Fortinet NSE4_FGT-7.0 Fortinet NSE 4 – FortiOS 7.0 Online Training
Fortinet NSE4_FGT-7.0 Online Training
The questions for NSE4_FGT-7.0 were last updated at Dec 22,2025.
- Exam Code: NSE4_FGT-7.0
- Exam Name: Fortinet NSE 4 - FortiOS 7.0
- Certification Provider: Fortinet
- Latest update: Dec 22,2025
An administrator has configured a strict RPF check on FortiGate.
Which statement is true about the strict RPF check?
- A . The strict RPF check is run on the first sent and reply packet of any new session.
- B . Strict RPF checks the best route back to the source using the incoming interface.
- C . Strict RPF checks only for the existence of at cast one active route back to the source using the incoming interface.
- D . Strict RPF allows packets back to sources with all active routes.
B
Explanation:
Reference: https://kb.fortinet.com/kb/documentLink.do?externalID=FD33955
Which two configuration settings are synchronized when FortiGate devices are in an active-active HA cluster? (Choose two.)
- A . FortiGuard web filter cache
- B . FortiGate hostname
- C . NTP
- D . DNS
An administrator has configured the following settings:
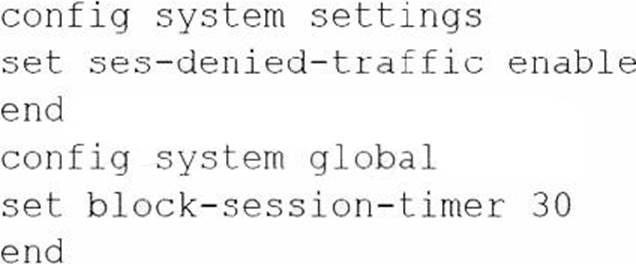
What are the two results of this configuration? (Choose two.)
- A . Device detection on all interfaces is enforced for 30 minutes.
- B . Denied users are blocked for 30 minutes.
- C . A session for denied traffic is created.
- D . The number of logs generated by denied traffic is reduced.
C,D
Explanation:
Reference: https://kb.fortinet.com/kb/documentLink.do?externalID=FD46328
Which three options are the remote log storage options you can configure on FortiGate? (Choose three.)
- A . FortiCache
- B . FortiSIEM
- C . FortiAnalyzer
- D . FortiSandbox
- E . FortiCloud
B,C,E
Explanation:
Reference: https://docs.fortinet.com/document/fortigate/6.0.0/handbook/265052/logging-and-reporting-overview
Which statement about video filtering on FortiGate is true?
- A . Full SSL Inspection is not required.
- B . It is available only on a proxy-based firewall policy.
- C . It inspects video files hosted on file sharing services.
- D . Video filtering FortiGuard categories are based on web filter FortiGuard categories.
B
Explanation:
Reference: https://docs.fortinet.com/document/fortigate/7.0.0/new-features/190873/video-filtering
Which two statements about FortiGate FSSO agentless polling mode are true? (Choose two.)
- A . FortiGate uses the AD server as the collector agent.
- B . FortiGate uses the SMB protocol to read the event viewer logs from the DCs.
- C . FortiGate does not support workstation check.
- D . FortiGate directs the collector agent to use a remote LDAP server.
B,D
Explanation:
Reference: https://kb.fortinet.com/kb/documentLink.do?externalID=FD47732
Refer to the exhibit showing a debug flow output.
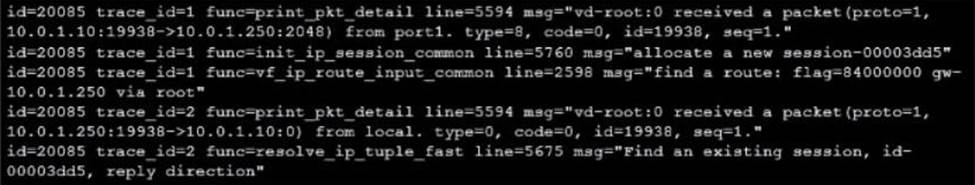
Which two statements about the debug flow output are correct? (Choose two.)
- A . The debug flow is of ICMP traffic.
- B . A firewall policy allowed the connection.
- C . A new traffic session is created.
- D . The default route is required to receive a reply.
A,C
Explanation:
Reference: https://docs.fortinet.com/document/fortigate/6.2.3/cookbook/54688/debugging-the-packet-flow
A network administrator wants to set up redundant IPsec VPN tunnels on FortiGate by using two IPsec VPN tunnels and static routes.
* All traffic must be routed through the primary tunnel when both tunnels are up
* The secondary tunnel must be used only if the primary tunnel goes down
* In addition, FortiGate should be able to detect a dead tunnel to speed up tunnel failover
Which two key configuration changes are needed on FortiGate to meet the design requirements? (Choose two,)
- A . Configure a high distance on the static route for the primary tunnel, and a lower distance on the static route for the secondary tunnel.
- B . Enable Dead Peer Detection.
- C . Configure a lower distance on the static route for the primary tunnel, and a higher distance on the static route for the secondary tunnel.
- D . Enable Auto-negotiate and Autokey Keep Alive on the phase 2 configuration of both tunnels.
B,C
Explanation:
B – because the customer requires the tunnels to notify when a tunnel goes down. DPD is designed for that purpose. To send a packet over a firewall to determine a failover for the next tunnel after a specific amount of time of not receiving a response from its peer.
C – remember when it comes to choosing a route with regards to Administrative Distance. The route with the lowest distance for that particular route will be chosen. So, by configuring a lower routing distance on the primary tunnel, means that the primary tunnel
will be chosen to route packets towards their destination.
Refer to the exhibits to view the firewall policy (Exhibit A) and the antivirus profile (Exhibit B).
Exhibit A.
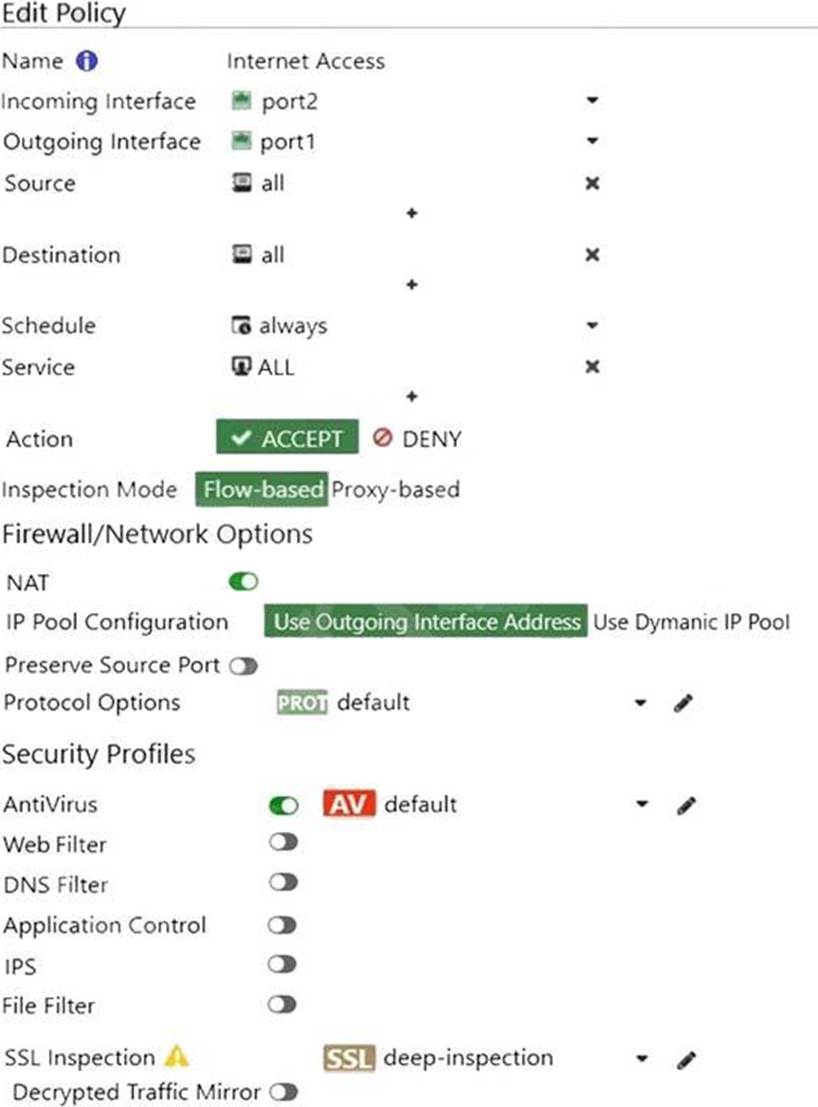
Exhibit B.
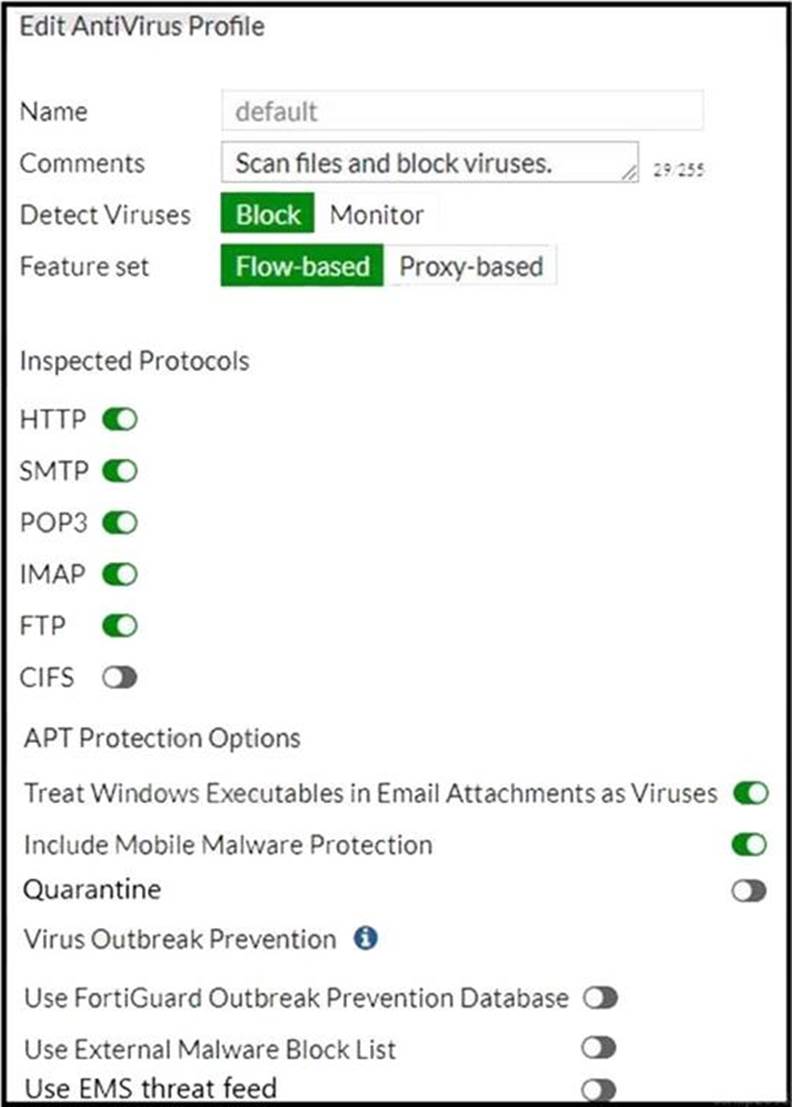
Which statement is correct if a user is unable to receive a block replacement message when downloading an infected file for the first time?
- A . The firewall policy performs the full content inspection on the file.
- B . The flow-based inspection is used, which resets the last packet to the user.
- C . The volume of traffic being inspected is too high for this model of FortiGate.
- D . The intrusion prevention security profile needs to be enabled when using flow-based inspection mode.
B
Explanation:
• "ONLY" If the virus is detected at the "START" of the connection, the IPS engine sends the block replacement message immediately
• When a virus is detected on a TCP session (FIRST TIME), but where "SOME PACKETS" have been already forwarded to the receiver, FortiGate "resets the connection" and does not send the last piece of the file. Although the receiver got most of the file content, the file has been truncated and therefore, can’t be opened. The IPS engine also caches the URL of the infected file, so that if a "SECOND ATTEMPT" to transmit the file is made, the IPS engine will then send a block replacement message to the client instead of scanning the file again.
In flow mode, the FortiGate drops the last packet killing the file. But because of that the block replacement message cannot be displayed. If the file is attempted to download again the block message will be shown.
Refer to the exhibits.
Exhibit A.
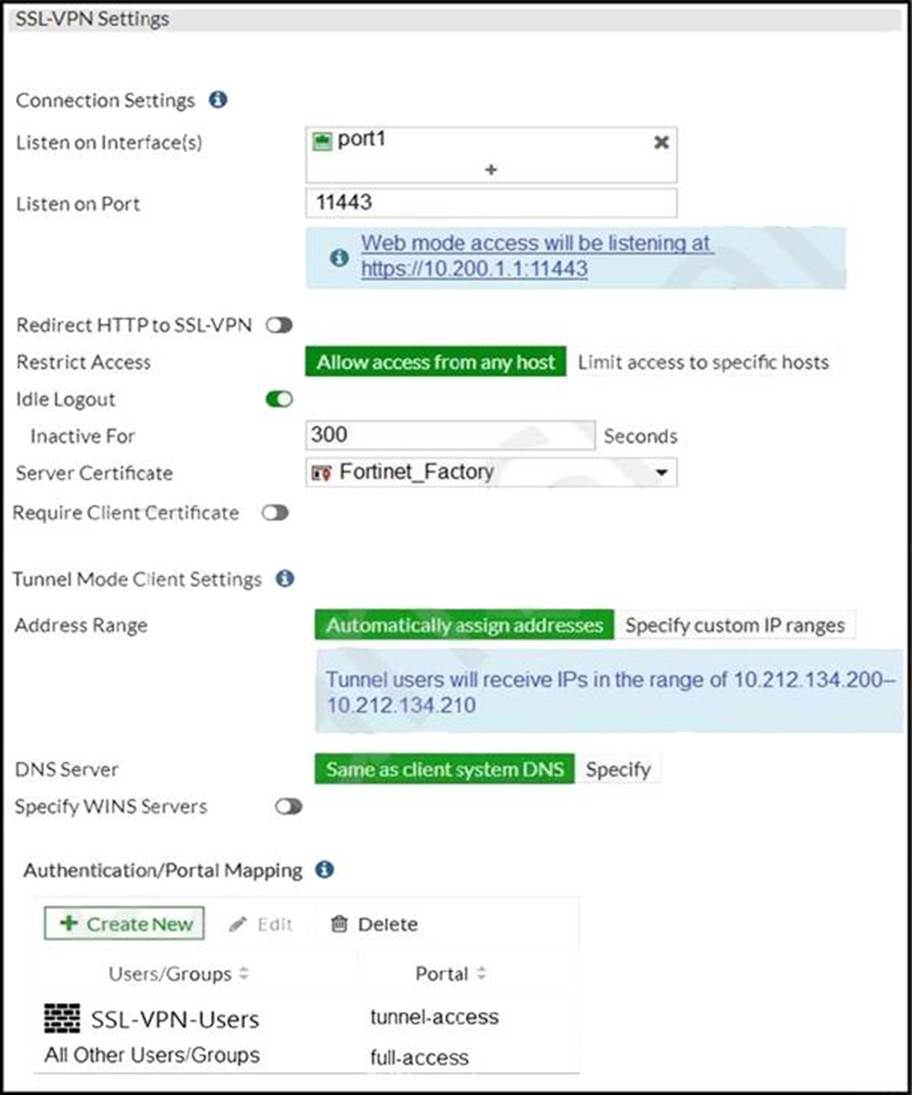
Exhibit B.
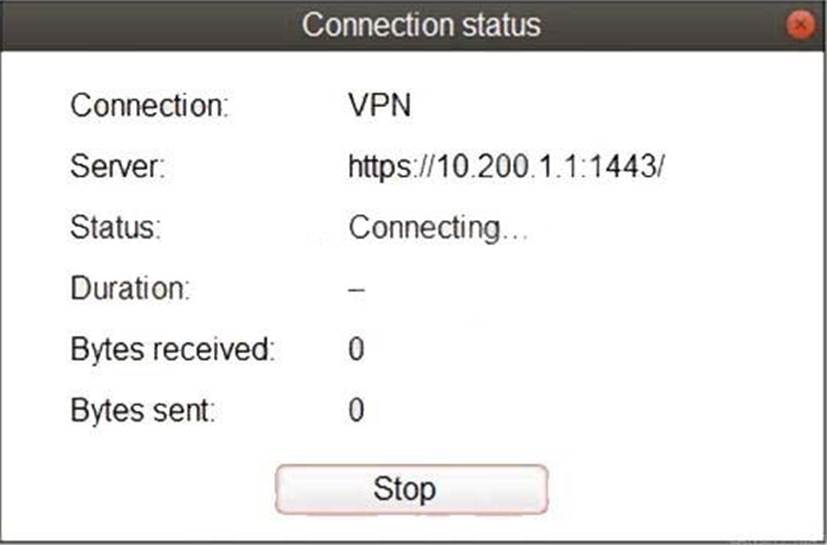
The SSL VPN connection fails when a user attempts to connect to it.
What should the user do to successfully connect to SSL VPN?
- A . Change the SSL VPN port on the client.
- B . Change the Server IP address.
- C . Change the idle-timeout.
- D . Change the SSL VPN portal to the tunnel.
A
Explanation:
Reference: https://docs.fortinet.com/document/fortigate/5.4.0/cookbook/150494
Latest NSE4_FGT-7.0 Dumps Valid Version with 172 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund

