Fortinet NSE4_FGT-7.2 Fortinet NSE 4 – FortiOS 7.2 Online Training
Fortinet NSE4_FGT-7.2 Online Training
The questions for NSE4_FGT-7.2 were last updated at Dec 12,2025.
- Exam Code: NSE4_FGT-7.2
- Exam Name: Fortinet NSE 4 - FortiOS 7.2
- Certification Provider: Fortinet
- Latest update: Dec 12,2025
Examine the exhibit, which contains a virtual IP and firewall policy configuration.
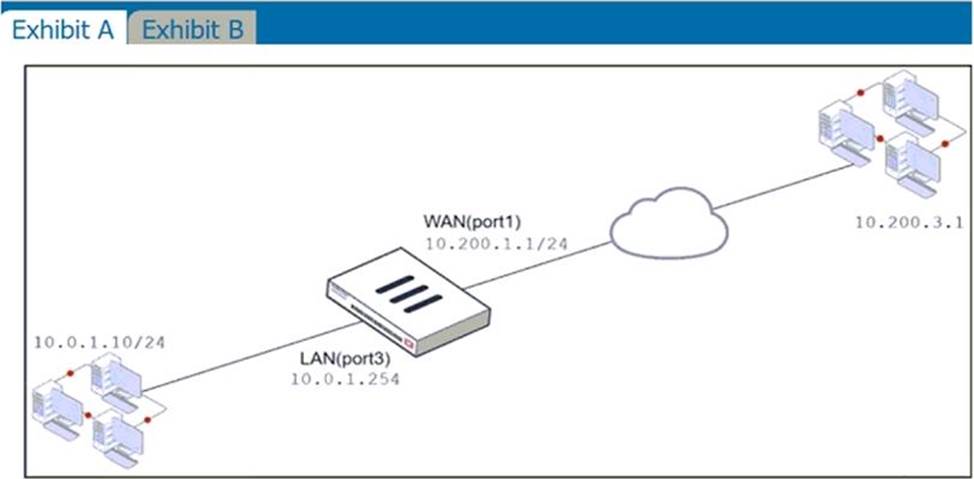
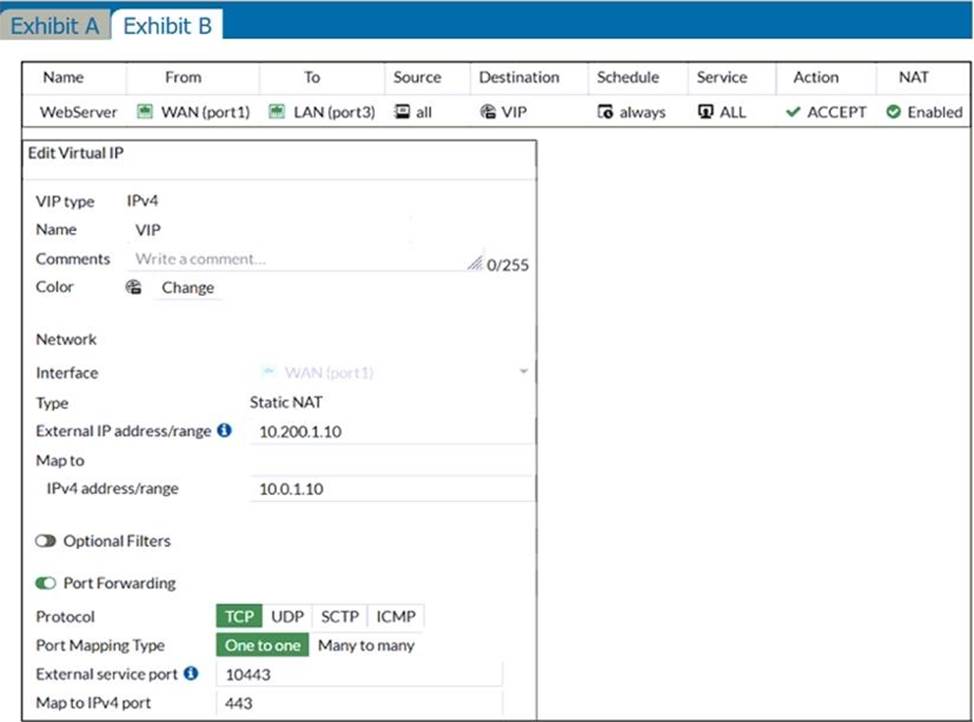
The WAN (port1) interface has the IP address 10.200. 1. 1/24. The LAN (port2) interface has the IP address 10.0. 1.254/24.
The first firewall policy has NAT enabled on the outgoing interface address. The second firewall policy is configured with a VIP as the destination address.
Which IP address will be used to source NAT the Internet traffic coming from a workstation with the IP address 10.0.1.10/24?
- A . 10.200. 1. 10
- B . Any available IP address in the WAN (port1) subnet 10.200. 1.0/24 66 of 108
- C . 10.200. 1. 1
- D . 10.0. 1.254
Which three statements are true regarding session-based authentication? (Choose three.)
- A . HTTP sessions are treated as a single user.
- B . IP sessions from the same source IP address are treated as a single user.
- C . It can differentiate among multiple clients behind the same source IP address.
- D . It requires more resources.
- E . It is not recommended if multiple users are behind the source NAT
Which of the following conditions must be met in order for a web browser to trust a web server certificate signed by a third-party CA?
- A . The public key of the web server certificate must be installed on the browser.
- B . The web-server certificate must be installed on the browser.
- C . The CA certificate that signed the web-server certificate must be installed on the browser.
- D . The private key of the CA certificate that signed the browser certificate must be installed on the browser.
An administrator must disable RPF check to investigate an issue.
Which method is best suited to disable RPF without affecting features like antivirus and intrusion prevention system?
- A . Enable asymmetric routing, so the RPF check will be bypassed.
- B . Disable the RPF check at the FortiGate interface level for the source check.
- C . Disable the RPF check at the FortiGate interface level for the reply check .
- D . Enable asymmetric routing at the interface level.
Which feature in the Security Fabric takes one or more actions based on event triggers?
- A . Fabric Connectors
- B . Automation Stitches
- C . Security Rating
- D . Logical Topology
Refer to the exhibit.
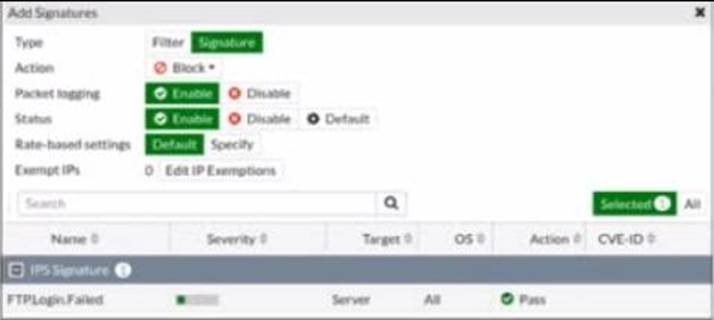
Review the Intrusion Prevention System (IPS) profile signature settings.
Which statement is correct in adding the FTP.Login.Failed signature to the IPS sensor profile?
- A . The signature setting uses a custom rating threshold.
- B . The signature setting includes a group of other signatures.
- C . Traffic matching the signature will be allowed and logged.
- D . Traffic matching the signature will be silently dropped and logged.
Which two statements are correct regarding FortiGate FSSO agentless polling mode? (Choose two.)
- A . FortiGate points the collector agent to use a remote LDAP server.
- B . FortiGate uses the AD server as the collector agent.
- C . FortiGate uses the SMB protocol to read the event viewer logs from the DCs.
- D . FortiGate queries AD by using the LDAP to retrieve user group information.
Refer to the exhibits to view the firewall policy (Exhibit A) and the antivirus profile (Exhibit B).
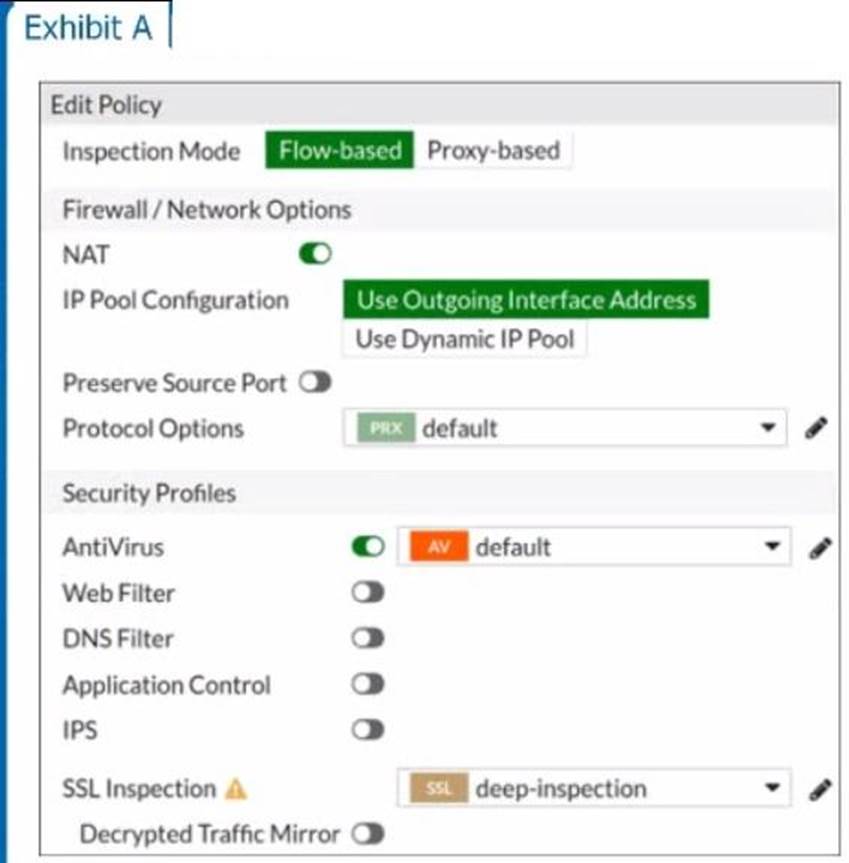
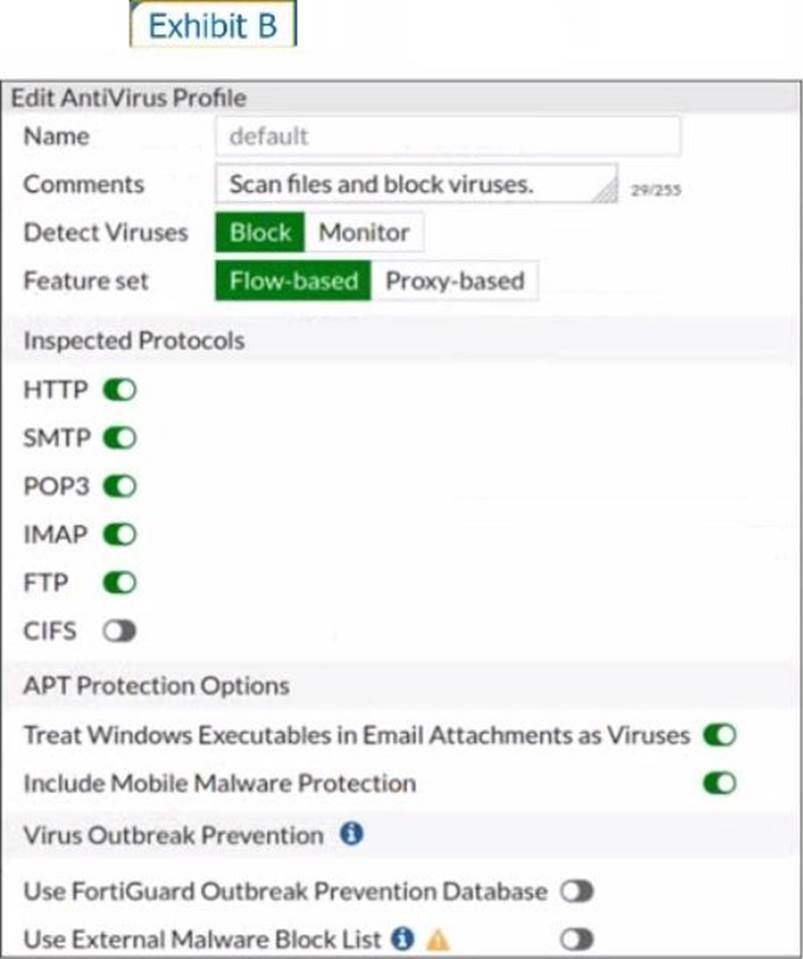
Which statement is correct if a user is unable to receive a block replacement message when downloading an infected file for the first time?
- A . The firewall policy performs the full content inspection on the file.
- B . The flow-based inspection is used, which resets the last packet to the user.
- C . The volume of traffic being inspected is too high for this model of FortiGate.
- D . The intrusion prevention security profile needs to be enabled when using flow-based inspection mode.
The HTTP inspection process in web filtering follows a specific order when multiple features are enabled in the web filter profile.
What order must FortiGate use when the web filter profile has features enabled, such as safe search?
- A . DNS-based web filter and proxy-based web filter
- B . Static URL filter, FortiGuard category filter, and advanced filters
- C . Static domain filter, SSL inspection filter, and external connectors filters
- D . FortiGuard category filter and rating filter
Refer to the exhibit.
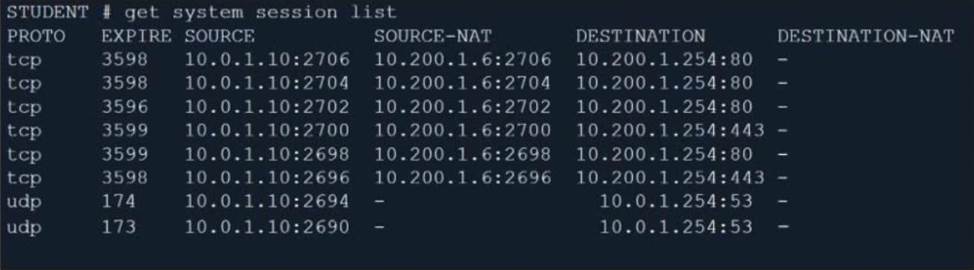
Which contains a session list output. Based on the information shown in the exhibit, which statement is true?
- A . Destination NAT is disabled in the firewall policy.
- B . One-to-one NAT IP pool is used in the firewall policy.
- C . Overload NAT IP pool is used in the firewall policy.
- D . Port block allocation IP pool is used in the firewall policy.
Latest NSE4_FGT-7.2 Dumps Valid Version with 154 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund

