Fortinet NSE4_FGT-6.2 Fortinet NSE 4 – FortiOS 6.2 Online Training
Fortinet NSE4_FGT-6.2 Online Training
The questions for NSE4_FGT-6.2 were last updated at Dec 26,2025.
- Exam Code: NSE4_FGT-6.2
- Exam Name: Fortinet NSE 4 - FortiOS 6.2
- Certification Provider: Fortinet
- Latest update: Dec 26,2025
Examine the two static routes shown in the exhibit, then answer the following question
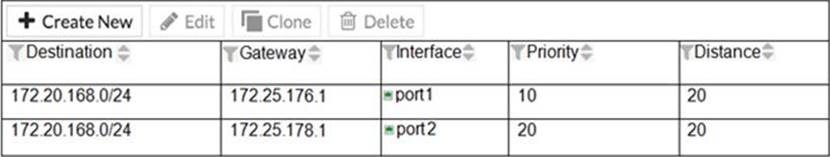
Which of the following is the expected FortiGate behavior regarding these two routes to the same destination?
- A . FortiGate will load balance all traffic across both routes.
- B . FortiGate will use the port1 route as the primary candidate
- C . FortiGate will route twice as much traffic to the port2 route
- D . FortiGate will only actuate the port1 route in the routing table
Examine the exhibit, which shows the partial output of an IKE real-time debug.
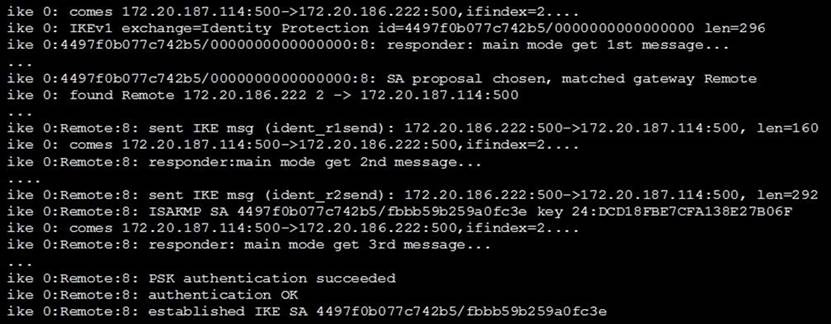
Which of the following statement about the output is true?
- A . The VPN is configured to use pre-shared key authentication.
- B . Extended authentication (XAuth) was successful
- C . Remote is the host name of the remote lPsec peer.
- D . Phase 1went down.
How can you block or allow to Twitter using a firewall policy?
- A . Configure the Destination field as Internet Service objects for Twitter
- B . Configure the Action field as Learn and select Twitter.
- C . Configure the Service field as Internet Service objects for Twitter
- D . Configure the source field as Internet Service objects for Twitter
When browsing to an internal web server using a web-mode SSL VPN bookmark, which IP address is used as the source of the HTTP request?
- A . remote user’s public IPaddress
- B . The public IP address of the FortiGate device.
- C . The remote user’s virtual lP address.
- D . The internal IP address of the FortiGate device.
Which of the following services can be inspected by the DLP profile? (Choose three.)
- A . NFS
- B . FTP
- C . IMAP
- D . CIFS
- E . HTTP-POST
A company needs to provide SSL VPN access to two user groups. The company also needs to display different welcome messages on the SSL VPN login screen for both user groups.
What is required in the SSL VPN configuration to meet these requirements?
- A . Different SSL VPN realms for each group
- B . Two separate SSL VPNs in different interfaces mapping the same ss root
- C . Two firewall policies with different captive portals
- D . Different virtual SSL VPN IP addresses for each group.
The FSSO Collector Agent set to advanced access mode for the Windows Active Directory uses which of the following?
- A . LDAP convention
- B . NTLM convention
- C . Windows convention – NetBiosUsername
- D . RSSO convention
NGFW mode allows policy-based configuration for most inspection rules. Which security profile’s configuration does not change when you enable policy-based inspection?
- A . Web filtering
- B . Antivirus
- C . Web proxy
- D . Application control
Which of the following statements are true when using WPAD with the DHCP discovery method? (Choose two.)
- A . If the DHCP method fails, browsers will try the DNS method.
- B . The browser needs to be preconfigured with the DHCP server’s IP address
- C . The browser sends a DHCPONFORM request to the DHCP server.
- D . The DHCP server provides the PAC file for download
What is the limitation of using a URL list and application control on the same firewall policy, in NGFW policy-based mode?
- A . It limits the scope of application control to the browser-based technology category only
- B . It limits the scope of application control to scan application traffic based on application category only.
- C . It limits the scope of application control to scan application traffic using parent signatures only.
- D . It limits the scope of application control to scan application traffic on DNS protocol only.
Latest NSE4_FGT-6.2 Dumps Valid Version with 120 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund

