Fortinet NSE5_FAZ-6.2 Fortinet NSE 5 – FortiAnalyzer 6.2 Online Training
Fortinet NSE5_FAZ-6.2 Online Training
The questions for NSE5_FAZ-6.2 were last updated at Dec 21,2025.
- Exam Code: NSE5_FAZ-6.2
- Exam Name: Fortinet NSE 5 - FortiAnalyzer 6.2
- Certification Provider: Fortinet
- Latest update: Dec 21,2025
By default, what happens when a log file reaches its maximum file size?
- A . FortiAnalyzer overwrites the log files.
- B . FortiAnalyzer stops logging.
- C . FortiAnalyzer rolls the active log by renaming the file.
- D . FortiAnalyzer forwards logs to syslog.
Which statements are correct regarding FortiAnalyzer reports? (Choose two)
- A . FortiAnalyzer provides the ability to create custom reports.
- B . FortiAnalyzer glows you to schedule reports to run.
- C . FortiAnalyzer includes pre-defined reports only.
- D . FortiAnalyzer allows reporting for FortiGate devices only.
Refer to the exhibit.
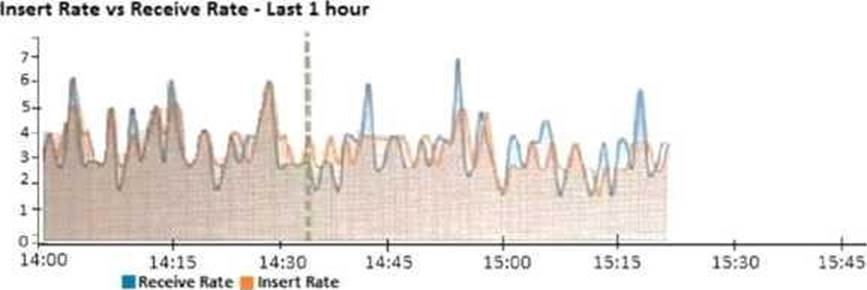
What does the data point at 14:55 tell you?
- A . The received rate is almost at its maximum for this device
- B . The sqlplugind daemon is behind in log indexing by two logs
- C . Logs are being dropped
- D . Raw logs are reaching FortiAnalyzer faster than they can be indexed
On FortiAnalyzer, what is a wildcard administrator account?
- A . An account that permits access to members of an LDAP group
- B . An account that allows guest access with read-only privileges
- C . An account that requires two-factor authentication
- D . An account that validates against any user account on a FortiAuthenticator
How does FortiAnalyzer retrieve specific log data from the database?
- A . SQL FROM statement
- B . SQL GET statement
- C . SQL SELECT statement
- D . SQL EXTRACT statement
For which two purposes would you use the command set log checksum? (Choose two.)
- A . To help protect against man-in-the-middle attacks during log upload from FortiAnalyzer to an SFTP server
- B . To prevent log modification or tampering
- C . To encrypt log communications
- D . To send an identical set of logs to a second logging server
A,B
Explanation:
To prevent the log in the store from being modified, you can add a log checksum by using the config system global command. When the log is split, archived, and the log is uploaded (if the feature is enabled), you can configure the FortiAnalyzer to log the log file hash value, timestamp, and authentication code. This can help defend against man-in-the-middle attacks when uploading log transmission data from the
FortiAnalyzer to the SFTP server.
FortiAnalyzer uses the Optimized Fabric Transfer Protocok (OFTP) over SSL for what purpose?
- A . To upload logs to an SFTP server
- B . To prevent log modification during backup
- C . To send an identical set of logs to a second logging server
- D . To encrypt log communication between devices
What remote authentication servers can you configure to validate your FortiAnalyzer administrator logons? (Choose three)
- A . RADIUS
- B . Local
- C . LDAP
- D . PKI
- E . TACACS+
What is the purpose of employing RAID with FortiAnalyzer?
- A . To introduce redundancy to your log data
- B . To provide data separation between ADOMs
- C . To separate analytical and archive data
- D . To back up your logs
Logs are being deleted from one of the ADOMs earlier than the configured setting for archiving in the data policy.
What is the most likely problem?
- A . CPU resources are too high
- B . Logs in that ADOM are being forwarded, in real-time, to another FortiAnalyzer device
- C . The total disk space is insufficient and you need to add other disk
- D . The ADOM disk quota is set too low, based on log rates
D
Explanation:
Reference: https://help.fortinet.com/fmgr/50hlp/56/5-6-1/FMG-FAZ/1100_Storage/0017_Deleted%20device%20logs.htm
Latest NSE5_FAZ-6.2 Dumps Valid Version with 65 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund

