed the HTTPS URL
or attachment yet. - B . The user account has been de-activated, and the user must register again the next time they receive an IBE email.
- C . The user was registered by an administrator in anticipation of IBE participation.
- D . The user has completed the IBE registration process, but has not yet accessed their IBE email.
D
Explanation:
Reference: https://docs.fortinet.com/document/fortimail/6.4.2/administration-guide/470401/configuring-ibe-users
Refer to the exhibit.
MTA-1 is delivering an email intended for User 1 to MTA-2.
Which two statements about protocol usage between the devices are true? (Choose two.)
- A . User 1 will use logs were generated load the email message from MTA-2
- B . MTA-2 will use IMAP to receive the email message from MTA-1
- C . MTA-1 will use POP3 to deliver the email message to User 1 directly
- D . MTA-1 will use SMTP to deliver the email message to MTA-2
While testing outbound MTA functionality, an administrator discovers that all outbound email is being processed using policy IDs 1:2:0.
Which two reasons explain why the last policy ID value is 0? (Choose two.)
- A . Outbound email is being rejected
- B . IP policy ID 2 has the exclusive flag set
- C . There are no outgoing recipient policies configured
- D . There are no access delivery rules configured for outbound email
Refer to the exhibit.
For the transparent mode FortiMail shown in the exhibit, which two sessions are considered incoming sessions? (Choose two.)
- A . DESTINATION IP: 172.16.32.56 MAIL FROM: support@example.com RCPT TO: marketing@example.com
- B . DESTINATION IP: 192.168.54.10 MAIL FROM: accounts@example.com RCPT TO: sales@example.com
- C . DESTINATION IP: 10.25.32.15 MAIL FROM: training@example.com RCPT TO: students@external.com
- D . DESTINATION IP: 172.16.32.56 MAIL FROM: mis@hosted.net RCPT TO: noc@example.com