Fortinet NSE4_FGT-6.2 Fortinet NSE 4 – FortiOS 6.2 Online Training
Fortinet NSE4_FGT-6.2 Online Training
The questions for NSE4_FGT-6.2 were last updated at Dec 29,2025.
- Exam Code: NSE4_FGT-6.2
- Exam Name: Fortinet NSE 4 - FortiOS 6.2
- Certification Provider: Fortinet
- Latest update: Dec 29,2025
Which configuration objects can be selected for the Source field of a firewall policy? (Choose two.)
- A . Firewall service
- B . User or user group
- C . IP Pool
- D . FQDN address
By default, when logging to disk, when does FortiGate delete logs?
- A . 30 days
- B . 1 year
- C . Never
- D . 7 days
Which of the following conditions are required for establishing an IP Sec VPN between two FortiGate devices? (Choose two)
- A . If XAuth is enabled as a server in one peer, it must be enabled as a client in the other peer
- B . If the VPN is configured as route-based, there must be at least one firewall policy with the action set to IP Sec
- C . If the VPN is configured as Dial Up User in one peer, it must be configured as either Static IP Address or Dynamic DNS in the other peer.
- D . If the VPN is configured as a policy-based in one peer, it must also be configured as policy based in the other peer.
Based on this output, which statements are correct? (Choose two.)
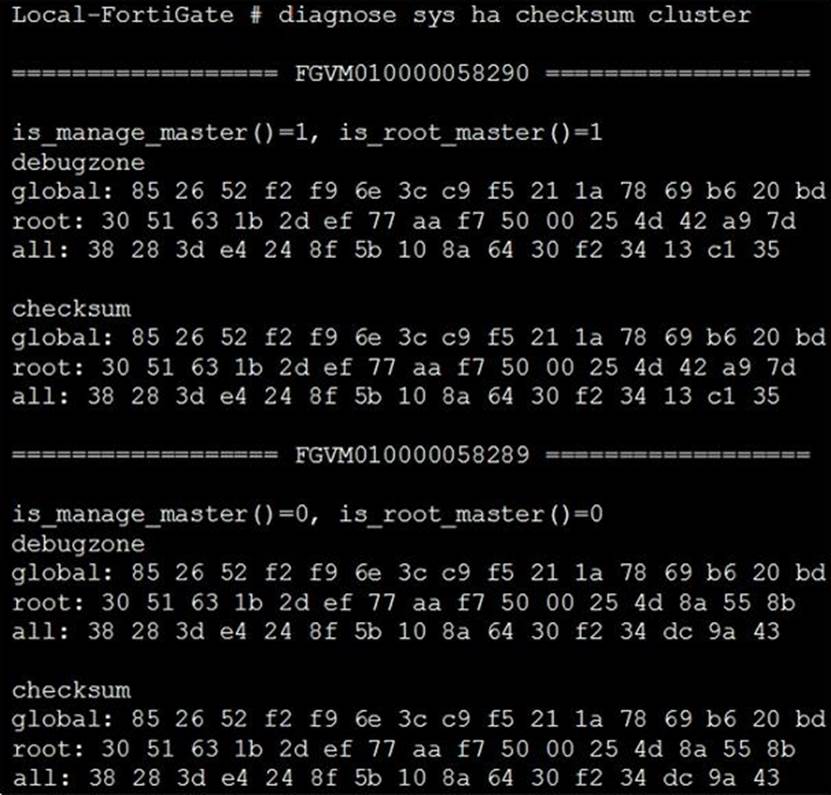
- A . The all V DOM is not synchronized between the primary and secondary FortiGate devices
- B . The root V DOM is not synchronized between the primary and secondary FortiGate devices
- C . The global configuration is synchronized between the primary and secondary FortiGate devices
- D . The FortiGate devices have three V DOMS
Which of the following statements about NTLM authentication are correct? (Choose two.)
- A . It is useful when users login to DCs that are not monitored by a collector agent
- B . It takes over as the primary authentication method when configured alongside FS SO.
- C . Multidomain environments require DC agents on every domain controller.
- D . NTLM-enabled web browsers are required.
Refer to the exhibit.
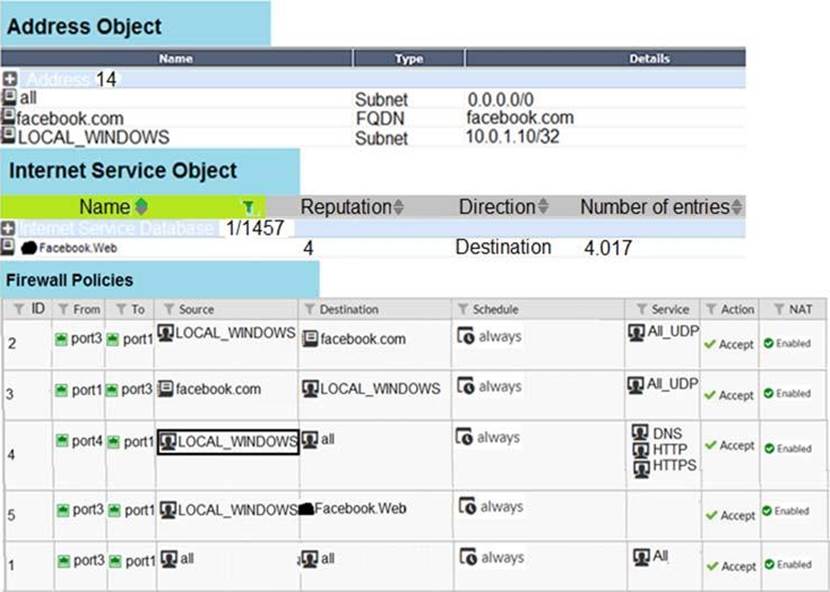
The exhibits show the firewall policies and the objects used in the firewall policies.
The administrator is using the Policy Lookup feature and has entered the search criteria shown in the exhibit.
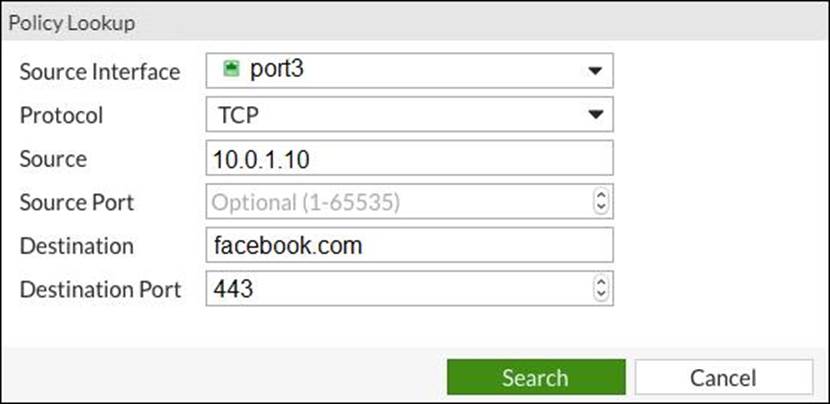
Which of the following will be highlighted based on the input criteria?
- A . Policy with 1
- B . Policies with ID 2 and 3
- C . Policy with ID 5
- D . Policy with ID 4
An administrator is attempting to allow access to https://fortinet. com through a firewall policy that is configured with a webfilter and an SSL inspection profile configured for deep inspection which of the following are possible actions to eliminate the certificate error generated by deep inspection? (Choose Two)
- A . Implement firewall authentication for all users that need access to fortinet.com
- B . Manually install the FortiGate deep inspection certificate as a trusted CA
- C . Configure fortinet.com access to bypass the IPS engine
- D . Configure an SSL-inspection exemption for fortinet.com
An administrator has configured a dialup IPsec VPN with XAuth.
Which statement best describes what occurs during this scenario?
- A . Phase 1 negotiations will skip preshared key exchange.
- B . Only digital certificates will be accepted as an authentication method in phase 1.
- C . Dialup clients must provide a username and password for authentication
- D . Dialup clients must provide their localID during phase 2 negotiations
What are the expected actions if traffic matches this IPS sensor? (Choose two)
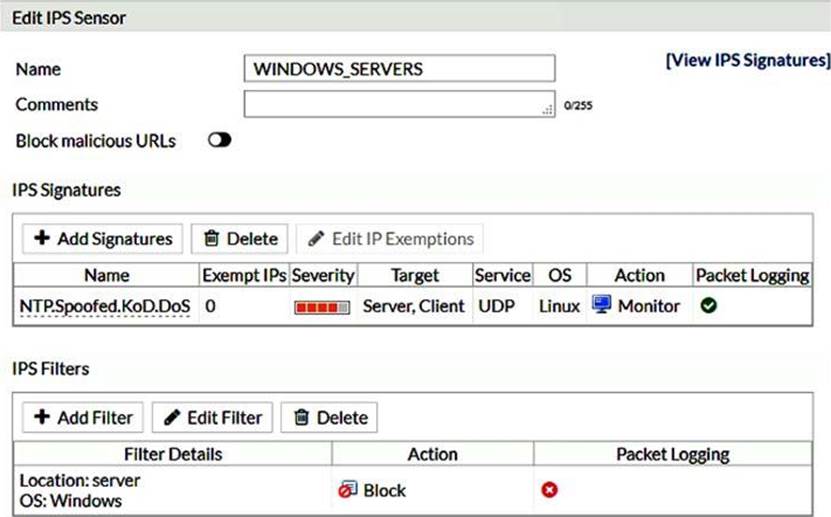
- A . The sensor will gather a packet log for all matched traffic
- B . The sensor will not block attackers matching the A32S. Botnet signature
- C . The sensor will block all attacks for Windows Servers
- D . The sensor will reset all connections that match these signatures
An administrator has configured the following settings
config system settings
set ses-denied-traffic enable end
config system global
set block-session-timer 30 end
What does the configuration do? (Choose two)
- A . Reduces the amount of logs generated by denied traffic
- B . Enforces device detection on all interfaces for 30 minutes
- C . Blocks denied users for 30 minutes
- D . Creates a session for traffic being denied
Latest NSE4_FGT-6.2 Dumps Valid Version with 120 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund

