Fortinet NSE4_FGT-6.4 Fortinet NSE 4 – FortiOS 6.4 Online Training
Fortinet NSE4_FGT-6.4 Online Training
The questions for NSE4_FGT-6.4 were last updated at Apr 12,2025.
- Exam Code: NSE4_FGT-6.4
- Exam Name: Fortinet NSE 4 - FortiOS 6.4
- Certification Provider: Fortinet
- Latest update: Apr 12,2025
An administrator needs to increase network bandwidth and provide redundancy.
What interface type must the administrator select to bind multiple FortiGate interfaces?
- A . VLAN interface
- B . Software Switch interface
- C . Aggregate interface
- D . Redundant interface
C
Explanation:
Reference: https://forum.fortinet.com/tm.aspx?m=120324
Which CLI command will display sessions both from client to the proxy and from the proxy to the servers?
- A . diagnose wad session list
- B . diagnose wad session list | grep hook-pre&&hook-out
- C . diagnose wad session list | grep hook=pre&&hook=out
- D . diagnose wad session list | grep "hook=pre"&"hook=out"
What types of traffic and attacks can be blocked by a web application firewall (WAF) profile? (Choose three.)
- A . Traffic to botnetservers
- B . Traffic to inappropriate web sites
- C . Server information disclosure attacks
- D . Credit card data leaks
- E . SQL injection attacks
If Internet Service is already selected as Source in a firewall policy, which other configuration objects can be added to the Source filed of a firewall policy?
- A . IP address
- B . Once Internet Service is selected, no other object can be added
- C . User or User Group
- D . FQDN address
Refer to the exhibit.
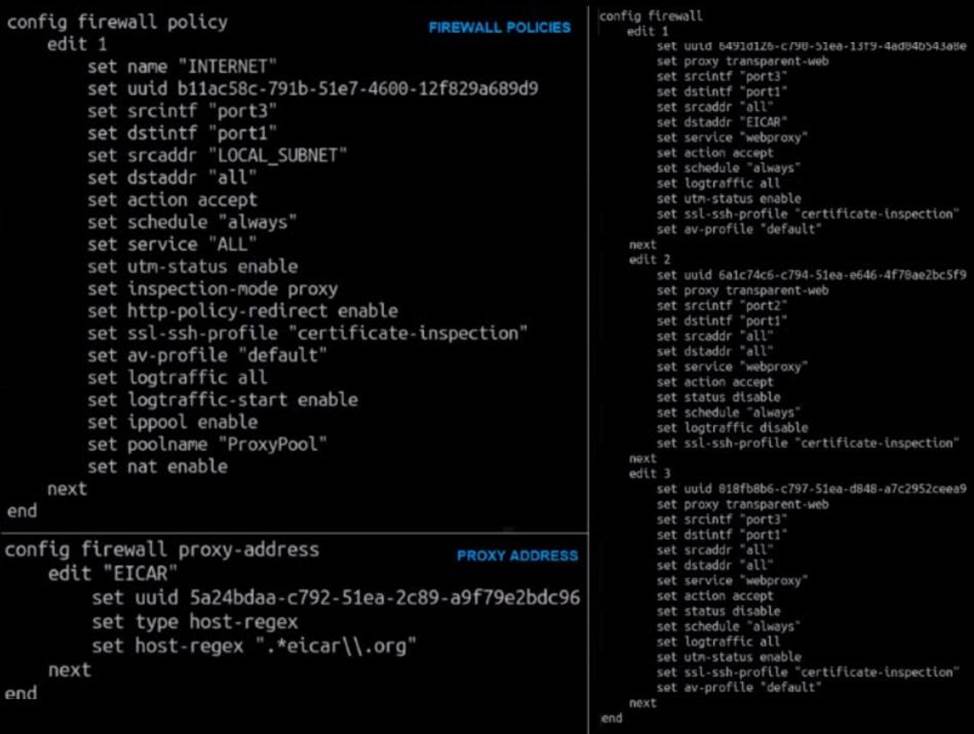
The exhibit shows a CLI output of firewall policies, proxy policies, and proxy addresses.
How does FortiGate process the traffic sent to http://www.fortinet.com?
- A . Traffic will be redirected to the transparent proxy and it will be allowed by proxy policy ID 3.
- B . Traffic will not be redirected to the transparent proxy and it will be allowed by firewall policy ID 1.
- C . Traffic will be redirected to the transparent proxy and It will be allowed by proxy policy ID 1.
- D . Traffic will be redirected to the transparent proxy and it will be denied by the proxy implicit deny policy.
Refer to the exhibit to view the firewall policy.
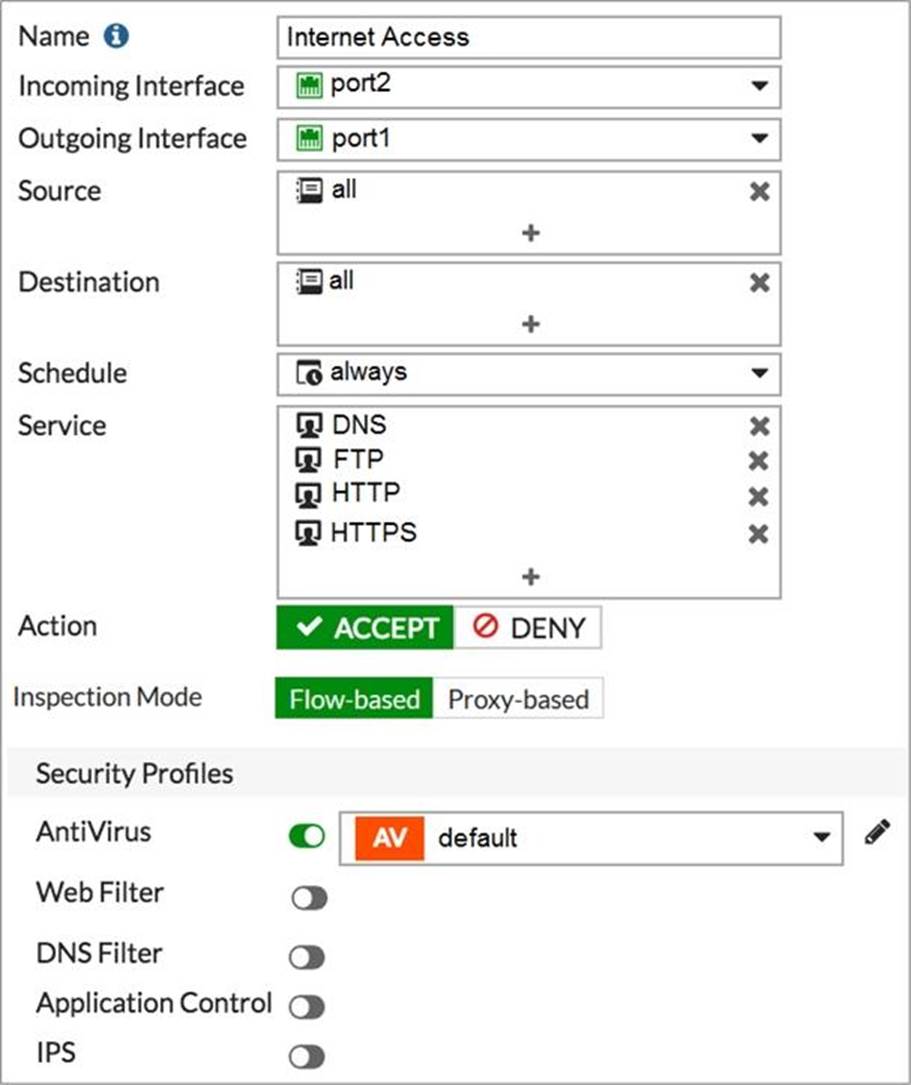
Which statement is correct if well-known viruses are not being blocked?
- A . The firewall policy does not apply deep content inspection.
- B . The firewall policy must be configured in proxy-based inspection mode.
- C . The action on the firewall policy must be set to deny.
- D . Web filter should be enabled on the firewall policy to complement the antivirus profile.
Which two protocols are used to enable administrator access of a FortiGate device? (Choose two.)
- A . SSH
- B . HTTPS
- C . FTM
- D . FortiTelemetry
A,B
Explanation:
Reference: https://docs.fortinet.com/document/fortigate/6.4.0/hardening-your-fortigate/995103/buildingsecurity-into-fortios
Refer to the exhibit.
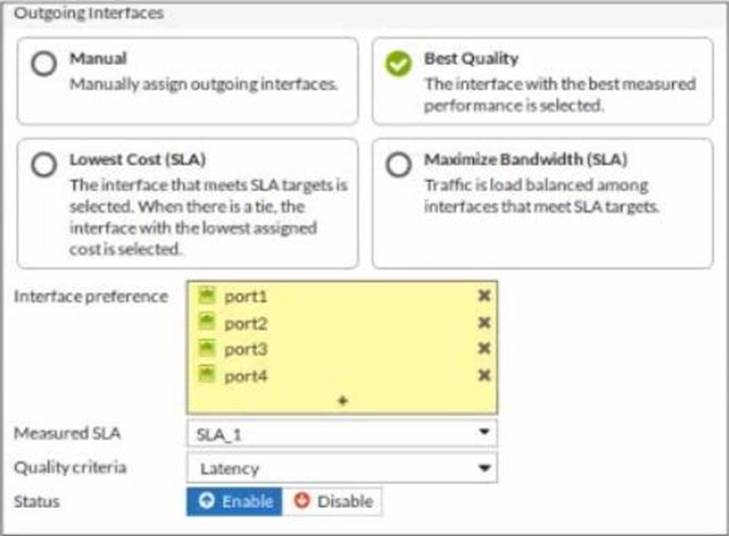
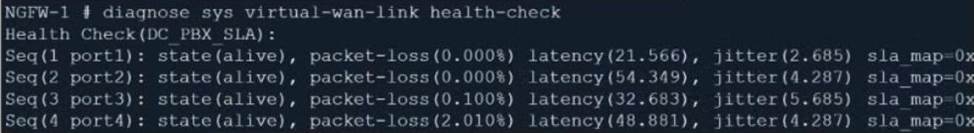
The exhibit contains the configuration for an SD-WAN Performance SLA, as well as the output of diagnose sys virtual-wan-link health-check.
Which interface will be selected as an outgoing interface?
- A . port2
- B . port4
- C . port3
- D . port1
Which statement regarding the firewall policy authentication timeout is true?
- A . It is an idle timeout. The FortiGate considers a user to be “idle” if it does not see any packets coming from the user’s source IP.
- B . It is a hard timeout. The FortiGate removes the temporary policy for a user’s source IP address after this timer has expired.
- C . It is an idle timeout. The FortiGate considers a user to be “idle” if it does not see any packets coming from the user’s source MAC.
- D . It is a hard timeout. The FortiGate removes the temporary policy for a user’s source MAC address after this timer has expired.
Which of the following statements about central NAT are true? (Choose two.)
- A . IP tool references must be removed from existing firewall policies before enabling central NAT.
- B . Central NAT can be enabled or disabled from the CLI only.
- C . Source NAT, using central NAT, requires at least one central SNAT policy.
- D . Destination NAT, using central NAT, requires a VIP object as the destination address in a firewall.
Latest NSE4_FGT-6.4 Dumps Valid Version with 142 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund

