Fortinet NSE5_FAZ-6.4 Fortinet NSE 5 – FortiAnalyzer 6.4 Online Training
Fortinet NSE5_FAZ-6.4 Online Training
The questions for NSE5_FAZ-6.4 were last updated at Dec 24,2025.
- Exam Code: NSE5_FAZ-6.4
- Exam Name: Fortinet NSE 5 - FortiAnalyzer 6.4
- Certification Provider: Fortinet
- Latest update: Dec 24,2025
On the RAID management page, the disk status is listed as Initializing.
What does the status Initializing indicate about what the FortiAnalyzer is currently doing?
- A . FortiAnalyzer is ensuring that the parity data of a redundant drive is valid
- B . FortiAnalyzer is writing data to a newly added hard drive to restore it to an optimal state
- C . FortiAnalyzer is writing to all of its hard drives to make the array fault tolerant
- D . FortiAnalyzer is functioning normally
C
Explanation:
Reference: https://fortinetweb.s3.amazonaws.com/docs.fortinet.com/v2/attachments/4cb0dce6-dbef-11e9-8977-00505692583a/FortiAnalyzer-5.6.10-Administration-Guide.pdf (40)
What is the recommended method of expanding disk space on a FortiAnalyzer VM?
- A . From the VM host manager, add an additional virtual disk and use the #execute lvm extend <disk number> command to expand the storage
- B . From the VM host manager, expand the size of the existing virtual disk
- C . From the VM host manager, expand the size of the existing virtual disk and use the # execute format disk command to reformat the disk
- D . From the VM host manager, add an additional virtual disk and rebuild your RAID array
A
Explanation:
https://kb.fortinet.com/kb/documentLink.do?externalID=FD40848
On FortiAnalyzer, what is a wildcard administrator account?
- A . An account that permits access to members of an LDAP group
- B . An account that allows guest access with read-only privileges
- C . An account that requires two-factor authentication
- D . An account that validates against any user account on a FortiAuthenticator
A
Explanation:
https://docs.fortinet.com/document/fortigate/6.2.0/cookbook/747268/configuring-wildcard-admin-accounts
Consider the CLI command:

What is the purpose of the command?
- A . To add a unique tag to each log to prove that it came from this FortiAnalyzer
- B . To add the MD5 hash value and authentication code
- C . To add a log file checksum
- D . To encrypt log communications
C
Explanation:
https://docs.fortinet.com/document/fortianalyzer/6.2.5/cli-reference/849211/global
Which statements are true regarding securing communications between FortiAnalyzer and FortiGate with SSL? (Choose two.)
- A . SSL is the default setting.
- B . SSL communications are auto-negotiated between the two devices.
- C . SSL can send logs in real-time only.
- D . SSL encryption levels are globally set on FortiAnalyzer.
- E . FortiAnalyzer encryption level must be equal to, or higher than, FortiGate.
You need to upgrade your FortiAnalyzer firmware.
What happens to the logs being sent to FortiAnalyzer from FortiGate during the time FortiAnalyzer is temporarily unavailable?
- A . FortiAnalyzer uses log fetching to retrieve the logs when back online
- B . FortiGate uses the miglogd process to cache the logs
- C . The logfiled process stores logs in offline mode
- D . Logs are dropped
What statements are true regarding FortiAnalyzer ‘s treatment of high availability (HA)
dusters? (Choose two)
- A . FortiAnalyzer distinguishes different devices by their serial number.
- B . FortiAnalyzer receives logs from d devices in a duster.
- C . FortiAnalyzer receives bgs only from the primary device in the cluster.
- D . FortiAnalyzer only needs to know (he serial number of the primary device in the cluster-it automaticaly discovers the other devices.
What can you do on FortiAnalyzer to restrict administrative access from specific locations?
- A . Configure trusted hosts for that administrator.
- B . Enable geo-location services on accessible interface.
- C . Configure two-factor authentication with a remote RADIUS server.
- D . Configure an ADOM for respective location.
A
Explanation:
Reference: https://docs.fortinet.com/document/fortigate/6.2.0/hardening-your-fortigate/582009/system-administrator-best-practices
View the exhibit.
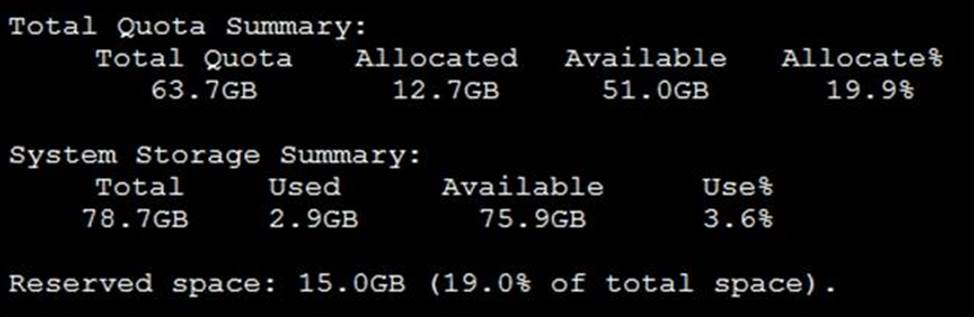
Why is the total quota less than the total system storage?
- A . 3.6% of the system storage is already being used.
- B . Some space is reserved for system use, such as storage of compression files, upload files, and temporary report files
- C . The oftpd process has not archived the logs yet
- D . The logfiled process is just estimating the total quota
B
Explanation:
https://docs.fortinet.com/document/fortianalyzer/6.2.5/administration-guide/368682/disk-space-allocation
Which log type does the FortiAnalyzer indicators of compromise feature use to identify infected hosts?
- A . Antivirus logs
- B . Web filter logs
- C . IPS logs
- D . Application control logs
B
Explanation:
Reference: https://help.fortinet.com/fa/faz50hlp/60/6-0-2/Content/FortiAnalyzer_Admin_Guide/3600_FortiView/0200_Using_FortiView/1200_Compromised_hosts_page.htm?TocPath=FortiView%7CUsing%20FortiView%7C_____6
Latest NSE5_FAZ-6.4 Dumps Valid Version with 86 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund

