Fortinet NSE4_FGT-7.2 Fortinet NSE 4 – FortiOS 7.2 Online Training
Fortinet NSE4_FGT-7.2 Online Training
The questions for NSE4_FGT-7.2 were last updated at Dec 22,2025.
- Exam Code: NSE4_FGT-7.2
- Exam Name: Fortinet NSE 4 - FortiOS 7.2
- Certification Provider: Fortinet
- Latest update: Dec 22,2025
Which statement correctly describes the use of reliable logging on FortiGate?
- A . Reliable logging is enabled by default in all configuration scenarios.
- B . Reliable logging is required to encrypt the transmission of logs.
- C . Reliable logging can be configured only using the CLI.
- D . Reliable logging prevents the loss of logs when the local disk is full.
A team manager has decided that, while some members of the team need access to a particular website, the majority of the team does not.
Which configuration option is the most effective way to support this request?
- A . Implement a web filter category override for the specified website
- B . Implement a DNS filter for the specified website.
- C . Implement web filter quotas for the specified website
- D . Implement web filter authentication for the specified website.
Which two statements ate true about the Security Fabric rating? (Choose two.)
- A . It provides executive summaries of the four largest areas of security focus.
- B . Many of the security issues can be fixed immediately by clicking Apply where available.
- C . The Security Fabric rating must be run on the root FortiGate device in the Security Fabric.
- D . The Security Fabric rating is a free service that comes bundled with alt FortiGate devices.
Refer to the exhibit.
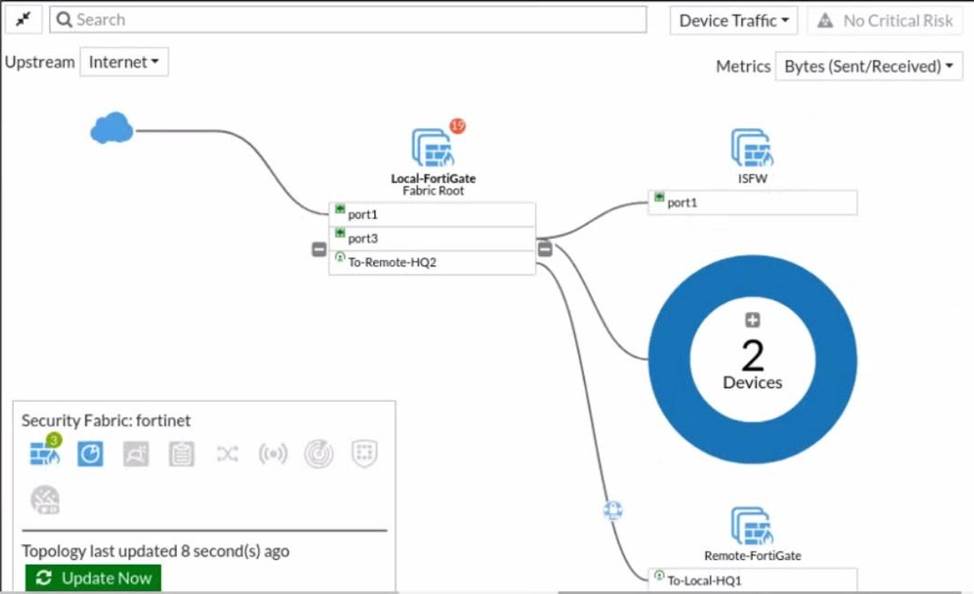
Given the security fabric topology shown in the exhibit, which two statements are true? (Choose two.)
- A . There are five devices that are part of the security fabric.
- B . Device detection is disabled on all FortiGate devices.
- C . This security fabric topology is a logical topology view.
- D . There are 19 security recommendations for the security fabric.
Refer to the exhibit.
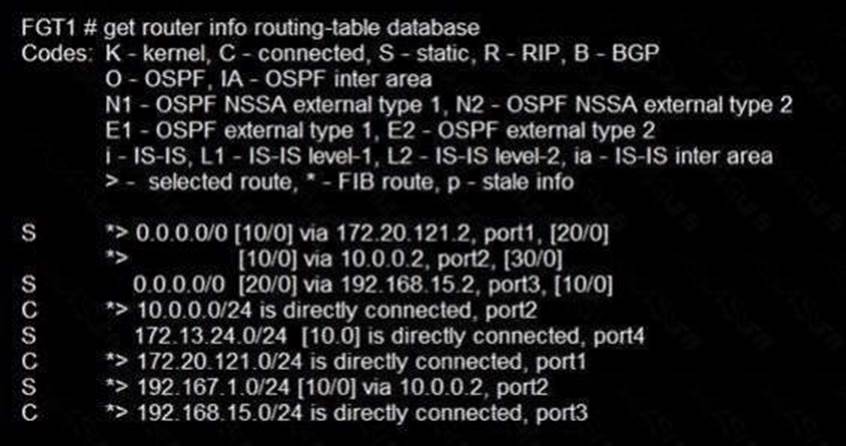
Given the routing database shown in the exhibit, which two statements are correct? (Choose two.)
- A . The port3 default route has the highest distance.
- B . The port3 default route has the lowest metric.
- C . There will be eight routes active in the routing table.
- D . The port1 and port2 default routes are active in the routing table.
An organization’s employee needs to connect to the office through a high-latency internet connection.
Which SSL VPN setting should the administrator adjust to prevent the SSL VPN negotiation failure?
- A . Change the session-ttl.
- B . Change the login timeout.
- C . Change the idle-timeout.
- D . Change the udp idle timer.
Which two statements are true about the RPF check? (Choose two.)
- A . The RPF check is run on the first sent packet of any new session.
- B . The RPF check is run on the first reply packet of any new session.
- C . The RPF check is run on the first sent and reply packet of any new session.
- D . RPF is a mechanism that protects FortiGate and your network from IP spoofing attacks.
Refer to the exhibit.
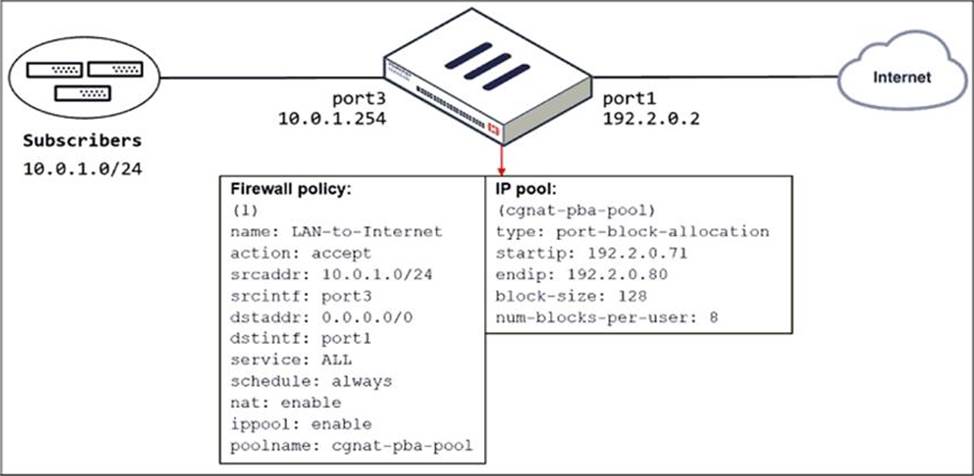
The exhibit shows a diagram of a FortiGate device connected to the network and the firewall policy and IP pool configuration on the FortiGate device.
Which two actions does FortiGate take on internet traffic sourced from the subscribers? (Choose two.)
- A . FortiGate allocates port blocks per user, based on the configured range of internal IP addresses.
- B . FortiGate allocates port blocks on a first-come, first-served basis.
- C . FortiGate generates a system event log for every port block allocation made per user.
- D . FortiGate allocates 128 port blocks per user.
You have enabled logging on your FortiGate device for Event logs and all Security logs, and you have set up logging to use the FortiGate local disk.
What is the default behavior when the local disk is full?
- A . Logs are overwritten and the only warning is issued when log disk usage reaches the threshold of 95%.
- B . No new log is recorded until you manually clear logs from the local disk.
- C . Logs are overwritten and the first warning is issued when log disk usage reaches the threshold of 75%.
- D . No new log is recorded after the warning is issued when log disk usage reaches the threshold of 95%.
Latest NSE4_FGT-7.2 Dumps Valid Version with 154 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund

