Fortinet NSE4_FGT-7.2 Fortinet NSE 4 – FortiOS 7.2 Online Training
Fortinet NSE4_FGT-7.2 Online Training
The questions for NSE4_FGT-7.2 were last updated at Dec 25,2025.
- Exam Code: NSE4_FGT-7.2
- Exam Name: Fortinet NSE 4 - FortiOS 7.2
- Certification Provider: Fortinet
- Latest update: Dec 25,2025
Which of the following statements is true regarding SSL VPN settings for an SSL VPN portal?
- A . By default, FortiGate uses WINS servers to resolve names.
- B . By default, the SSL VPN portal requires the installation of a client’s certificate.
- C . By default, split tunneling is enabled.
- D . By default, the admin GUI and SSL VPN portal use the same HTTPS port.
Refer to exhibit.
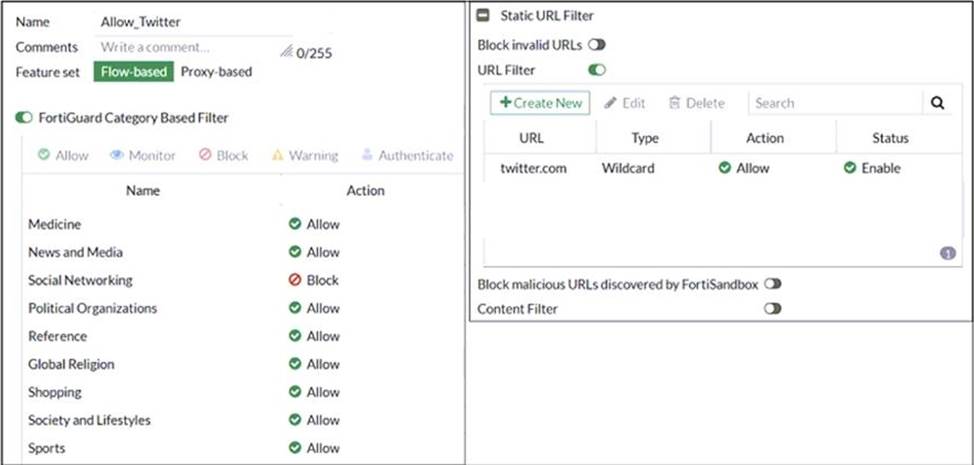
An administrator configured the web filtering profile shown in the exhibit to block access to all social networking sites except Twitter. However, when users try to access twitter.com, they are redirected to a FortiGuard web filtering block page.
Based on the exhibit, which configuration change can the administrator make to allow Twitter while blocking all other social networking sites?
- A . On the FortiGuard Category Based Filter configuration, set Action to Warning for
Social Networking - B . On the Static URL Filter configuration, set Type to Simple
- C . On the Static URL Filter configuration, set Action to Exempt.
- D . On the Static URL Filter configuration, set Action to Monitor.
Which two inspection modes can you use to configure a firewall policy on a profile-based next-generation firewall (NGFW)? (Choose two.)
- A . Proxy-based inspection
- B . Certificate inspection
- C . Flow-based inspection
- D . Full Content inspection
Which two statements about FortiGate FSSO agentless polling mode are true? (Choose two.)
- A . FortiGate uses the AD server as the collector agent.
- B . FortiGate uses the SMB protocol to read the event viewer logs from the DCs.
- C . FortiGate does not support workstation check .
- D . FortiGate directs the collector agent to use a remote LDAP server.
When configuring a firewall virtual wire pair policy, which following statement is true?
- A . Any number of virtual wire pairs can be included, as long as the policy traffic direction is the same.
- B . Only a single virtual wire pair can be included in each policy.
- C . Any number of virtual wire pairs can be included in each policy, regardless of the policy traffic direction settings.
- D . Exactly two virtual wire pairs need to be included in each policy.
When configuring a firewall virtual wire pair policy, which following statement is true?
- A . Any number of virtual wire pairs can be included, as long as the policy traffic direction is the same.
- B . Only a single virtual wire pair can be included in each policy.
- C . Any number of virtual wire pairs can be included in each policy, regardless of the policy traffic direction settings.
- D . Exactly two virtual wire pairs need to be included in each policy.
What two changes can the administrator make to resolve the issue without affecting any existing services running through FortiGate? (Choose two.)
- A . Create a new firewall policy with the new HTTP service and place it above the existing HTTP policy.
- B . Create a new service object for HTTP service and set the session TTL to never
- C . Set the TTL value to never under config system-ttl
- D . Set the session TTL on the HTTP policy to maximum
Which two protocol options are available on the CLI but not on the GUI when configuring an SD-WAN Performance SLA? (Choose two.)
- A . DNS
- B . ping
- C . udp-echo
- D . TWAMP
Refer to the exhibits.
The exhibits show the firewall policies and the objects used in the firewall policies.
The administrator is using the Policy Lookup feature and has entered the search criteria shown in the exhibit.
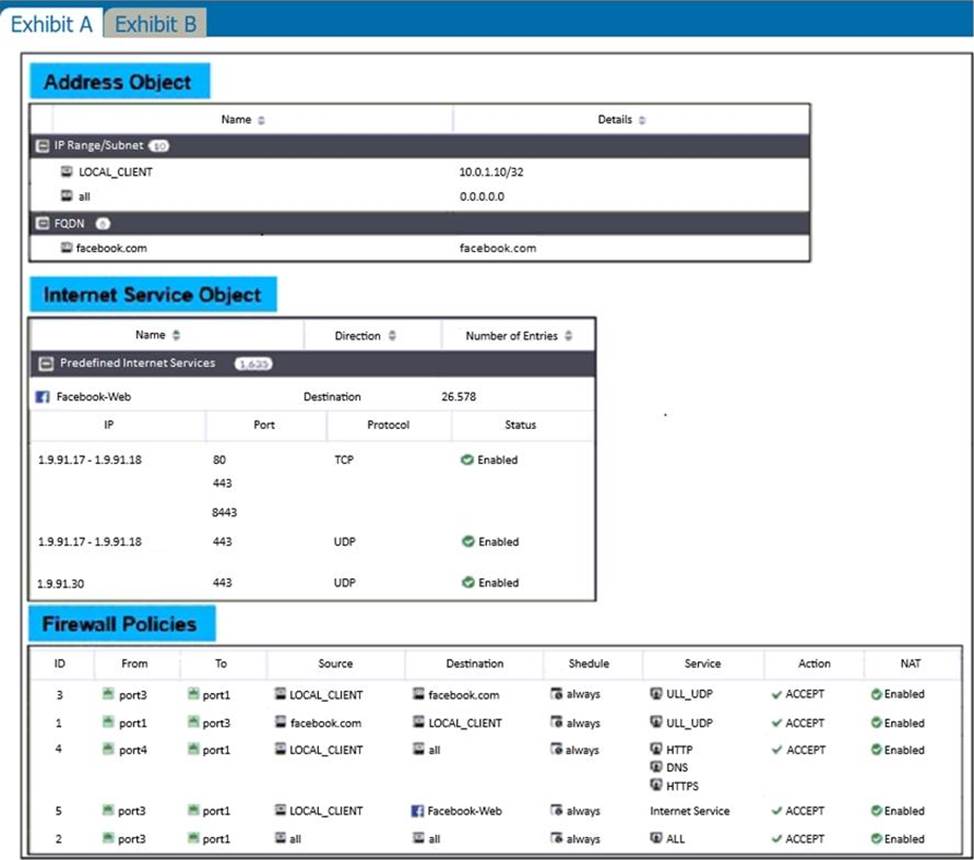
Which policy will be highlighted, based on the input criteria?
- A . Policy with ID 4.
- B . Policy with ID 5.
- C . Policies with ID 2 and 3.
- D . Policy with ID 4.
In an explicit proxy setup, where is the authentication method and database configured?
- A . Proxy Policy
- B . Authentication Rule
- C . Firewall Policy
- D . Authentication scheme
Latest NSE4_FGT-7.2 Dumps Valid Version with 154 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund

